We will explain how to add a rule in “McAfee Access Protection” and “McAfee EDR Triggers“, the rule for the “CVE 2022-29072” vulnerability, where you can find the vulnerability, exploitation, mitigation methods at “https://github.com/kagancapar/CVE-2022-29072“. Up to version 21.07, which is the current version of 7zip, is affected by this vulnerability. It allows for escalation and is not very complex to exploit.
It is possible to detect the exploitation of the related vulnerability, after running 7zip.exe, by writing a rule in case of child processes PowerShell, cmd or a network connection.
Write Rules in McAfee Access Protection
We will apply this rule to the policy that all machines use. On the Access Protection side, follow the steps below to take a block action when the “cmd.exe” and “powershell.exe” sub-processes run from within the “7zFM.exe” and “FzGM.exe” processes.
First, we click on the “Endpoint Security Threat Prevention -> Access Protection -> My Default ->” tab and click “Edit”. Here you should add to which policy you are using in your institution.
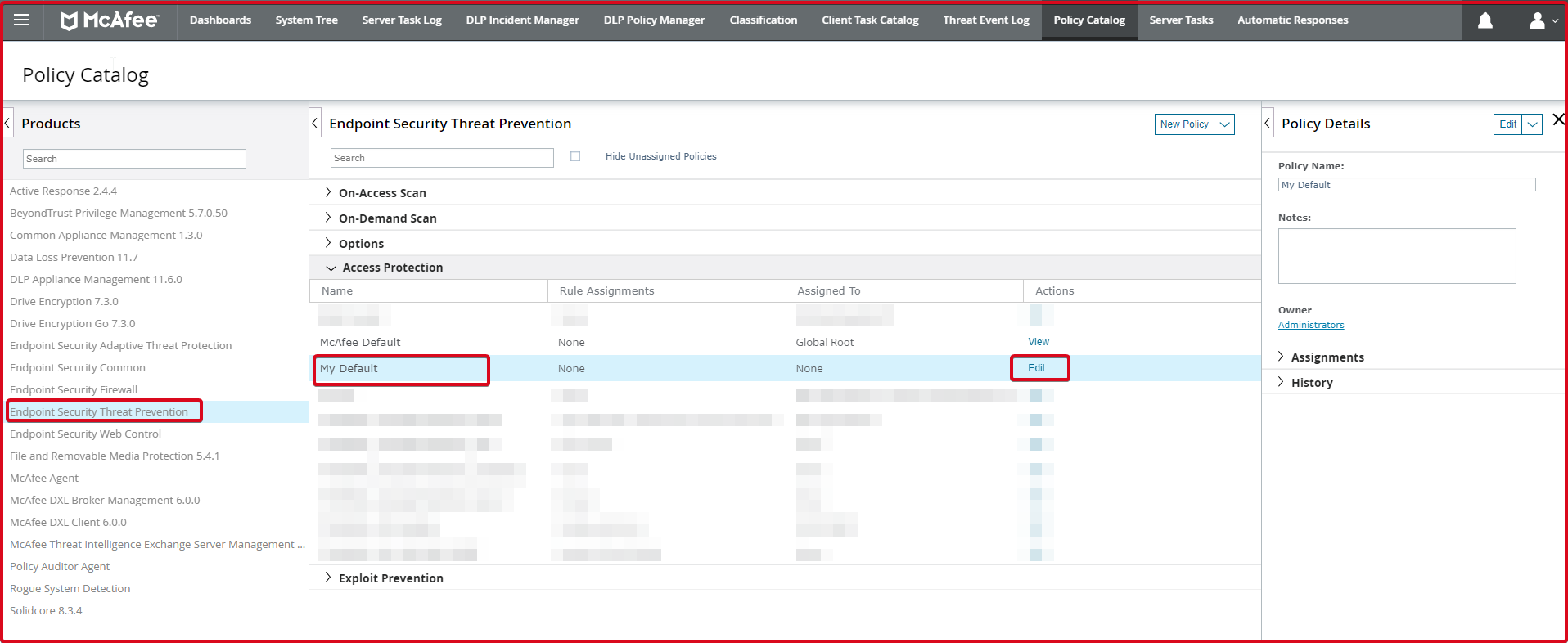
Afterwards, we click on the “Add” button since we will enter a new rule in the “Rules” section.
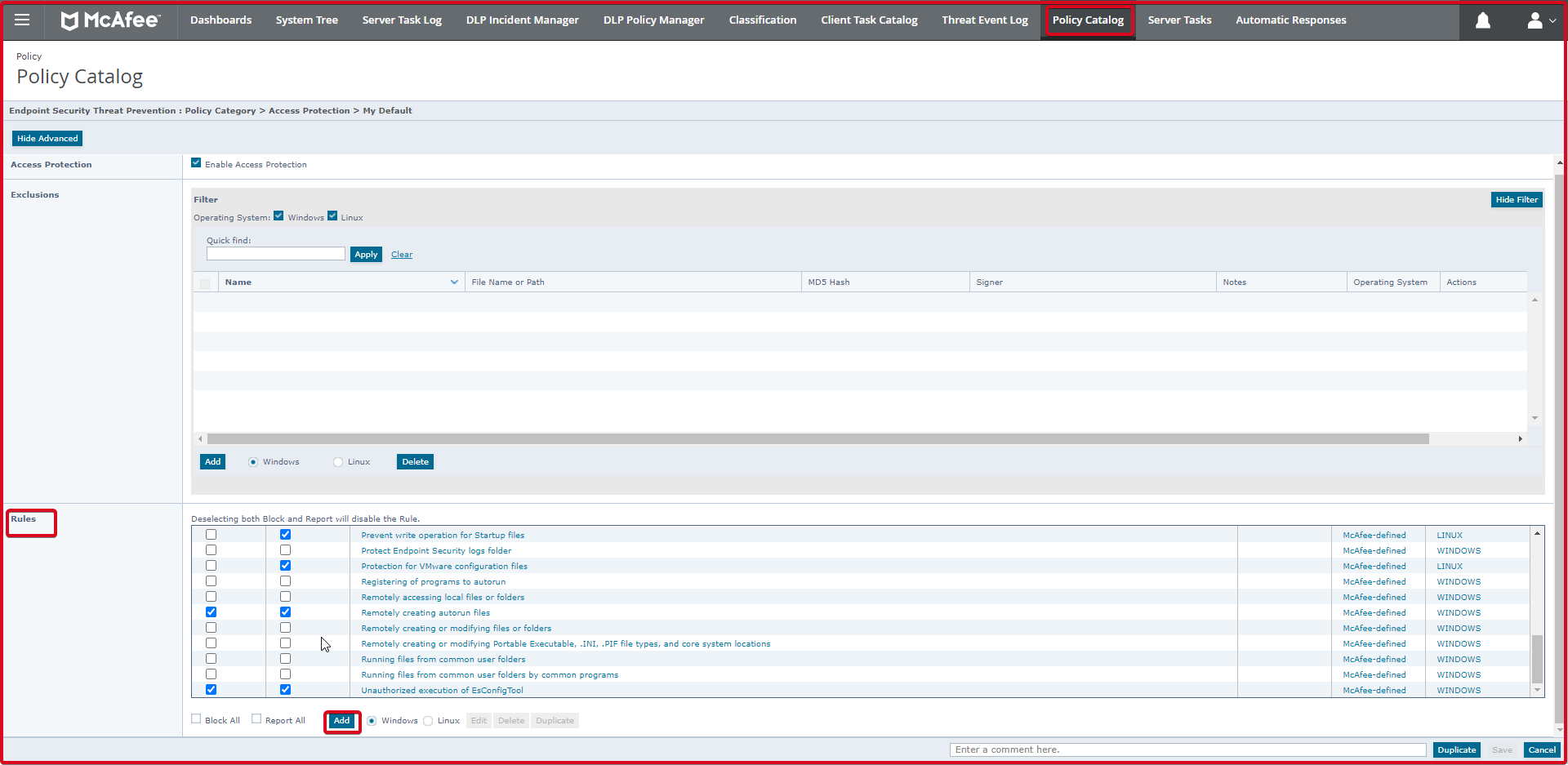
Here in the “Options” tab, we will add the “7zFM.exe” file with the opening in the “Executables:” section. To do this, click the “Add” button.
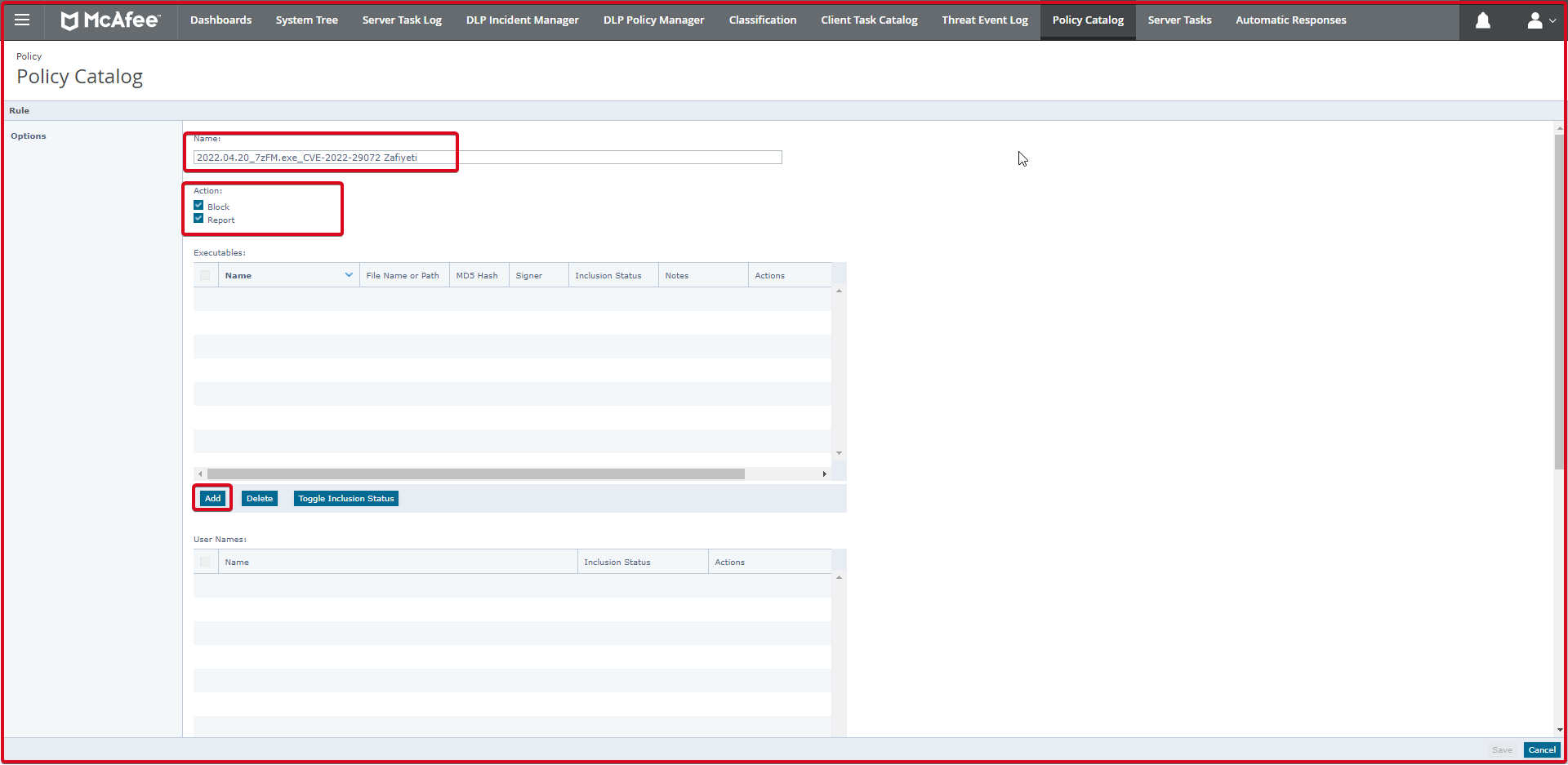
This page also adds the “7zFM.exe” file to the “File name or path” section. Enter the rule name in the “Name:” field. Click the “Save” button.
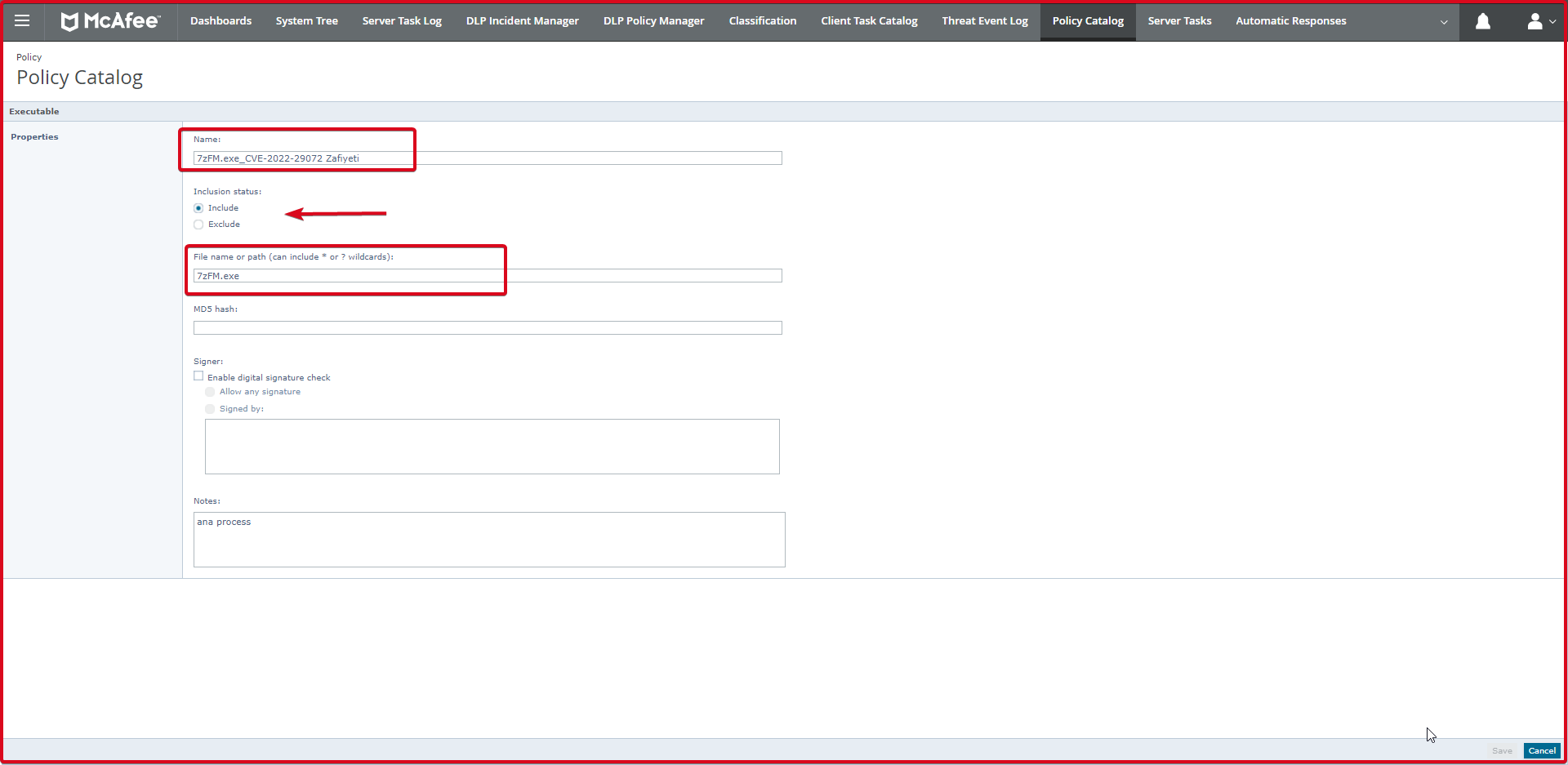
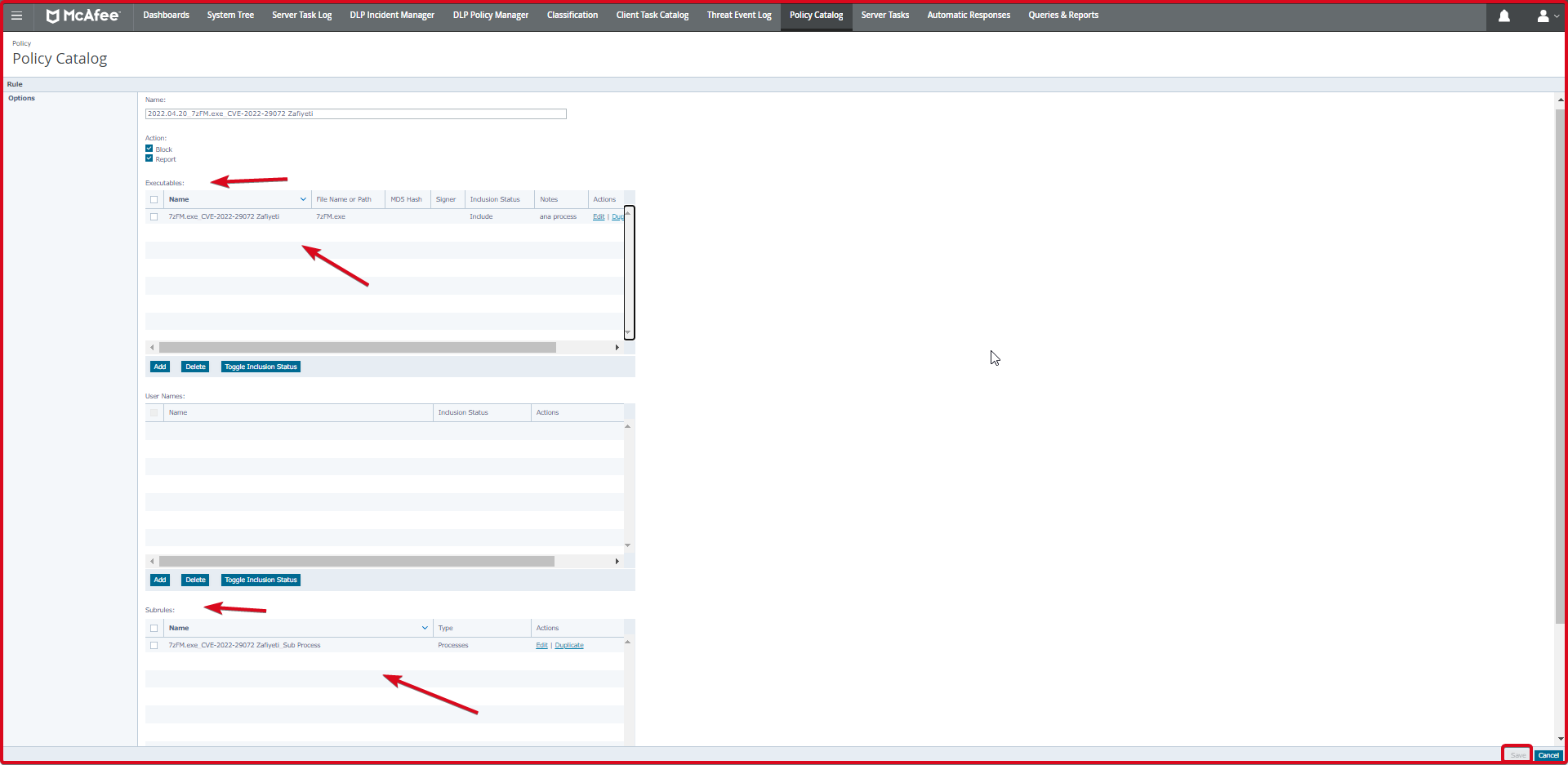
It is seen that the “7zFM.exe” file below has been added. This is the main added process.

In the next step, we will enter the sub-rules in the “Subrules” section at the bottom. To do this, click the “Add” button.
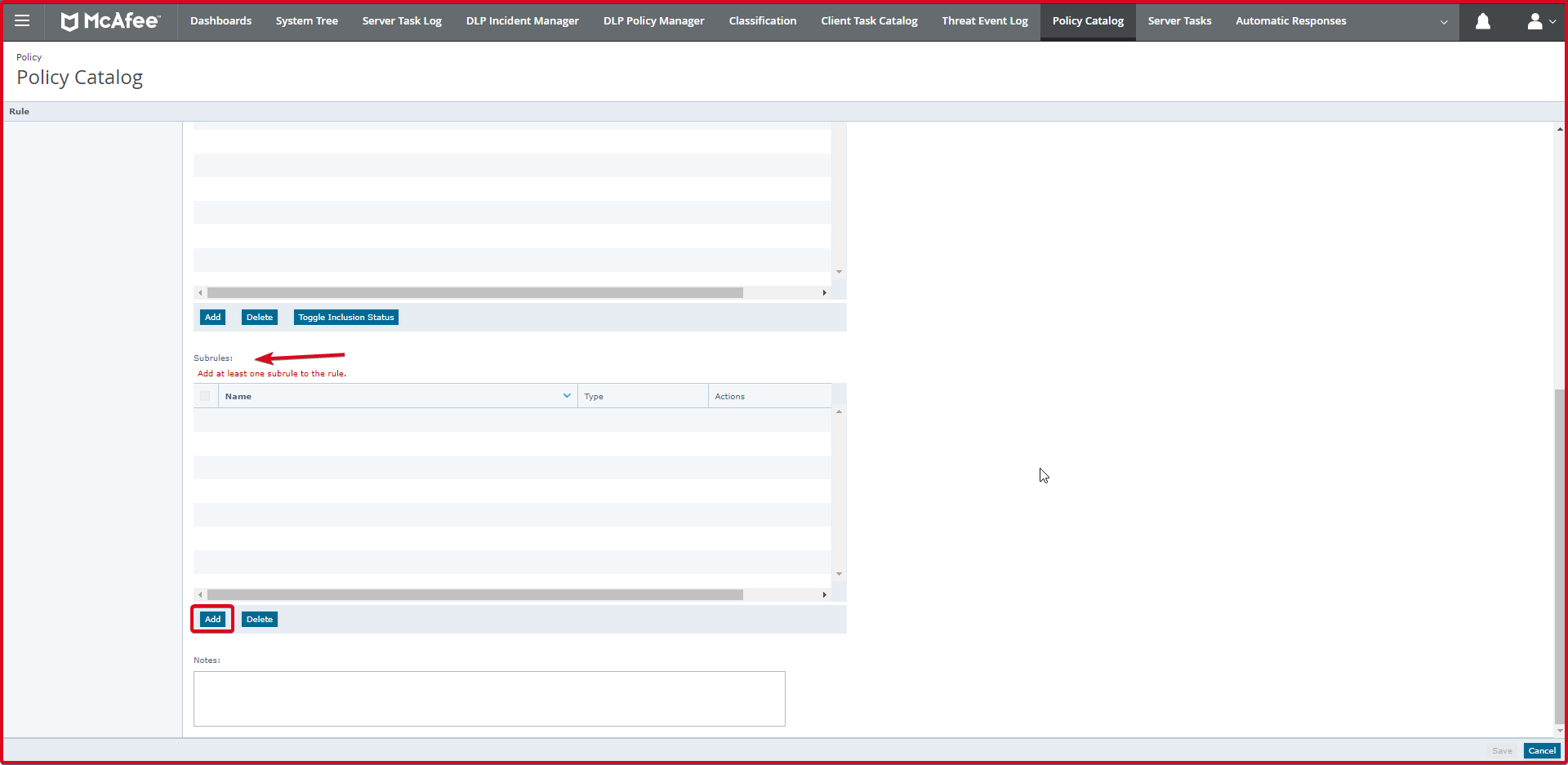
On the “Subrules” page, we will enter the sub-rules. Here we need to enter two processes. These are cmd.exe and powershell.exe. To add processes, click the “Add” button below.
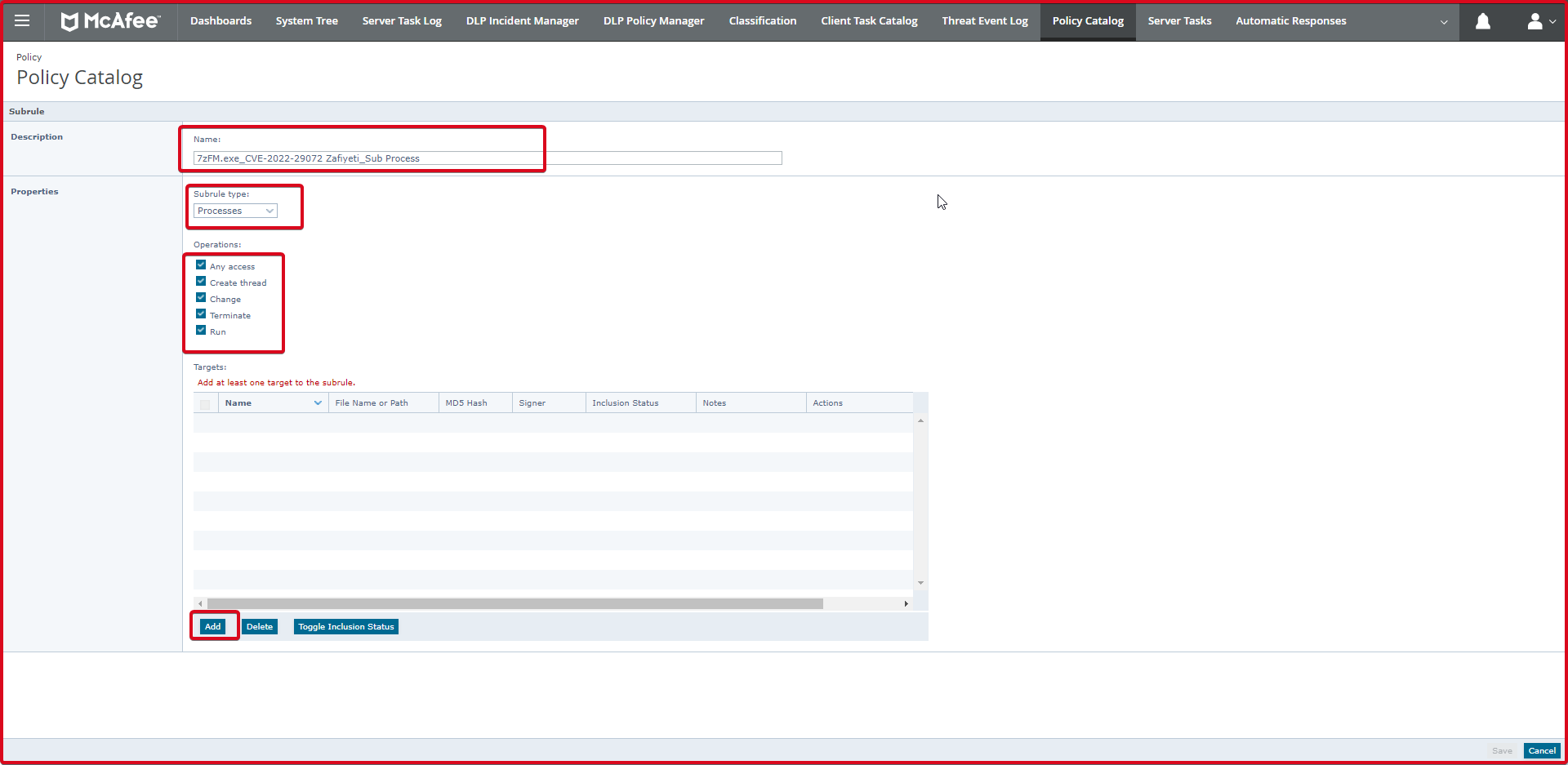
On the “Executable” page, we write the name of the process we want to write. We write the process in the “File name or path” section. For example **\cmd.exe process. Whichever path the “**\” sign starts with, it means to include cmd.exe.

Then click the “Save” button. After adding the Powershell.exe process, we click the “Save” button again.
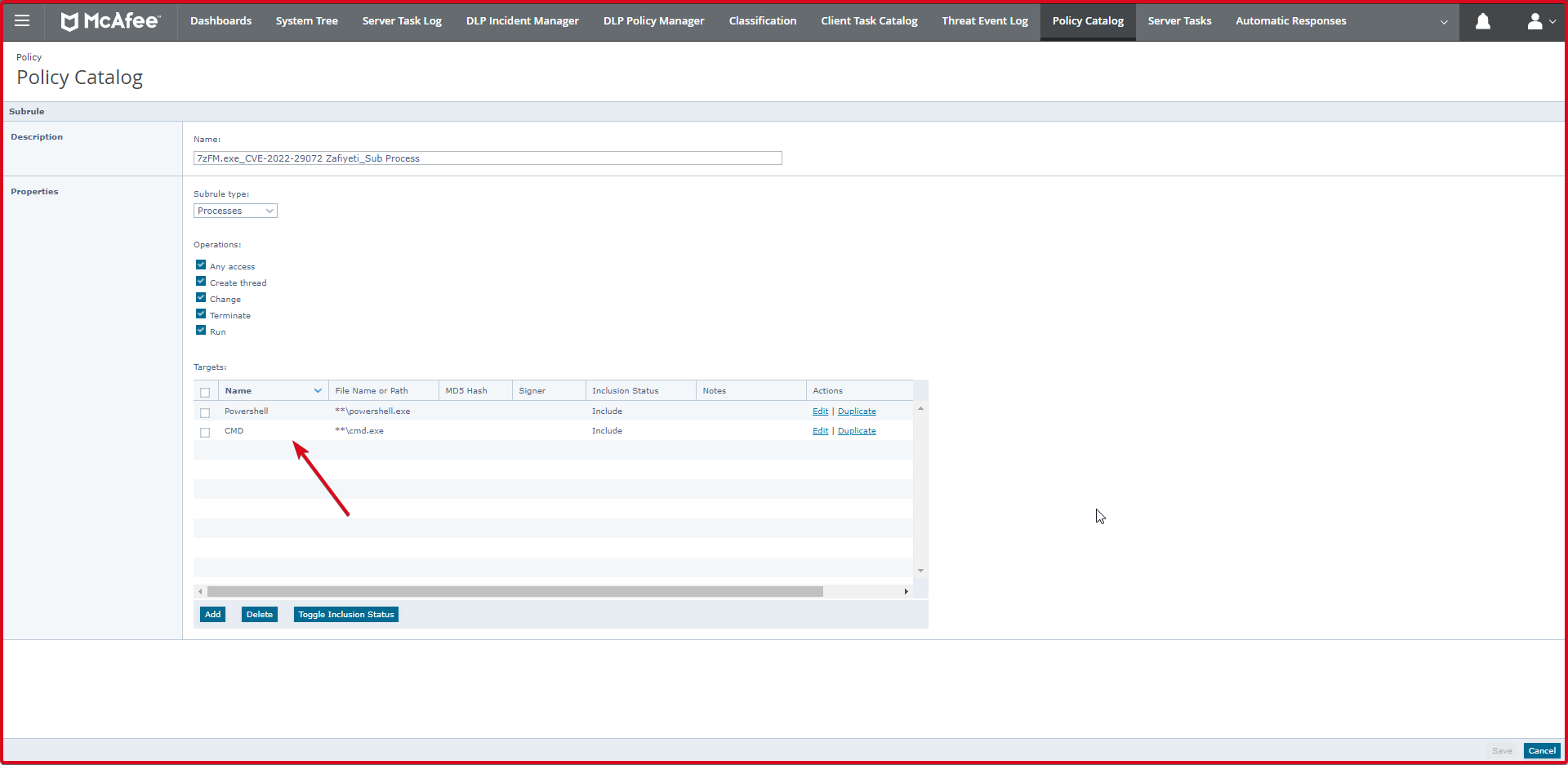
In the end, the screen where we add both the child processes and the parent process is shown below. Finally, we click on the “Save” button again. This is the rule we added in “McAfee Access Protection”.
Write Rules in McAfee EDR Triggers
On the McAfee EDR (Endpoint Security Resource) side, we will write triggers that take the “KillProcessTree” action when the “cmd.exe” and “powershell.exe” sub-processes run from within the “7zFM.exe” and “FzGM.exe” processes. For this, follow the steps below.
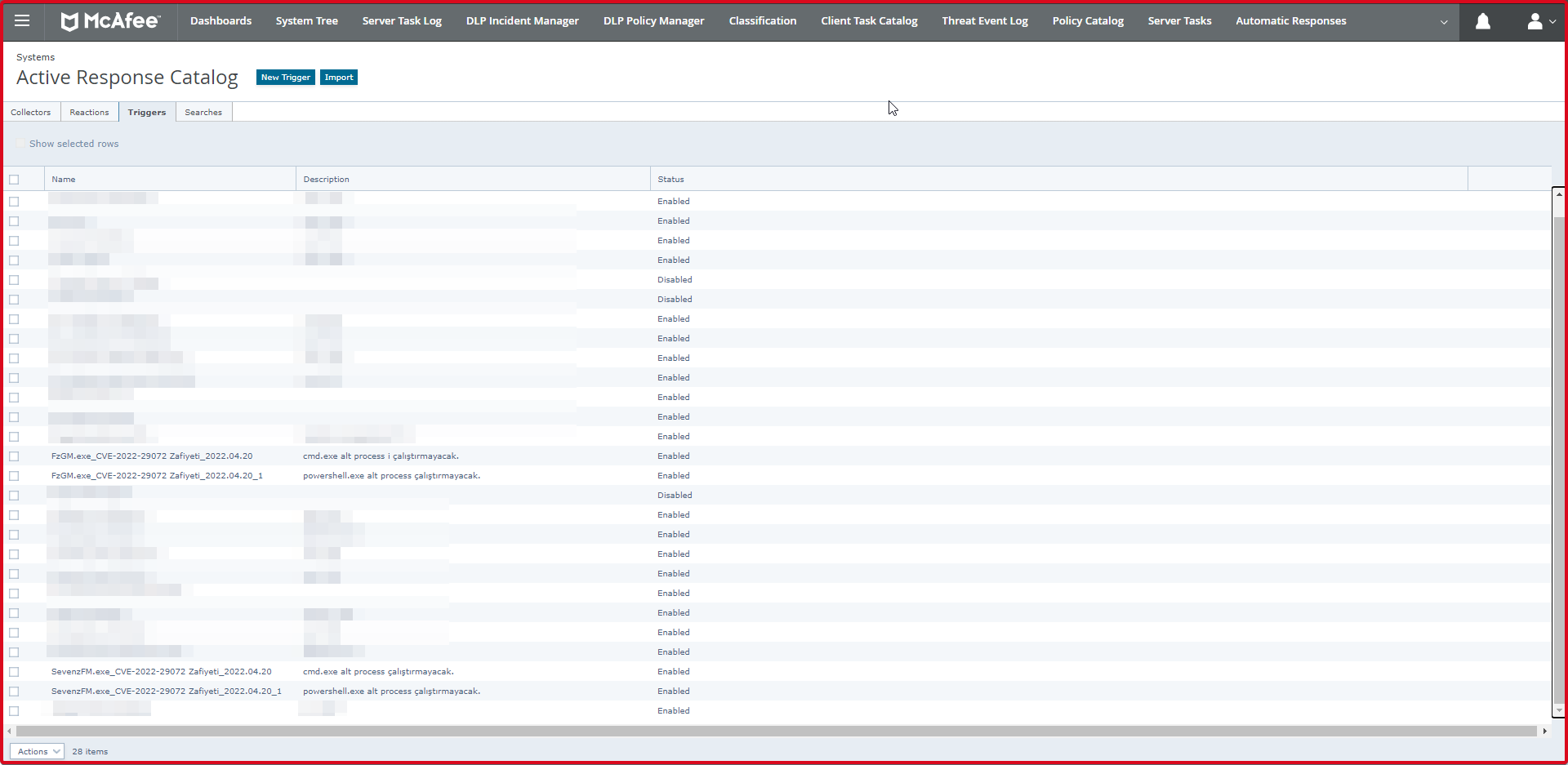
First, we click on the “Active Response Catalog” tab on McAfee EPO.
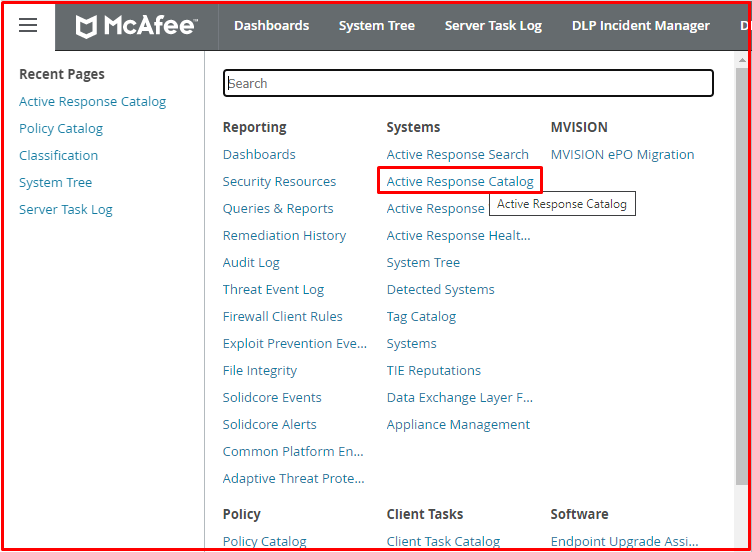
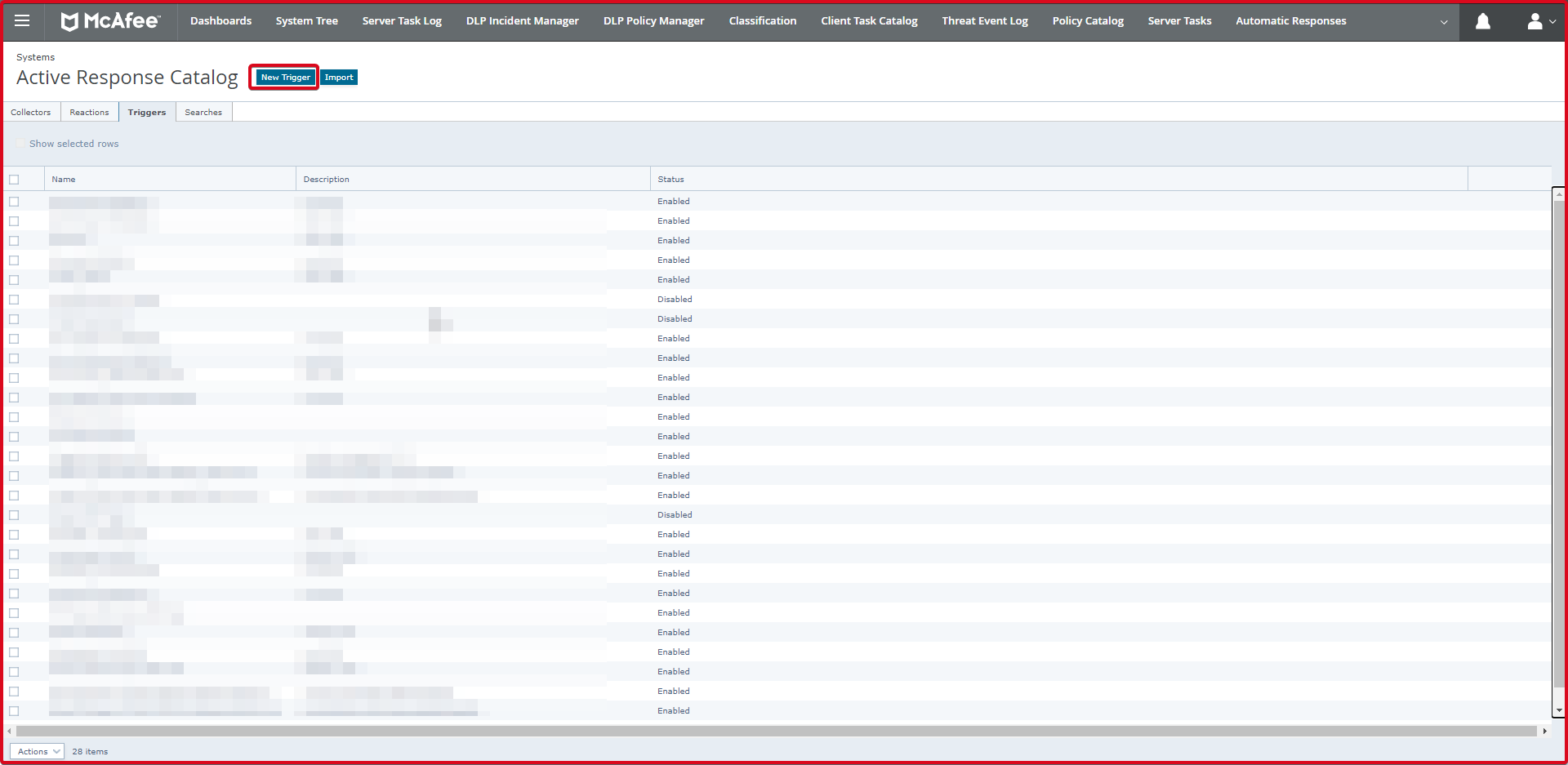
Then click on the “Triggers” tab. Here we click the “New Trigger” button to add a new trigger.
On the “Triggers” page, we enter the rule name. In the “Trigger Configuration” section, we “Enable” as “Status“. We choose “Critical” as “Event Severity“. If you want, you can change this according to the importance of this opening.
In the “Detection” section, we select “Process” as “Type“. We choose “ProcessCreated” as “Event“. In the “Condition” section, we write the rule. The rule is as follows.
Process name equals "cmd.exe" and Process parentname equals "FzGM.exe" Process name equals "powershell.exe" and Process parentname equals "FzGM.exe" Process name equals "cmd.exe" and Process parentname equals "7zFM.exe" Process name equals "powershell.exe" and Process parentname equals "7zFM.exe"
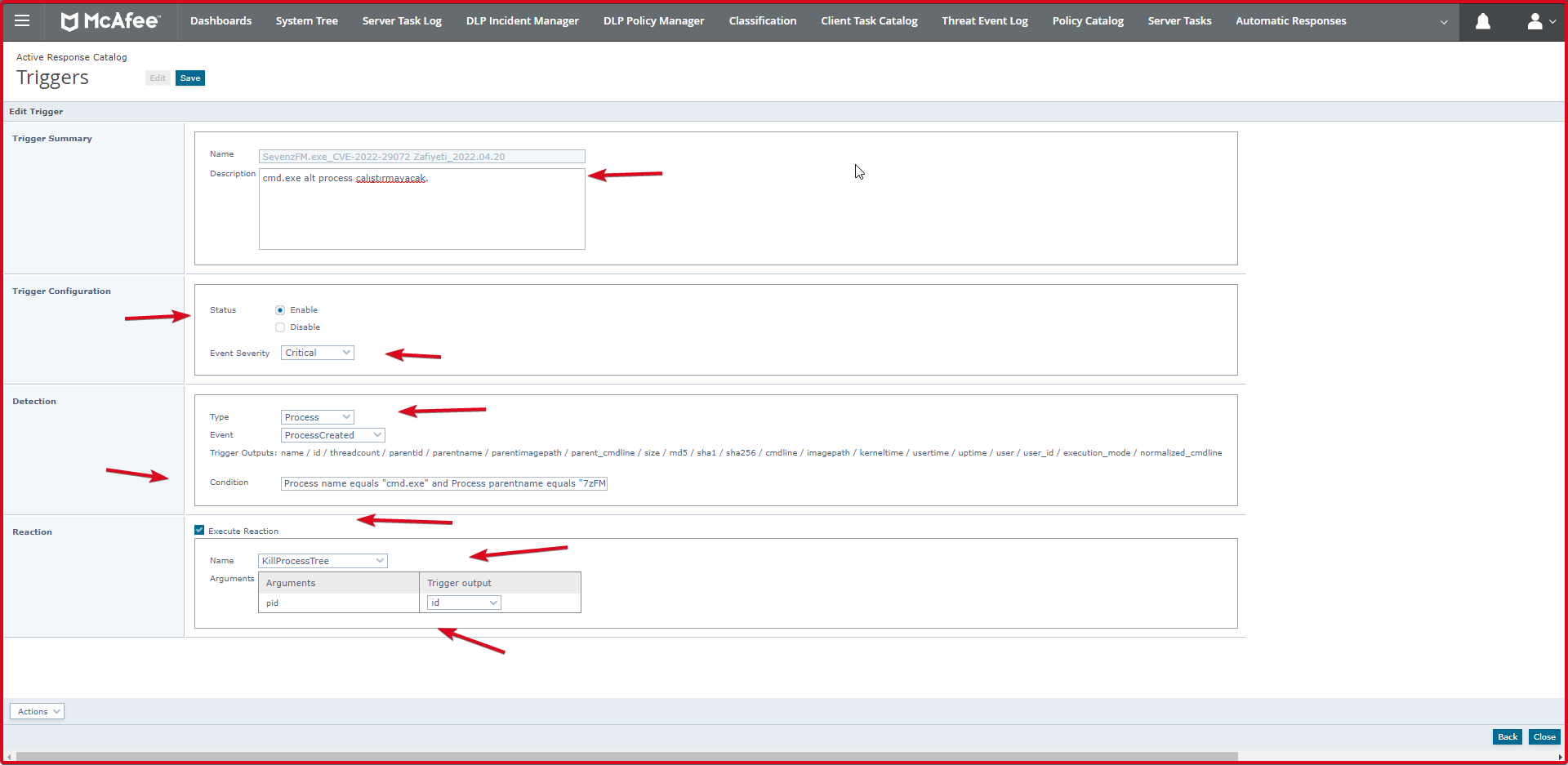
Here we have entered four rules in “Triggers” regarding this opening. You can see the state of these rules on the screen below.