This week, Check Point researchers announced a vulnerability in Instagram’s Android and iOS app that would take over the device remotely. With this vulnerability, the attackers can take control of the targeted device with an image created for the victim.
Expressing that they are working with Facebook and Instagram for the vulnerability, Check Point stated in the report they published yesterday that “this vulnerability has turned into a tool that follows Instagram users without their knowledge”.
Upon reporting the vulnerability (CVE-2020-1895) to Facebook, Facebook started investigating the vulnerability via a patch update posted 6 months ago. The updating of Instagram by users has been postponed for now.
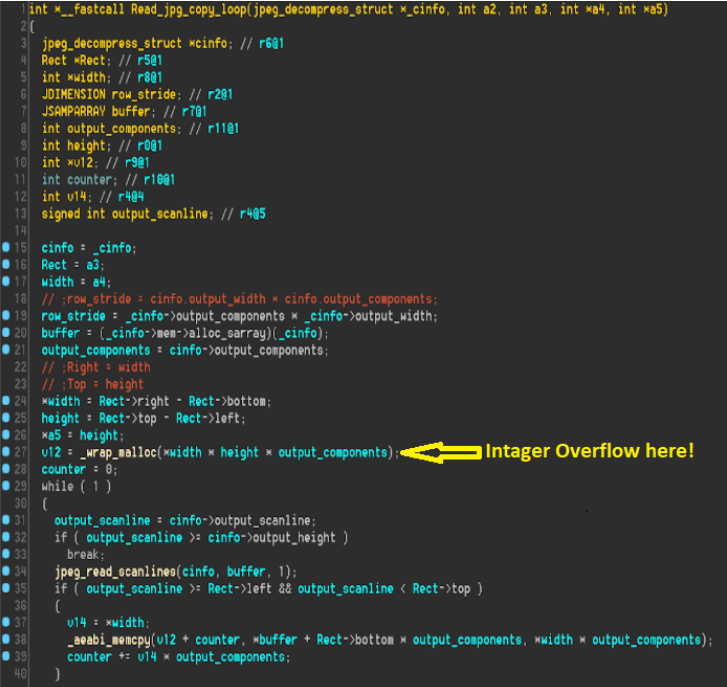
The way the vulnerability works is as follows; A JPEG is sent to the target user via email or WhatsApp. The attack occurs after the target user saves the file on their device and launches the Instagram application.
What Can Be Done With This Vulnerability?
According to Check Point, what can be done with the buffer overflow vulnerability in versions prior to 128.0.0.26.128 is listed as follows. When the user is given extensive permission to access the Instagram app’s camera, contacts, location service, photos, and microphone, the device allows remote code execution that can be used to compromise.
When the vulnerability occurs, the user’s Instagram application can be crashed and becomes unusable unless the application is uninstalled and installed again.
With the vulnerability, they do not only seize the device, they can view the private messages of the target user and delete photos from their account.
How Do We Use Our Phones Safely?
Yaniv Balmas, Head of Check Point Cyber Research, talked about the following security tips for smartphone users. Update! Update! Update! Make sure you update your mobile app and mobile operating systems regularly. Critical security patches are posted every week in these updates, and each of them can have a serious impact on your privacy.
Follow the permissions. Pay more attention to apps asking for permissions.
Think twice about endorsements. Think for a few seconds before confirming anything. Ask yourself the question: “Do I really want to give this application such access, do I really need it?” If the answer is no, DO NOT CONFIRM.
As Systemconf, your security is important to us and we will continue to inform you for your safety.





