Vulmap is an open-source online native vulnerability scanning tool. The vulmap tool was developed by vulmon. It consists of online native vulnerability scanning programs for Windows and Linux operating systems. It can be used for defence and attack. It is possible to make vulnerability assessments using certain scripts. It can also be used by pentesters for authorization elevation.
Vulmap’s main purpose is to retrieve real-time vulnerability data from Vulmon and exploit it, rather than relying on a local vulnerability scanning database. Even the newest vulnerabilities can be detected with this approach. In addition, the exploited feature assists in the privilege escalation processes. Pentester teams can download exploit codes from the command Exploit DB. All that is required to use this feature is the ID of the vulnerabilities.
Since most Linux installations include Python, Vulmap Linux was developed with Python and Vulmap Windows was developed with PowerShell. Vulmap is compatible with Linux, Python 2.x, 3.x and the dpkg package management system. Vulmap is compatible with Windows, PowerShell v3 and above.
Installing Vulmap
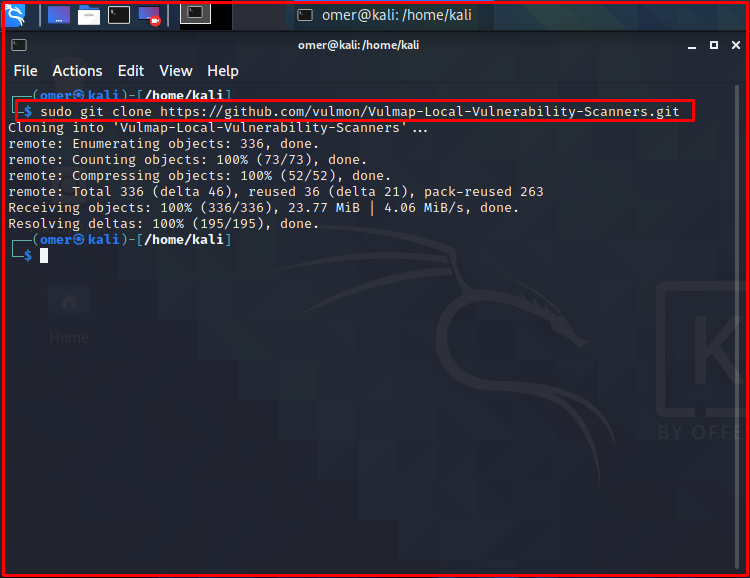
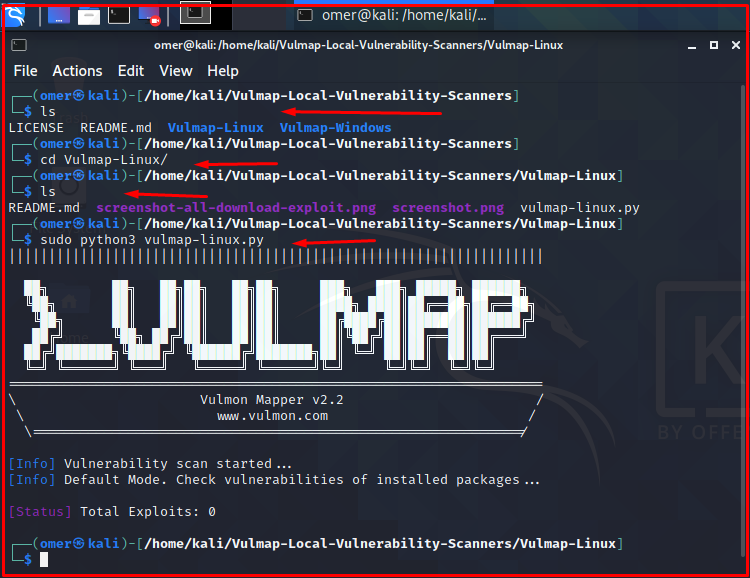
You can use the link below to download Vulmap Linux. After downloading, you can install it.
git clone https://github.com/vulmon/Vulmap-Local-Vulnerability-Scanners.git
python vulmap-linux.py python3 vulmap-linux.py
You can use the link below to download Vulmap for Windows.
https://github.com/vulmon/Vulmap/tree/master/Vulmap-Windows
Run the link below on Powershell during installation.
iex(New-Object Net.WebClient).DownloadString('https://raw.githubusercontent.com/vulmon/Vulmap/master/Vulmap-Windows/vulmap-windows.ps1')

HOW TO USE VULMAP?
Vulmap is very easy to use the tool. The basic options in default mode in Linux are as follows.
-v, –verbose: Used to enable verbose mode and view results in real-time.
-d, –download: Used for downloading. [<exploit_id> is added to download a specific exploit.
-a, –all-download: Used to download all exploits found.
-h, –help: Used to display the help message.
The following commands can be used depending on the process being performed in Windows.
DefaultMode: Scans for vulnerabilities.
DownloadAllExploits: Scans the computer and downloads any exploits that can be found.
OnlyExploitableVulns: Scans for vulnerabilities and only shows vulnerabilities with exploit code.
DownloadExploit: [<exploit_id>]. The exploit ID downloads the specified exploit code.




