We would like to point out that if you have a Linux system you need to take care of and want to sleep comfortably, you should have taken the precautions we recommend below.
Have a general security policy
You should create a security policy, although it is not very detailed about what the authority limits of your system and users are. It would be very beneficial to have precise limits on what cannot, can be done or where the limit of which user profile ends without your permission. If you do not deal with the Authorization process in the use of Linux and start granting “root” for the definitive solution, you may have a headache.
Physical System Security
You must make sure that your system is physically secured. I’m not just talking about locking the door. For example, it is a good idea to restrict the system from booting to devices such as USB, CD in the BIOS settings. Although the Boot Password is not used much, it allows you to protect the BIOS settings.

Choose to Use SSH
Logging in with SSH requires the use of the pub key. As such, you are protected as much as possible from Brute Force-style password cracking attacks. When you take some time to use ssh and become familiar with it, you will see that it is quite safe.

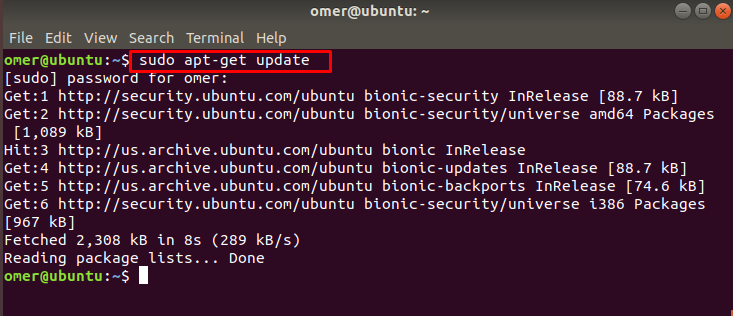
Update Your System
If you wait tomorrow to update your system, you may be late. If you do not do the operation with a few lines of commands, you may be in a very difficult situation.
Your Open Ports are like your Home’s Open window
The data flow of your system is done through the ports. It is very useful to check open ports with the help of the netstat command. After a while, you will be familiar with which service uses which port. Remember, attackers don’t break into your system to get things done and exit within 5 minutes. Usually, they get authorization and start visiting frequently. Ports provide very useful information for you to detect.

ROOT user
Sometimes you may want to do the fastest. Logging in as root can also be very tempting. You have to think again. For this, forget to log in with the ROOT user.
What do system log files do?
The log files in your Linux system are produced for the administrator and users to read and review. A healthy Linux notifies you with log files on issues it is disturbing. Be sure to learn to check records and don’t let go.
Backup
It will be very classic advice, but it still doesn’t hurt to say it. Backup is very important. Back up your system. One recommendation for backing up is password protected. Store your backup files with password protection. Unprotected backup files can cause major vulnerabilities.
Are you using IPv6?
Turn it off if you are not currently using IPv6. There is no need to have something open on your system that you are not using. In some distributions, if IPv6, which is turned on by default, is not turned off, malicious people send malicious packets over IPv6. System administrators generally do not follow IPv6.
SSH Banner
You can notify users who connect to your system with ssh about small warnings and important announcements using the ssh banner. In fact, it is a very good method for creating user awareness.
Closing unnecessary services
There is no need to say much about it. You install and try many programs. Then you don’t uninstall or stop it. Turn off unnecessary ones. Bluetooth for example.
SELinux
We recommend using SELinux for your security policies. Some distributions use AppArmor, but by default, it is in permissive mode. You should do research and have information on this subject.

Less Program, Less Vulnerability
It is a very effective approach to remove programs you do not need on your system. There is no need to keep some programs installed on your system even if you do not use them once a month. When required to use, it is possible to install and run it with one or two commands in a simple way. The fewer programs installed, the fewer vulnerabilities you will have.




