Web Firewalls (WAF) are used to protect web applications. This article will review the general features of Web Firewalls.
Attacks on Web Applications and OWASP
Corporate Web Application Firewlls maintain the mechanism of OWASP, which means open web aplication security project, according to the current web vulnerability list. This is an accepted and guided list by the standard WAF designers.
OWASP
Owasp, an open web application security project, is a community established to tackle the problems of unsafe software. All OWASP’s tools, documents, lists and sections are available free of charge to every software security employee and enthusiast. The WAF to be located must be able to detect and block known types of attacks. There are even WAFs that can detect zore-day attacks with data learning methods. The selected WAF must first be able to identify the following attack types, which are also on the OWASP’s list.
According to the list od OWASP, some of the weaknesses found in web applicaitons are as follows.
-SQL İnjection; Injection attacks occur when data from users is used in commands or database queries without checking them.
–Cross Site Scripting; is the attacker’s inclusion of malicious code in a web application, which can go as far as capturing the application.
-Command Injection; In this type of vulnerability, an attacker could exploit the vulnerability of the application running on the server to include and execute any commands on the system.
-Local File Including; The Lfi deficit is a vurnerability found in Php. The reason for this vulnerability is the assignment errors of the variables. Novice Php encoders unfortunately fall into this type of errors. However, this vulnerablity, which is almost no longer available, can still be found on Php systems encoded from scratch.
-Buffer Overflow; is a case where a program consistsof functions that are used incorrectly (strcpy, strcmp, etc.) in case of a crash with loading more data than storage capacity.
–Brute-Force Attack; is a kind of digital and cryptography attack to capture a password.
–Cookie-Session Posioning; One of the attacks made by sending incorrect parameter to web application.
-Session Hijacking; is a literally means “stealing session”.
-Server Misconfiguration; server misconfiguration exploit configuration weaknesses found on web and application servers.
-Parameter Tamper; is a simple attack targeting application business logic. This attack is caused by mant programmers relying on hidden or fixed fields (such as a hidden tag in a form or a parameter in a URL) as the sole security measure for certain operations.
-Local File Inclusion; is a view of a file that is not served to site on the target site.
-Remote File Including; is an attacker’s ability to view his or her file (for example, a shell file) on the target site.
Firewall and Methods
There are six popular firawall technologies, the pros and cons of various firewall technologies with examples and more detailed explanations are described bellow.
-
Application-Based Firewall
A software package that allows or denies access between networks. You can keep a record of what you want to do and what you do. Not all hosts, internal or external, will accept the connection. Provides user-level authentication. Detect malicious code in data packets. Record specific activities in data traffic.
-
Paket Filtreleme
It is the simplest firewall in terms of application. Configuring is very simple. Routers are configured to filter packets by comparing packet contents against predefined condition criteria. Adding a packet filter to a router does not create additional performance overhead. Packet filtering takes place in the network and transport layer, ie it can be used in all applications. As the complexity of packet filtering on a router increases, router performance will decrease. In some cases, filtering does not match certain caching strategies commonly used for performance enhancement.
-
Status Checking
Packet filter technology developed. Developed by Checkpoint in the 90s. Over time it has become a standard. Also known as dynamic packet filtering. The contents of the individual packages are examined. Low cost, high performance. As with packet filtering, the state checking method works on the network and transport layer. So it does not require an extra client configuration and software.
-
Proxy
It provides an intermediary connection between servers on the Internet and internal servers. For incoming packets, the proxy acts as a server to clients on the internal network. For outgoing packets, it acts as a client that sends data to servers on the external network. Proxy service provides high security because it works in the application layer. It also provides user-level authentication. Proxy systems provide automatic protection for weak or faulty IP applications and succeed in filtering.
-
Network Address Translation
Allows a network to internally use a set of network addresses and a different set when working with external networks. Network address translation does not provide any security by itself, but it helps to hide the internal network layout and help the connections go through a blockage point.
-
A Virtual Private Network
A virtual private network uses encryption and integrity protection. You can use a public network (the Internet) as if it were a private network. Virtual private networks allow you to remotely use security-powered protocols. However, virtual private networks contain dangerous network connections.
Web Application Firewall Operating Modes
-
Reverse Proxy
Among the web application firewall is the most common and feature-rich deployment. All traffic passes through the WAF. For incoming requests, Server acts as the back-end web server. But it can increase the delay for applications.

-
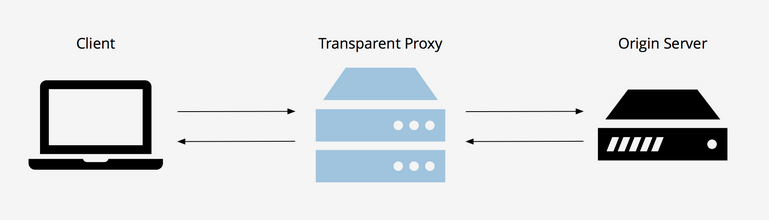
Transparent Proxy
Is this mode, the WAF is located between the Firewall and the Web Server, but does not broadcast an IP address. It acts like reverse proxy.
-
Bridge
In thşs method, the WAF device is placed in front of web servers in bridge mode to pass and examine the traffic. The only disadvantage is the possibility of interruption of web traffic after a malfunction in the system.
-
Off-Line Network Monitoring
The WAF is not even on this campus. Ideal for monitoring the networ from the outside. WAF can block the traffic by sending a TCP reset message to intercept unwanted traffic on this campus.
-
Server Based
This campus is located on the WAF web server. It is preferable if the number of systems to be protected is low. But it exhausts the server.
Web Application Firewall and Methods
WAF is an anti-intrusion system developed mainly against security threats to web and application servers. It provides a higher level of security protection against application servers than a typical IPS system.

-
Signature Based WAF
Incoming HTTP / https requests are compared with the characteristics of known attack signatures. If signatures are not updated within constantly changing attacks, many malicious requests that have been modified during use will bypass the web firewall. The purpose of intrusion detection systems is to unauthorized access, infiltration of information systems, detection of unwanted and malicious network traffic, and to minimize the damage of malicious software such as viruses, trojans and worms. The signature-based approach is more acceptable in the real world as it generates fewer false warnings than other approaches. However, it may be insufficient against new malware.
-
Abnormality Based WAF
The anomaly-based intrusion detection system operates on a predetermined behavior reference. In the behavior determination process; CPU usage, number of TCP connections, monitoring events, keystroke records, system calls, network packets, user session times, number of emails, access to file systems and secure working conditions are used. Abnormality-based web application firewall projects, including HTTP traffic related anomalies in HTTP messages, Protocol properties, abnormalities in calling a web application, and abnormalities in message content carried over HTTP, are being implemented. With these studies, signature based WAF deficiencies have been addressed and the aim is to minimize malicious requests to deceive the firewall.




