SSID (Service Set Identifier) are names that help identify and login to wireless home networks or hotspots. In other words, SSID is the “name of the Wi-Fi network”. In a place with plenty of Wi-Fi connections, you must have turned on your Wi-Fi connection before. When you open your Wi-Fi connection, all the names of the networks that appear on your device are SSIDs and they help determine the identity of that network.
Hiding the SSID is not shown to us or reflected in the style of “Other Network” as it does not broadcast the SSID when we look at the networks we want to connect to with a card in station mode, in our normal phone or computer. It is a method normally used for security purposes. It is a weak method like MAC Filtering. A conscious attacker can see and target your network broadcasting by hiding the SSID while listening to networks in the environment. In this method, the situation is similar to MAC Filtering. It is sufficient to have a target network and a device connected to the target network to bypass it.
What we will do is enable the target network and the device connected to the network to perform the authentication (handshake) process again. In short, catching handshake.
Finding the SSID
Wireless Network is in Monitor Mode
First, let’s switch our wireless network card to monitor mode as usual. wlan0 is the path to our network card. Your network card’s path can be mon0 or rausb0.
sudo airmon-ng start wlan0

Networks in the Environment
Let’s listen to the networks in the environment using “airodump-ng“.
sudo airodump-ng wlan0mon

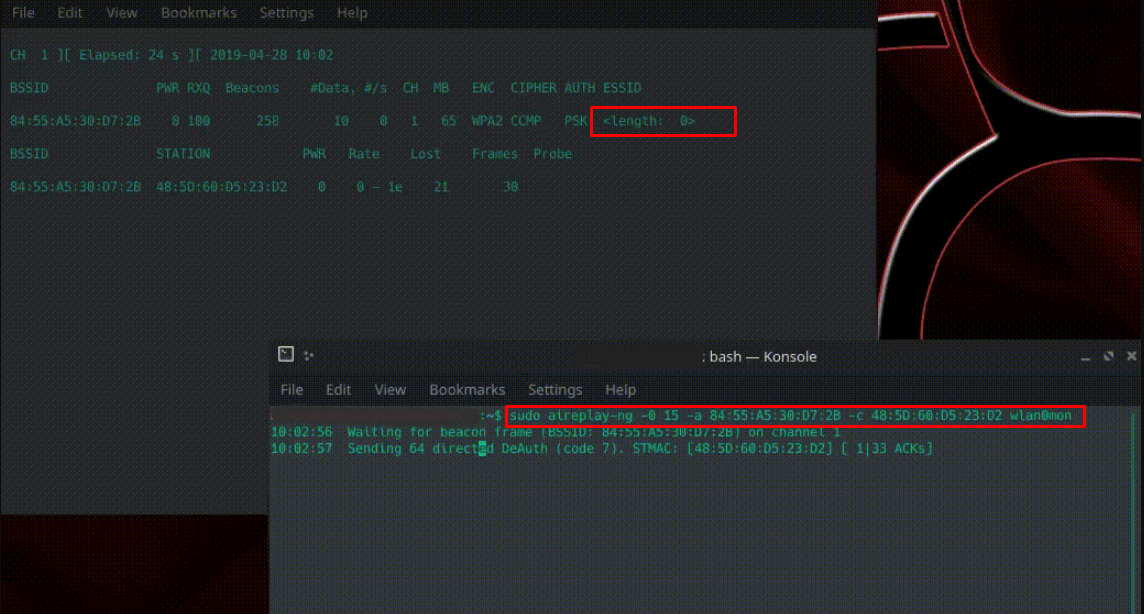
Here, by looking at “<length: 0>”, we can understand that our target network broadcasts by hiding the SSID. In some cases, the number “0” at the end of the “<length: 0>” output can tell us how many characters the SSID of the wireless network consists of. For example, like <length: 15>. This is not always true.

Wifi Network Hidden Name Detection
When we look while listening, there is a device connected to the target. Now we need to send “deauthentication” packets to both the target and the device connected to the target to force them to re-authenticate by disconnecting them. We will use aireplay-ng for this.
sudo aireplay-ng -0 15 -a target_ag_bssid -c connected_cihaz_bssid wlan0mon
-0: is the parameter that we determine that the package type we want the aireplay-ng tool to send is “deauth”.
15: We specify how many of this package to send. (15 piece)
-a: It is the parameter that we specify the MAC address of the target network.
-c: It is the parameter that we specify the MAC address of the device connected to the target.
As seen below, we will send deauth packets at the same time while listening to the environment and obtain the SSID of the network. The secret name of our network will replace “<length: 0>” in a few minutes. Although it is easy to know the ESSID, it is important for us to be included in the target network.