One of the features used for authorization in Windows is User Account Control (UAC) protection. UAC is used to control some operations performed by the user.
Control: User account audit and approval mechanism for authorized users should be operated.
Precaution: For the specified control substance, the measures that can be taken can be listed as follows.
The necessary settings for user account auditing can be performed with the Group Policy Object as follows:
1.Group Policy Security Options
Here we go to Security Options from Group Policy settings. The options under Security Options contain user-related security policies.

`Computer Configuration` –> Windows Settings –> Security Settings –> Local Policies –> Security Options

User Account Control: Admin Approval Mode for the Built-in Administrator account
The built-in administrator account logs on in Admin Approval Mode so that any operation that requires elevation of privilege displays a prompt that provides the administrator with the option to permit or deny the elevation of privilege.
- `User Account Control`: Admin Approval Mode for the Built-in Administrator account –> Enabled

User Account Control: Allow UIAccess applications to prompt for elevation without using the secure desktop
This check verifies whether User Interface Accessibility programs can automatically disable the secure desktop for elevation prompts for a standard user.
User Account Control: Allow UIAccess applications to prompt for elevation without using the secure desktop –> Disabled

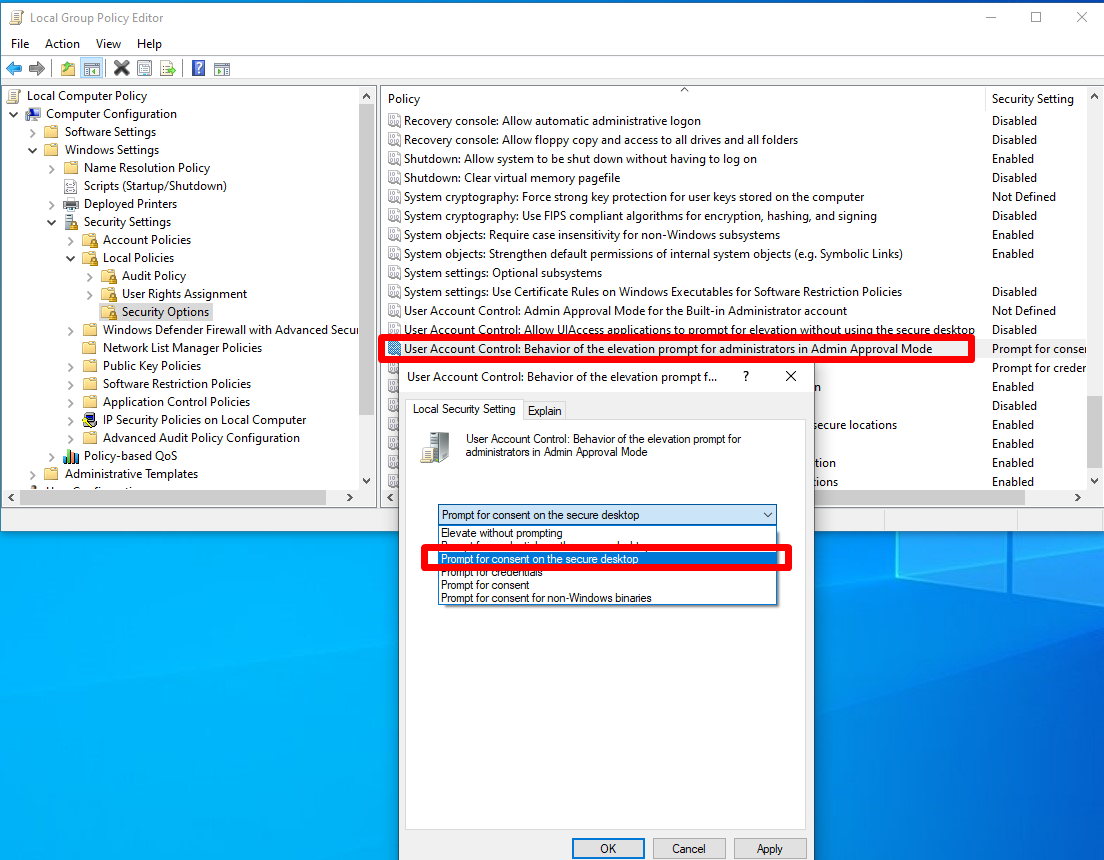
User Account Control: Behavior of the elevation prompt for administrators in Admin Approval Mode
When an operation requires elevation of privilege, the user is prompted on the secure desktop to select Permit or Deny. If the user selects Permit, the operation continues with the user’s highest available privilege.
- `User Account Control`: Behavior of the elevation prompt for administrators in Admin Approval Mode –> Prompt for consent on the secure desktop
User Account Control: Behavior of the elevation prompt for standard users
This policy setting determines the behavior of the elevation prompt for standard users.
- `User Account Control`: Behavior of the elevation prompt for standard users –> Automatically deny elevation requests

User Account Control: Detect application installations and prompt for elevation
This policy setting determines the behavior of application installation detection for the entire system. Some software might attempt to install itself after being given permission to run. The user may give permission for the program to run because the program is trusted. Then the user is prompted to install an unknown component. This security policy provides another way to identify and stop these attempted software installations before they can do damage.
- `User Account Control`: Detect application installations and prompt for elevation –> Enabled

User Account Control: Only elevate UIAccess applications that are installed in secure locations
This policy setting enforces the requirement that apps that request running with a UIAccess integrity level (by means of marking of UIAccess=true in their app manifest), must reside in a secure location on the file system. Relatively secure locations are limited to the following directories.
- \Program Files\ including subdirectories
- \Windows\system32\
- \Program Files (x86)\ including subdirectories for 64-bit versions of Windows
- `User Account Control`: Only elevate UIAccess applications that are installed in secure locations –> Enabled

User Account Control: Run all administrators in Admin Approval Mode
This policy setting determines the behavior of all User Account Control (UAC) policies for the entire system. This is the setting that turns UAC on or off.
- `User Account Control`: Run all administrators in Admin Approval Mode –> Enabled

User Account Control: Switch to the secure desktop when prompting for elevation
This policy setting determines whether the elevation request prompts on the interactive user desktop or on the secure desktop.
The secure desktop presents the login UI and restricts functionality and access to the system until the logon requirements are satisfied.
The secure desktop’s primary difference from the user desktop is that only trusted processes running as SYSTEM are allowed to run here (that is, nothing is running at the user’s privilege level). The path to get to the secure desktop from the user desktop must also be trusted through the entire chain.
- `User Account Control`: Switch to the secure desktop when prompting for elevation –> Enabled

User Account Control: Virtualize file and registry write failures to per-user locations
This policy setting enables or disables the redirection of the write failures of earlier applications to defined locations in the registry and the file system. This feature mitigates applications that historically ran as administrator and wrote runtime application data to %ProgramFiles%, %Windir%, %Windir%\system32, or HKEY_LOCAL_MACHINE\Software\.
This feature can be disabled for applications on devices running at least Windows Vista because it is unnecessary.
- `User Account Control`: Virtualize file and registry write failures to per-user locations –> Enabled

2.User Account Control security in the registry
- The necessary settings can be performed with the Registry as follows

HKEY_LOCAL_MACHINE \ SOFTWARE \ Microsoft \ Windows \ CurrentVersion \ Policies \ System

FilterAdministratorToken
FilterAdministratorToken is disabled by default (0) but can be set to (1) instead which would require the user to approve operations that require elevations of privileges.
FilterAdministratorToken(REG_DWORD) –> 1

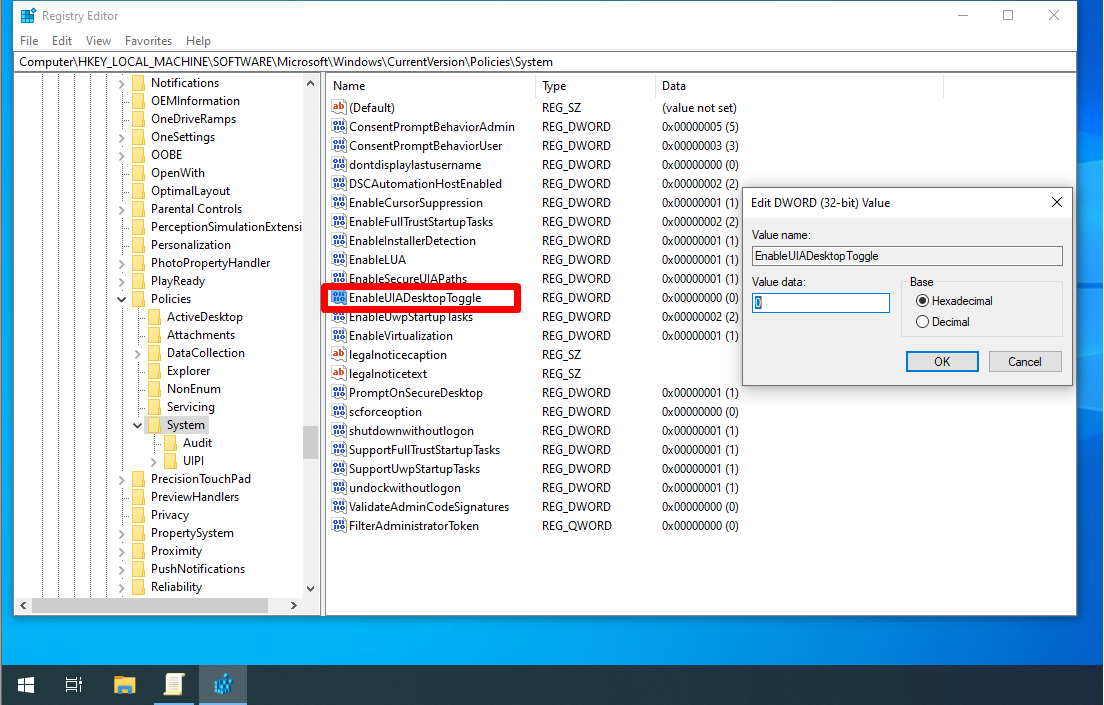
EnableUIADesktopToggle
EnableUIADesktopToggle is disabled by default (0). It determines whether UIAccess applications can prompt for elevation without the secure desktop. UIAccess applications are digitally signed.
- `EnableUIADesktopToggle` (REG_DWORD) –> 0
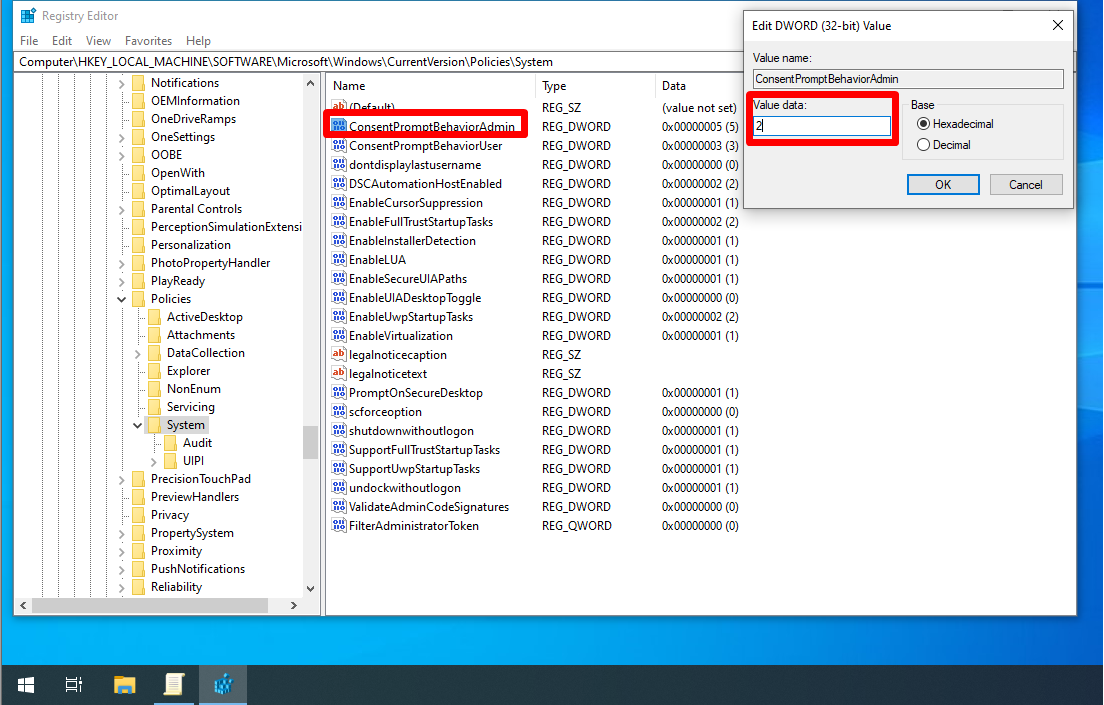
ConsentPromptBehaviorAdmin
This key defines the User Account Control behavior for system administrators. The default value is set to prompt but do not require credentials to be entered. Here are all possible values.
The value of 2 displays the UAC prompt that needs to be permitted or denied on a secure desktop. No authentication is required.
- `ConsentPromptBehaviorAdmin` (REG_DWORD) –> 2
ConsentPromptBehaviorUser
A value of 0 will automatically deny any operation that requires elevated privileges if executed by standard users.
- `ConsentPromptBehaviorUser` (REG_DWORD) –> 0

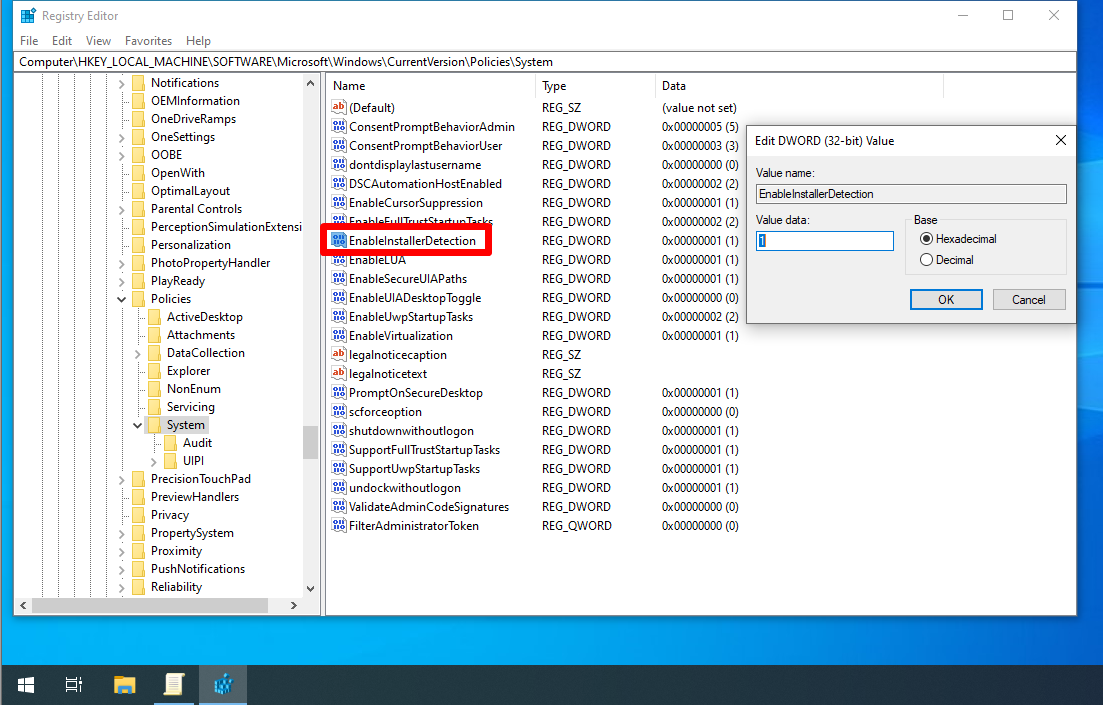
EnableInstallerDetection
EnableInstallerDetection set to 1 on all versions of Windows except Enterprise where it is set to 0. It determines whether application installations prompt for elevation (0 disabled, 1 enabled).
- `EnableInstallerDetection` (REG_DWORD) –> 1
EnableSecureUIAPaths
EnableSecureUIAPaths is enabled by default (1). If disabled (0), will allow the execution of UIAccess applications from non-secure locations.
EnableSecureUIAPaths(REG_DWORD) –> 1

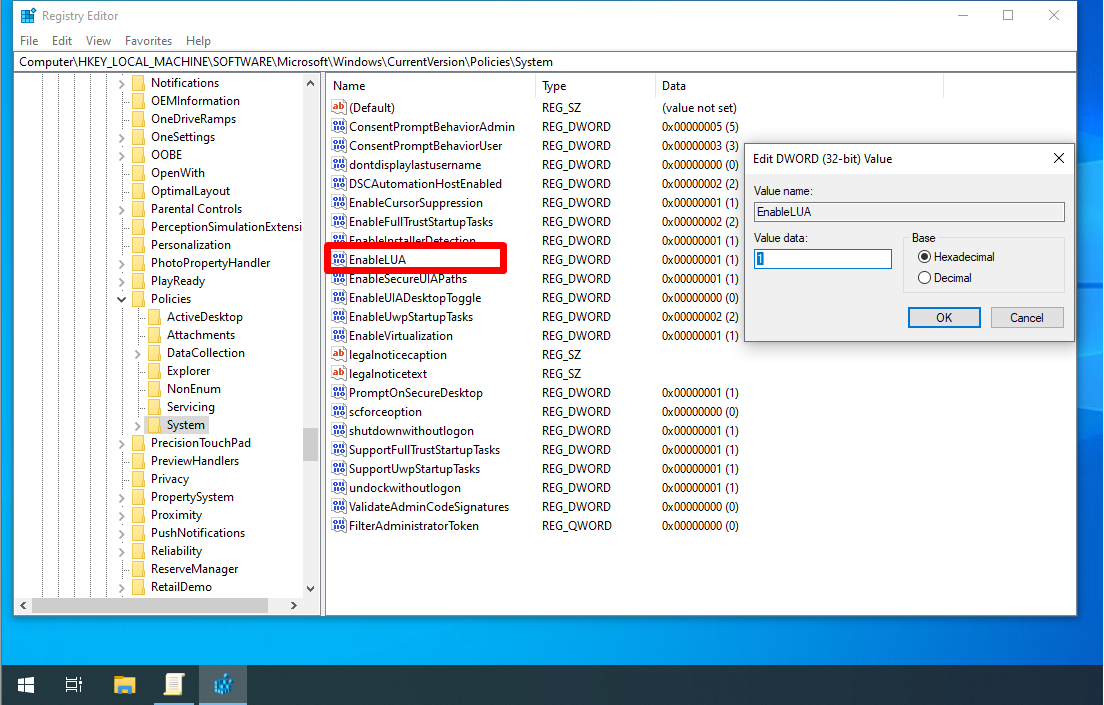
EnableLUA
EnableLUA enabled by default (1). If disabled (0), will disable admin approval mode and all related UAC policy settings.
- `EnableLUA` (REG_DWORD) –> 1
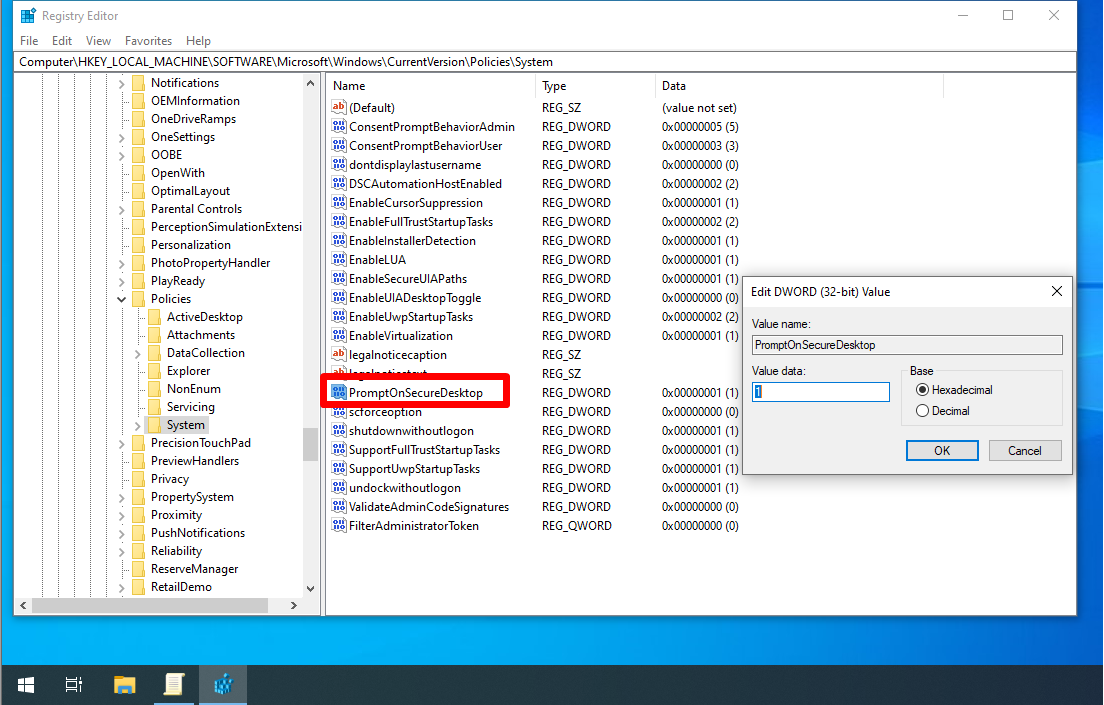
PromptOnSecureDesktop
PromptOnSecureDesktop determines whether UAC prompts are displayed on a secure desktop (1, default) or not (0). This gets rid of the full-screen prompt when disabled.
- `PromptOnSecureDesktop` (REG_DWORD) –> 1
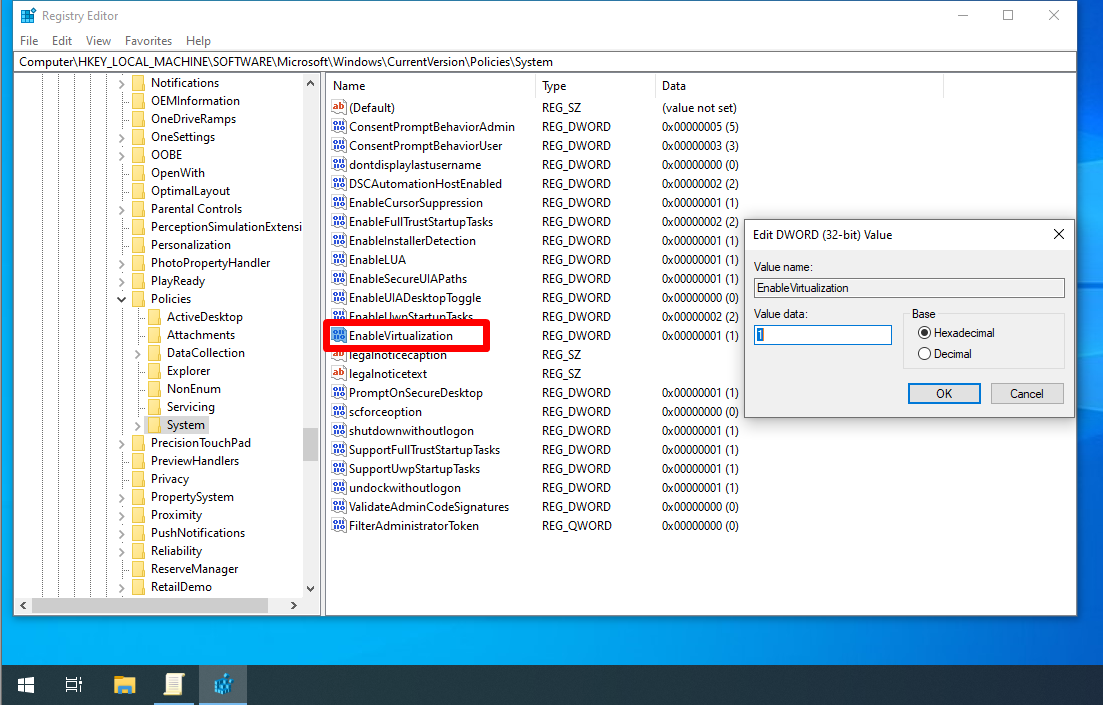
EnableVirtualization
EnableVirtualization enabled (1) by default which redirects application write failures at run time to defined user locations. Applications that write data to protected locations will fail if disabled (0.
- `EnableVirtualization` (REG_DWORD) –> 1