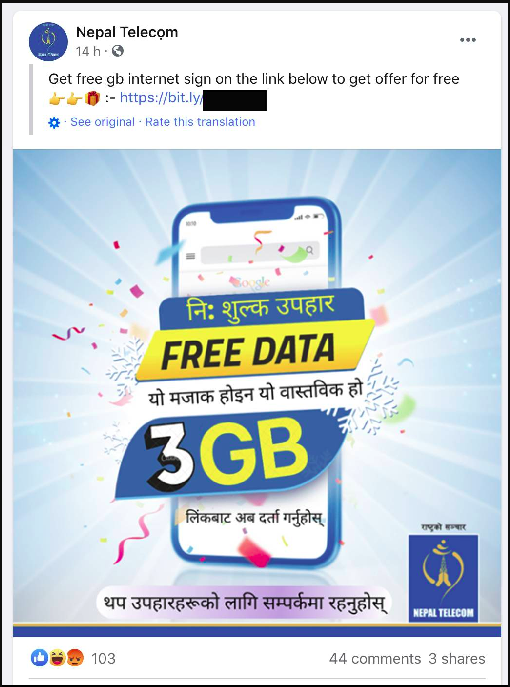
Security researchers recently uncovered a large-scale phishing campaign that mimics the Facebook login page using GitHub pages. The campaign, with its main targets in Nepal, Egypt and the Philippines, was found to affect more than 615,000 users. With the campaign, it was first delivered in a sponsored Facebook post with the title “Free 3 GB mobile data from Nepal Telecom”. The malicious link in the post was pointing to a phishing site hosted on GitHub pages.
Phishing Campaign Operation
The campaign was seen to spread phishing links with the help of Facebook ads, imitating the official institutions of the target countries. The post below shows that it will offer free data packages, mimicking the local telecom service provider Nepal Telecom. The page that posted the ad appears to have made itself almost indistinguishable from the original page by using Nepal Telecom’s profile picture and name. Tunisia, Egypt, Philippines, Pakistan etc. There were similar Facebook posts targeting Facebook users of countries.
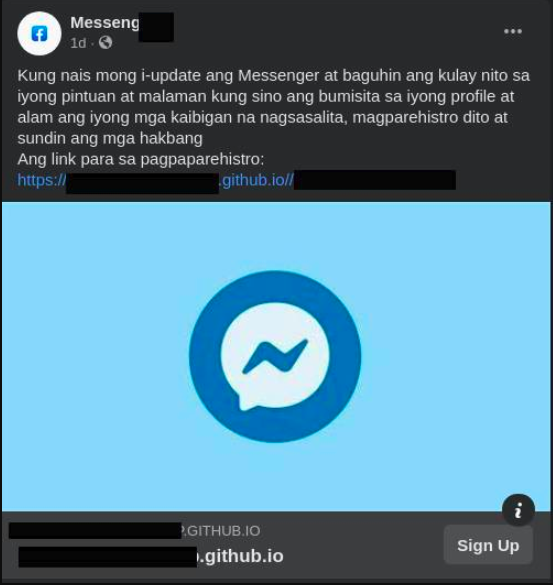
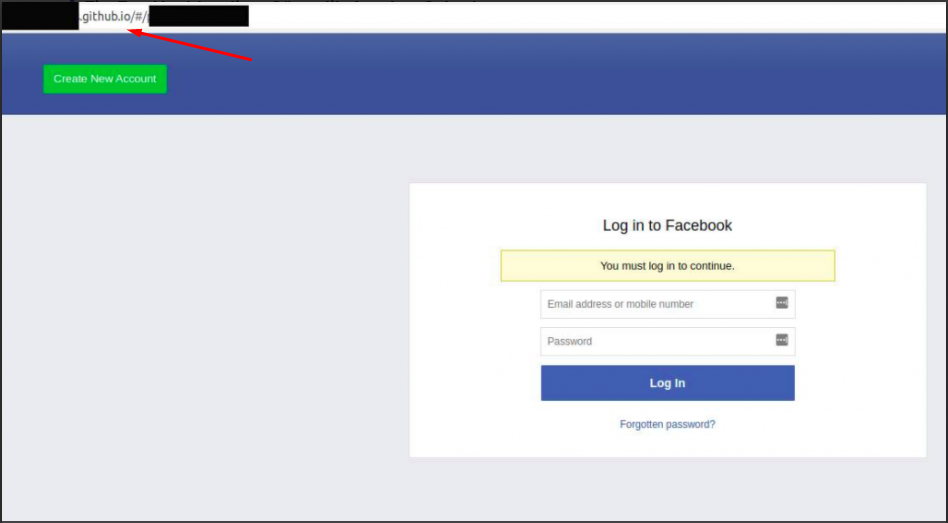
Github Page Redirect
The links in the posts lead to a static Github page with a Facebook login panel. After the victim entered the Facebook information on the static phishing page, the information was transmitted to 2 different places. First to the Firestore database, then to a domain owned by the attackers.
In order to prevent the spread of such phishing pages, Facebook blocks pages containing malicious links from advertising. However, the attackers initially used Bitly (link shortening) links to point to a harmless page. After the approval of the post’s suitability for advertising, it was determined that they changed the post link to point to the phishing page.
About 500 GitHub repositories containing phishing pages have been discovered as part of the same campaign. It seemed that the pages were created on GitHub 5 months ago. It was determined that the domain name used in the campaign was first created on April 3, 2020, behind CloudFlare and was registered with GoDaddy. Four more domains suspected of belonging to the same group have been identified.
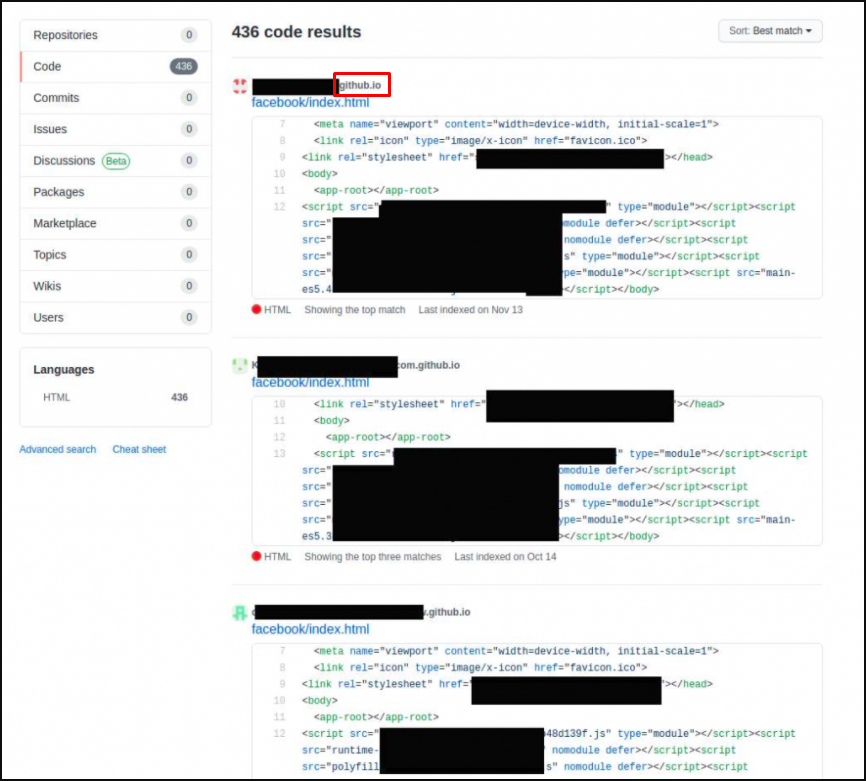
Affected Users
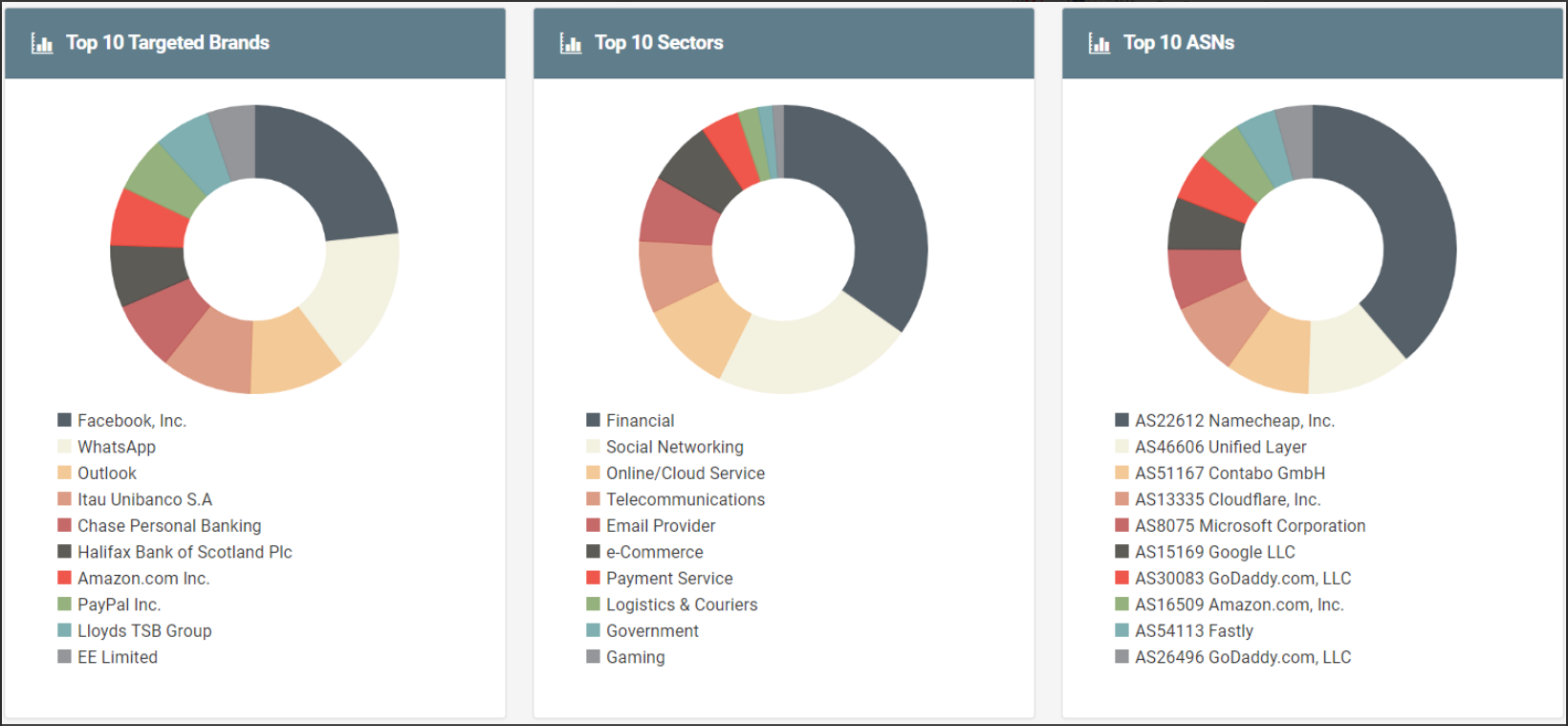
When looking at the credentials stolen with the help of the campaign, it is seen that there are more than 615,000 entries and the list is growing rapidly with more than 100 entries per minute.

Records of more than 50 countries were seen in the leaked data. When the data are analyzed on a country basis, you can see the distribution of the 10 most-affected countries below.

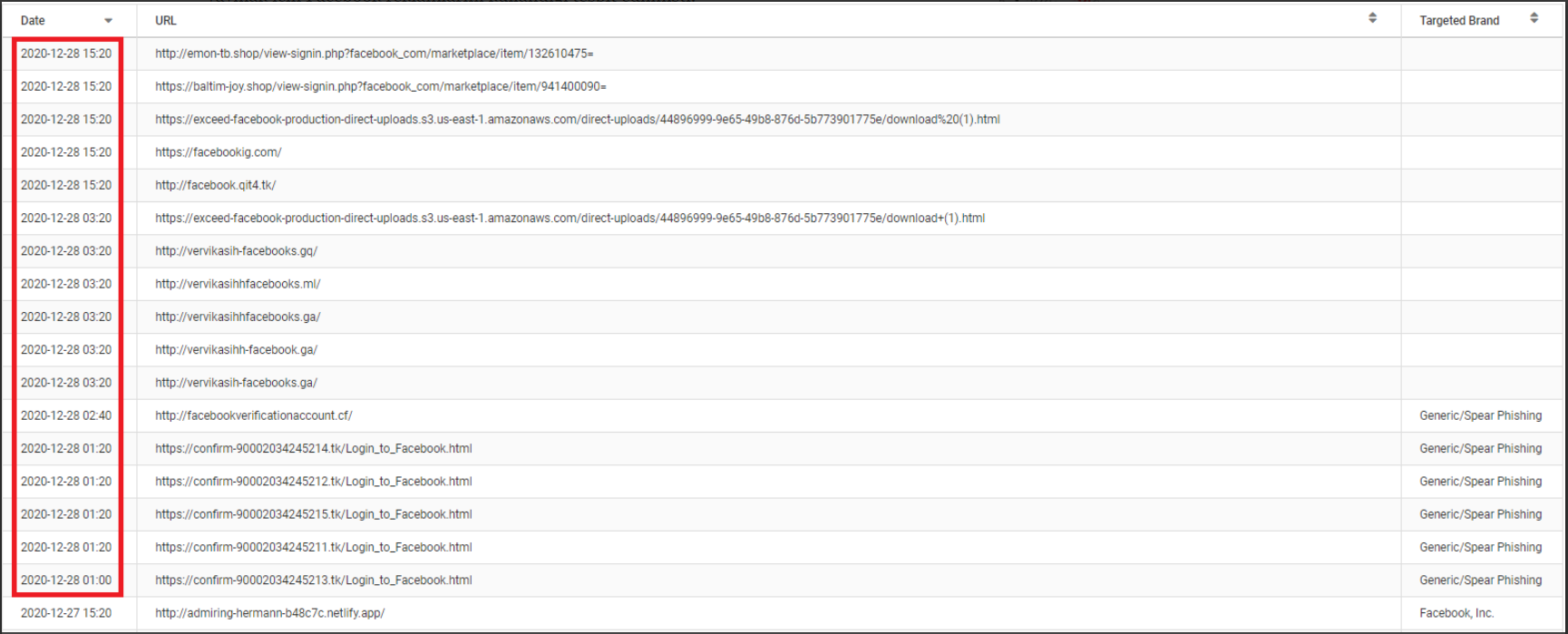
Latest Phishing Activities Detected by Cyberthint
Below are the latest phishing activities detected by Cyberthint, an advanced cyber intelligence product, which enables you to take precautions against cyber threats that may affect your company and employees in cyberspace. In the last 12 hours, 17 phishing operations created by copying only the Facebook login panel have been detected.