The Web for Pentester application is a laboratory environment that can be used in web penetration testing training. Developed by PentesterLab, this platform contains vulnerabilities found in web applications. You can do exercises by identifying these gradual weaknesses.
Cross-Site Scripting (XSS) is on the OWASP Top 10 list. In this article, we will decode the XSS parts of the “Web for Pentester” application. We download the ISO file from the link https://pentesterlab.com/exercises/web_for_pentester/attachments and open it in our virtual machine.


We access the “Web for Pentester” application from our browser with the IP address of our virtual machine as follows.
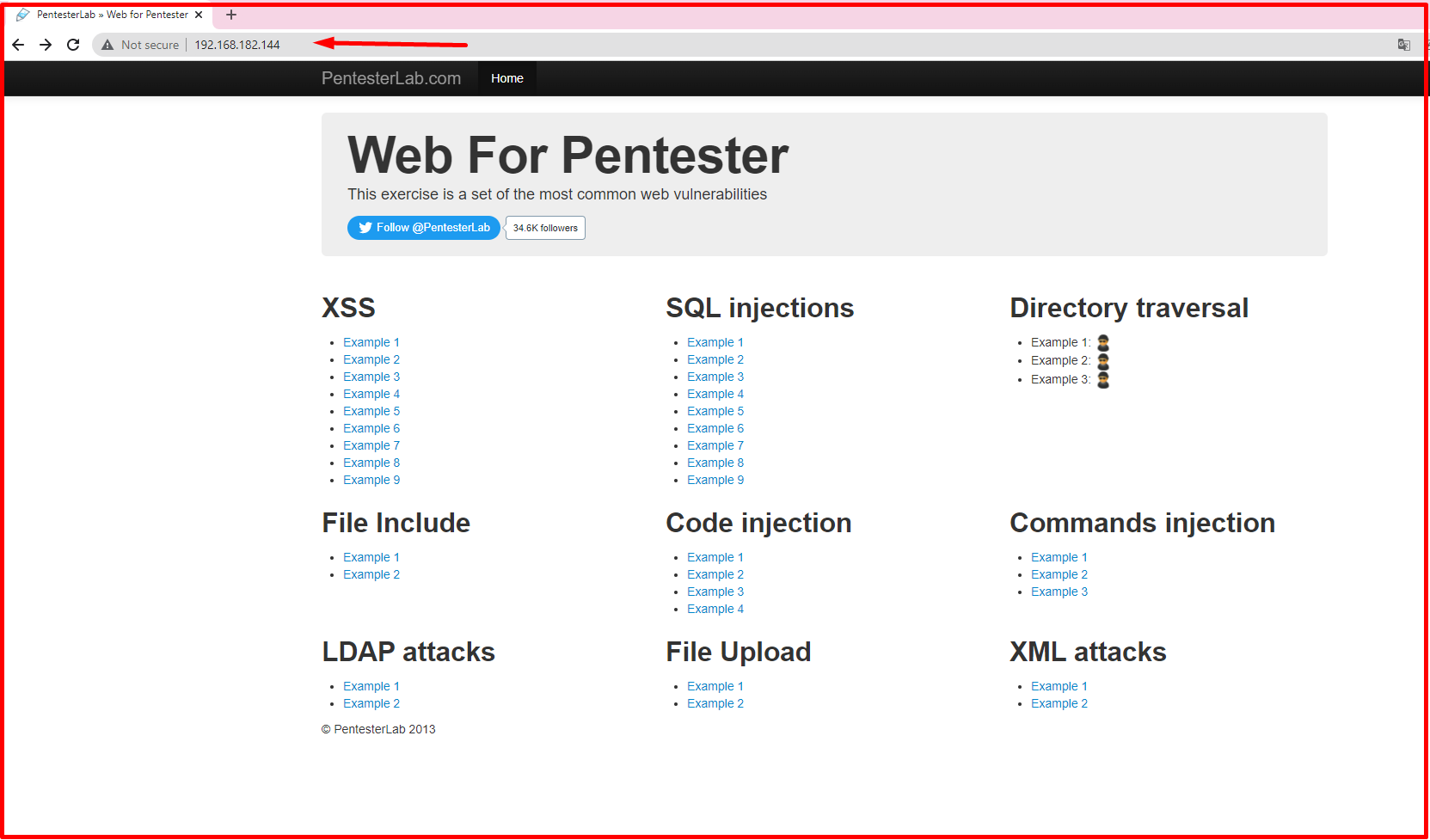
XSS Examples in “Web for Pentester” Application
The “Web for Pentester” application has been prepared to teach many web vulnerabilities. We will now decode the XSS parts of the “Web for Pentester” application. In the example we will do, it will be our goal to detect XSS and see an alert on the page. For this, we start the XSS sections of Web for Pentester.
Example 1:
We did a test for the “name” parameter expected from the user. We’re looking to see if anything we’re going to use while writing the payload is filtered. None are filtered for this example. By typing a payload here, we can decide whether there is XSS detection or not.
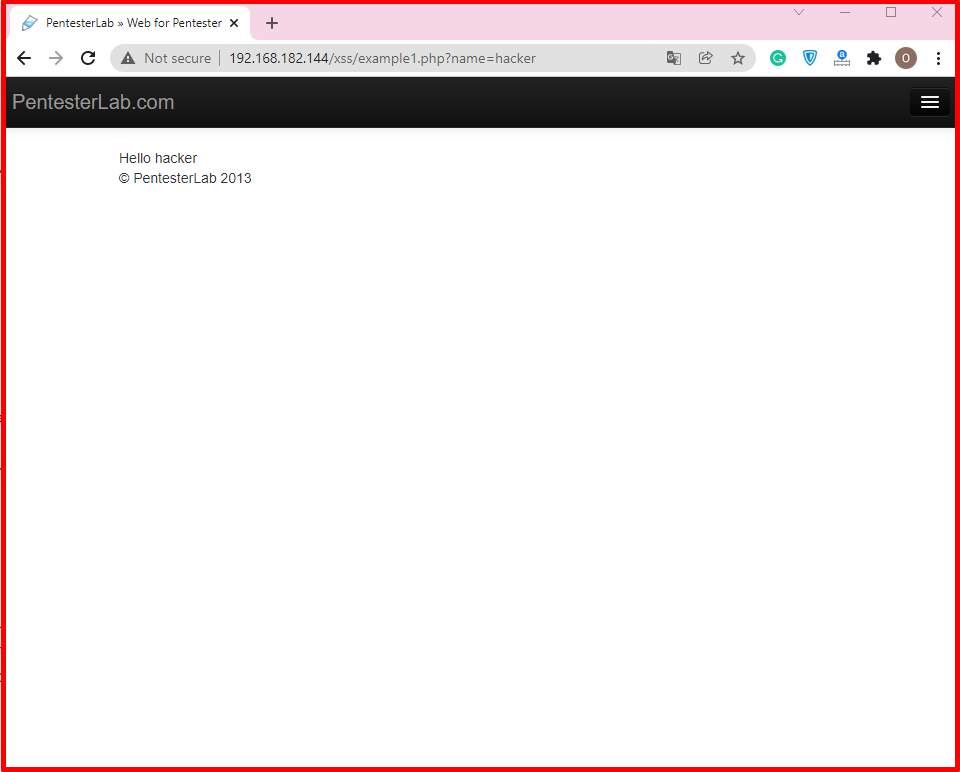
Here, we have found our XSS by entering our “<script>alert(1)</script>” payload and printing the alert on the screen.

If you want to write a name inside the alert, you can write it like “<script>alert(“Hacker Ömer”)</script>“. But sometimes, due to the filtering of quotation marks, entering numbers directly without using quotation marks gives healthier results.

You can see how the payload we wrote looks in the codes by right-clicking on the page and clicking view the page source.