One of our essentials in penetration tests is of course searchsploit. He presents the exploits in ExploitDB to us from the terminal and also provides detailed information about the exploits.
Installing Searchsploit on Linux
Although Kali is already available on Linux, you can download it from GitHub to install it on other Linux systems. Finish the setup with the commands below and let’s use it.
Using Searchsploit
-h Parameter
With this parameter, we get information about the other parameters of the searchsploit and what they do.
kali@kali:~$ searchsploit -h
Usage: searchsploit [options] term1 [term2] ... [termN]
==========
Examples
==========
searchsploit afd windows local
searchsploit -t oracle windows
searchsploit -p 39446
searchsploit linux kernel 3.2 --exclude="(PoC)|/dos/"
searchsploit -s Apache Struts 2.0.0
searchsploit linux reverse password
searchsploit -j 55555 | json_pp
For more examples, see the manual: https://www.exploit-db.com/searchsploit
=========
Options
=========
## Search Terms
-c, --case [Term] Perform a case-sensitive search (Default is inSEnsITiVe)
-e, --exact [Term] Perform an EXACT & order match on exploit title (Default is an AND match on each term) [Implies "-t"]
e.g. "WordPress 4.1" would not be detect "WordPress Core 4.1")
-s, --strict Perform a strict search, so input values must exist, disabling fuzzy search for version range
e.g. "1.1" would not be detected in "1.0 < 1.3")
-t, --title [Term] Search JUST the exploit title (Default is title AND the file's path)
--exclude="term" Remove values from results. By using "|" to separate, you can chain multiple values
e.g. --exclude="term1|term2|term3"
## Output
-j, --json [Term] Show result in JSON format
-o, --overflow [Term] Exploit titles are allowed to overflow their columns
-p, --path [EDB-ID] Show the full path to an exploit (and also copies the path to the clipboard if possible)
-v, --verbose Display more information in output
-w, --www [Term] Show URLs to Exploit-DB.com rather than the local path
--id Display the EDB-ID value rather than local path
--colour Disable colour highlighting in search results
## Non-Searching
-m, --mirror [EDB-ID] Mirror (aka copies) an exploit to the current working directory
-x, --examine [EDB-ID] Examine (aka opens) the exploit using $PAGER
## Non-Searching
-h, --help Show this help screen
-u, --update Check for and install any exploitdb package updates (brew, deb & git)
## Automation
--nmap [file.xml] Checks all results in Nmap's XML output with service version
e.g.: nmap [host] -sV -oX file.xml
=======
Notes
=======
* You can use any number of search terms
* By default, search terms are not case-sensitive, ordering is irrelevant, and will search between version ranges
* Use '-c' if you wish to reduce results by case-sensitive searching
* And/Or '-e' if you wish to filter results by using an exact match
* And/Or '-s' if you wish to look for an exact version match
* Use '-t' to exclude the file's path to filter the search results
* Remove false positives (especially when searching using numbers - i.e. versions)
* When using '--nmap', adding '-v' (verbose), it will search for even more combinations
* When updating or displaying help, search terms will be ignored
kali@kali:~$

Simplest Use
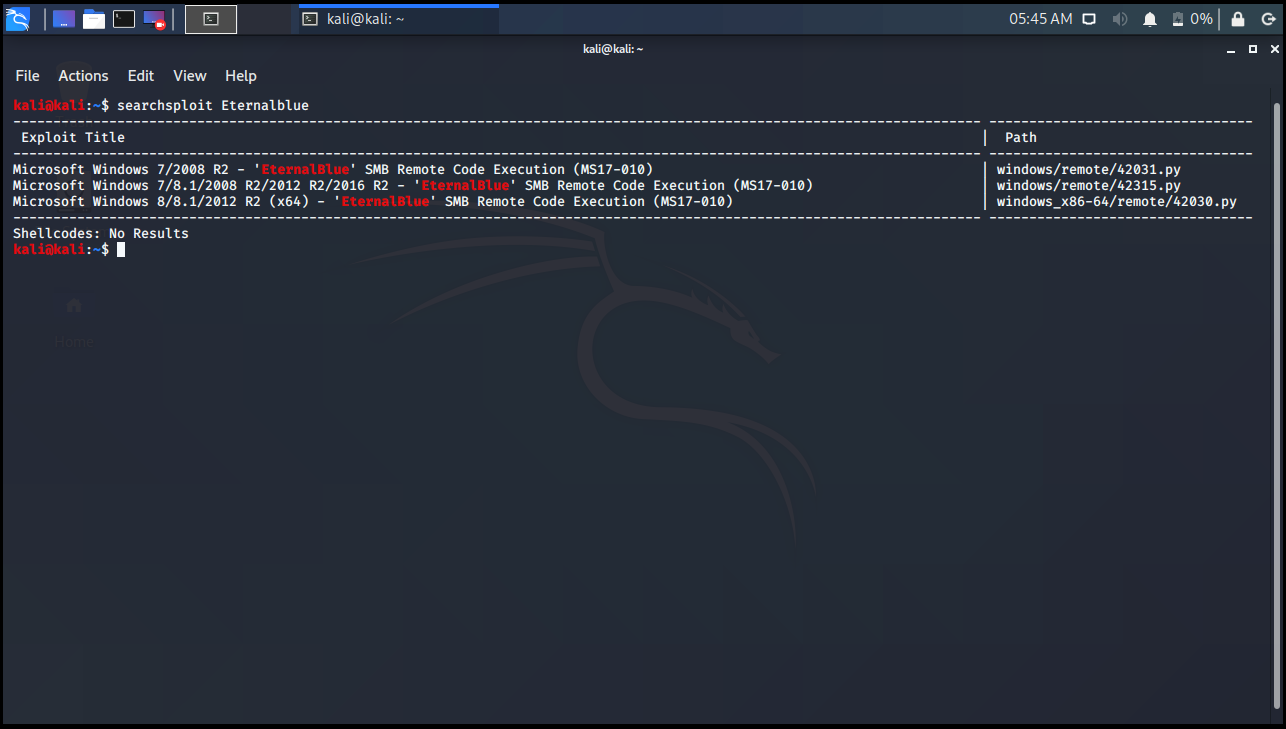
We just need to write the name of the exploit. The first column is the exploit title, the second column is the location of the exploit on our computer.
kali@kali:~$ searchsploit Eternalblue ------------------------------------------------------------------------------------------------------------------------- --------------------------------- Exploit Title | Path ------------------------------------------------------------------------------------------------------------------------- --------------------------------- Microsoft Windows 7/2008 R2 - 'EternalBlue' SMB Remote Code Execution (MS17-010) | windows/remote/42031.py Microsoft Windows 7/8.1/2008 R2/2012 R2/2016 R2 - 'EternalBlue' SMB Remote Code Execution (MS17-010) | windows/remote/42315.py Microsoft Windows 8/8.1/2012 R2 (x64) - 'EternalBlue' SMB Remote Code Execution (MS17-010) | windows_x86-64/remote/42030.py ------------------------------------------------------------------------------------------------------------------------- --------------------------------- Shellcodes: No Results kali@kali:~$
Of course, this may not always look good. If there is an exploit crowd other than the type you are looking for, you can filter it using the grep command.
kali@kali:~$ searchsploit ms17-010 | grep -v '/windows/' ------------------------------------------------------------------------------------------------------------------------- --------------------------------- Exploit Title | Path ------------------------------------------------------------------------------------------------------------------------- --------------------------------- Microsoft Windows - 'EternalRomance'/'EternalSynergy'/'EternalChampion' SMB Remote Code Execution (Metasploit) (MS17-010 | windows/remote/43970.rb Microsoft Windows - SMB Remote Code Execution Scanner (MS17-010) (Metasploit) | windows/dos/41891.rb Microsoft Windows 7/2008 R2 - 'EternalBlue' SMB Remote Code Execution (MS17-010) | windows/remote/42031.py Microsoft Windows 7/8.1/2008 R2/2012 R2/2016 R2 - 'EternalBlue' SMB Remote Code Execution (MS17-010) | windows/remote/42315.py Microsoft Windows 8/8.1/2012 R2 (x64) - 'EternalBlue' SMB Remote Code Execution (MS17-010) | windows_x86-64/remote/42030.py Microsoft Windows Server 2008 R2 (x64) - 'SrvOs2FeaToNt' SMB Remote Code Execution (MS17-010) | windows_x86-64/remote/41987.py ------------------------------------------------------------------------------------------------------------------------- --------------------------------- Shellcodes: No Results kali@kali:~$

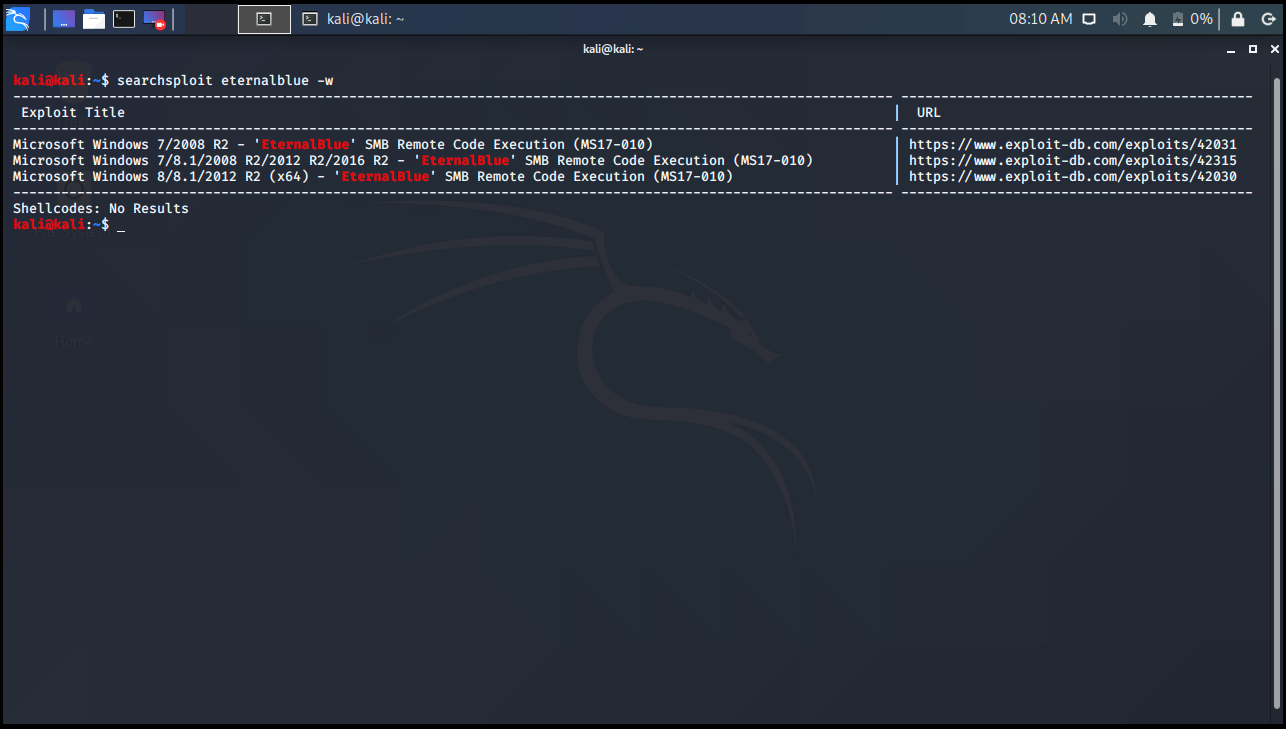
-w Parameter
This parameter gives us the location of the exploit in ExploitDB. For example, the location of the Eternalblue exploit in ExploitDB is as follows.
kali@kali:~$ searchsploit eternalblue -w -------------------------------------------------------------------------------------------------------------- -------------------------------------------- Exploit Title | URL -------------------------------------------------------------------------------------------------------------- -------------------------------------------- Microsoft Windows 7/2008 R2 - 'EternalBlue' SMB Remote Code Execution (MS17-010) | https://www.exploit-db.com/exploits/42031 Microsoft Windows 7/8.1/2008 R2/2012 R2/2016 R2 - 'EternalBlue' SMB Remote Code Execution (MS17-010) | https://www.exploit-db.com/exploits/42315 Microsoft Windows 8/8.1/2012 R2 (x64) - 'EternalBlue' SMB Remote Code Execution (MS17-010) | https://www.exploit-db.com/exploits/42030 -------------------------------------------------------------------------------------------------------------- -------------------------------------------- Shellcodes: No Results kali@kali:~$
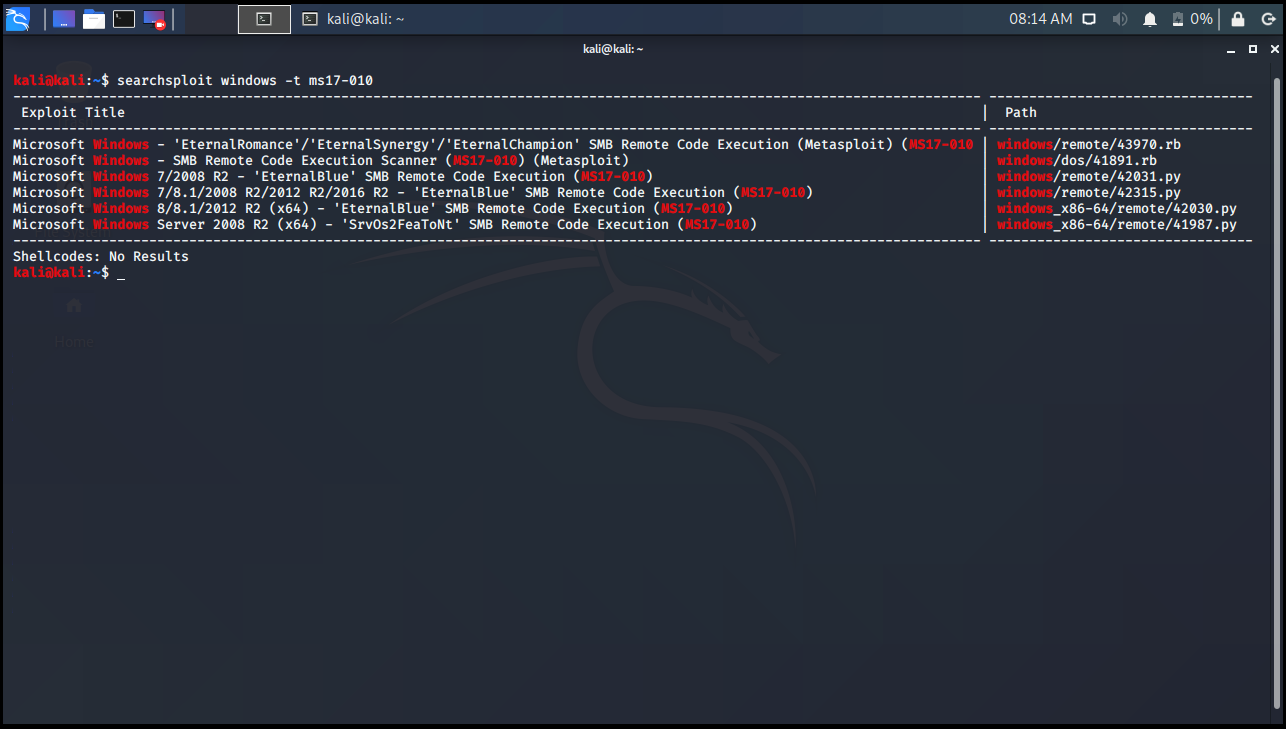
-t Parameter
This parameter allows us to search by exploit title. We will find the exploits named lsass from Windows exploits.
kali@kali:~$ searchsploit windows -t ms17-010 ------------------------------------------------------------------------------------------------------------------------- --------------------------------- Exploit Title | Path ------------------------------------------------------------------------------------------------------------------------- --------------------------------- Microsoft Windows - 'EternalRomance'/'EternalSynergy'/'EternalChampion' SMB Remote Code Execution (Metasploit) (MS17-010 | windows/remote/43970.rb Microsoft Windows - SMB Remote Code Execution Scanner (MS17-010) (Metasploit) | windows/dos/41891.rb Microsoft Windows 7/2008 R2 - 'EternalBlue' SMB Remote Code Execution (MS17-010) | windows/remote/42031.py Microsoft Windows 7/8.1/2008 R2/2012 R2/2016 R2 - 'EternalBlue' SMB Remote Code Execution (MS17-010) | windows/remote/42315.py Microsoft Windows 8/8.1/2012 R2 (x64) - 'EternalBlue' SMB Remote Code Execution (MS17-010) | windows_x86-64/remote/42030.py Microsoft Windows Server 2008 R2 (x64) - 'SrvOs2FeaToNt' SMB Remote Code Execution (MS17-010) | windows_x86-64/remote/41987.py ------------------------------------------------------------------------------------------------------------------------- --------------------------------- Shellcodes: No Results kali@kali:~$
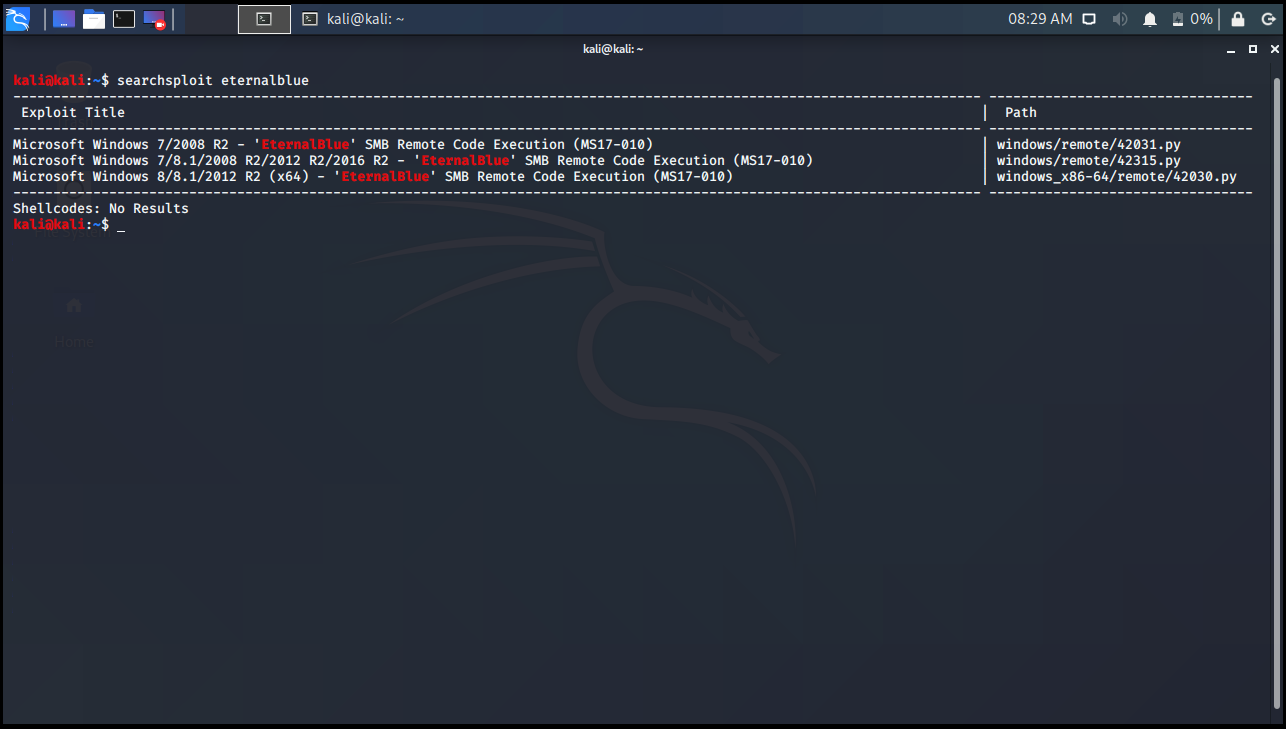
-x Parameter
We can instantly look at the exploit related to this parameter. For example, we can look at the Eternalblue exploit.
kali@kali:~$ searchsploit eternalblue ------------------------------------------------------------------------------------------------------------------------- --------------------------------- Exploit Title | Path ------------------------------------------------------------------------------------------------------------------------- --------------------------------- Microsoft Windows 7/2008 R2 - 'EternalBlue' SMB Remote Code Execution (MS17-010) | windows/remote/42031.py Microsoft Windows 7/8.1/2008 R2/2012 R2/2016 R2 - 'EternalBlue' SMB Remote Code Execution (MS17-010) | windows/remote/42315.py Microsoft Windows 8/8.1/2012 R2 (x64) - 'EternalBlue' SMB Remote Code Execution (MS17-010) | windows_x86-64/remote/42030.py ------------------------------------------------------------------------------------------------------------------------- --------------------------------- Shellcodes: No Results kali@kali:~$
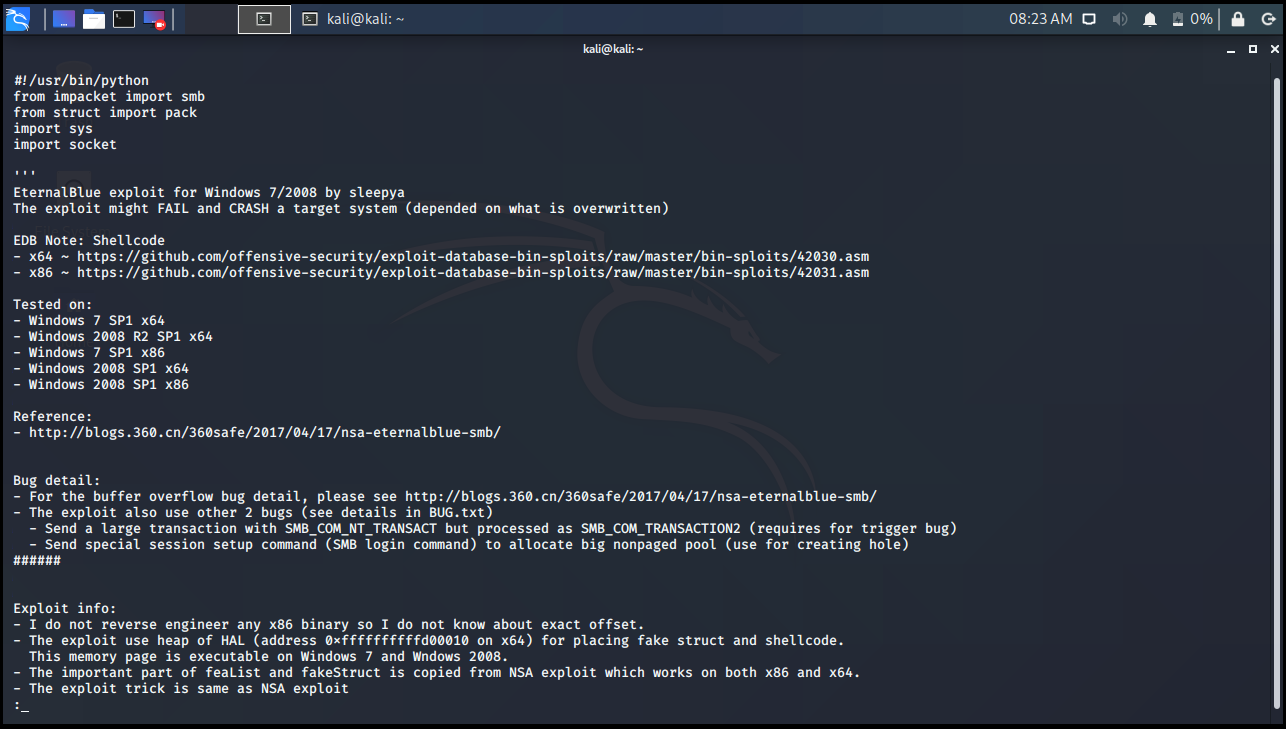
It has given the location of the exploit in the “Path” section on the right. Let’s open the exploit for the -x parameter. We can take a quick look at the exploit before running it in the figure below.
kali@kali:~$ searchsploit -x windows/remote/42031.py
Exploit: Microsoft Windows 7/2008 R2 - 'EternalBlue' SMB Remote Code Execution (MS17-010)
URL: https://www.exploit-db.com/exploits/42031
Path: /usr/share/exploitdb/exploits/windows/remote/42031.py
File Type: Python script, ASCII text executable, with CRLF line terminators
[1]+ Stopped searchsploit -x windows/remote/42031.py
kali@kali:~$
-id -m and -p Parameter
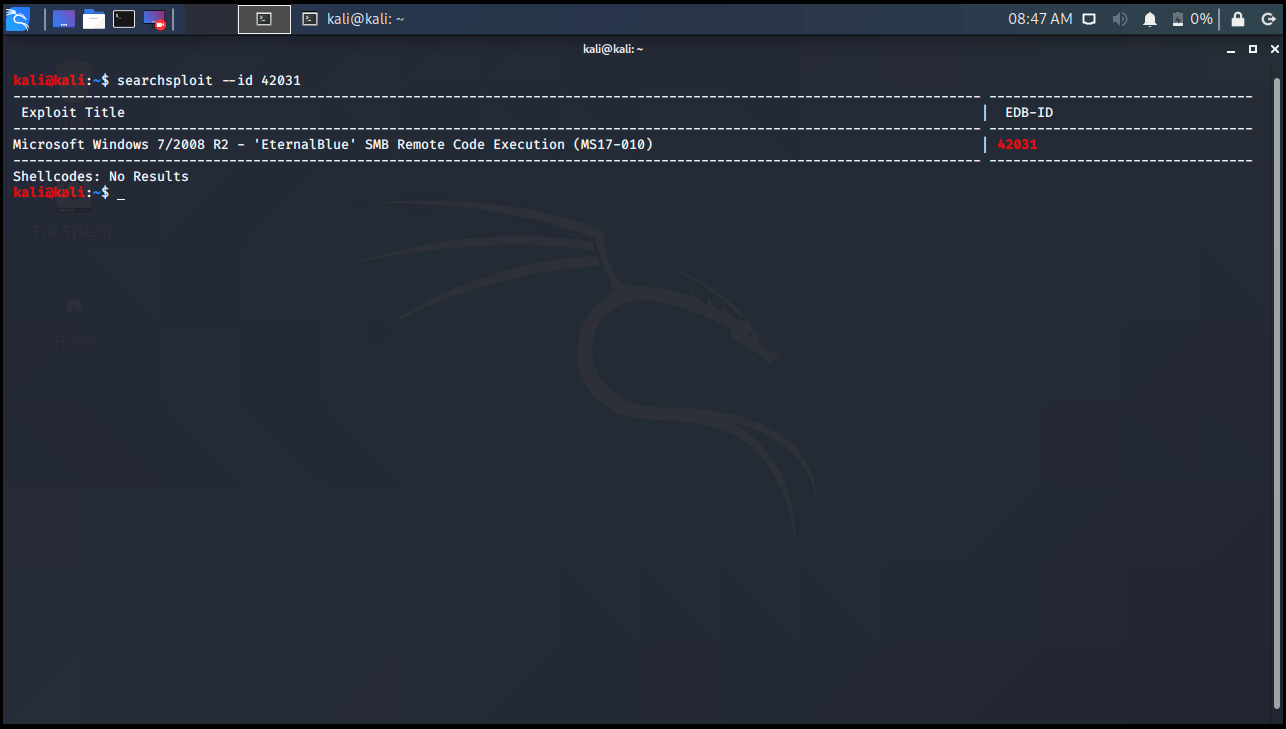
If we look at the main commands, it allows us to find an exploit that we do not know which exploit belongs to, have information about it and then save it in the directory we are in. For example, we have an id and we can search this way first and reach the result we want.
kali@kali:~$ searchsploit --id 42031 ------------------------------------------------------------------------------------------------------------------------- --------------------------------- Exploit Title | EDB-ID ------------------------------------------------------------------------------------------------------------------------- --------------------------------- Microsoft Windows 7/2008 R2 - 'EternalBlue' SMB Remote Code Execution (MS17-010) | 42031 ------------------------------------------------------------------------------------------------------------------------- --------------------------------- Shellcodes: No Results kali@kali:~$
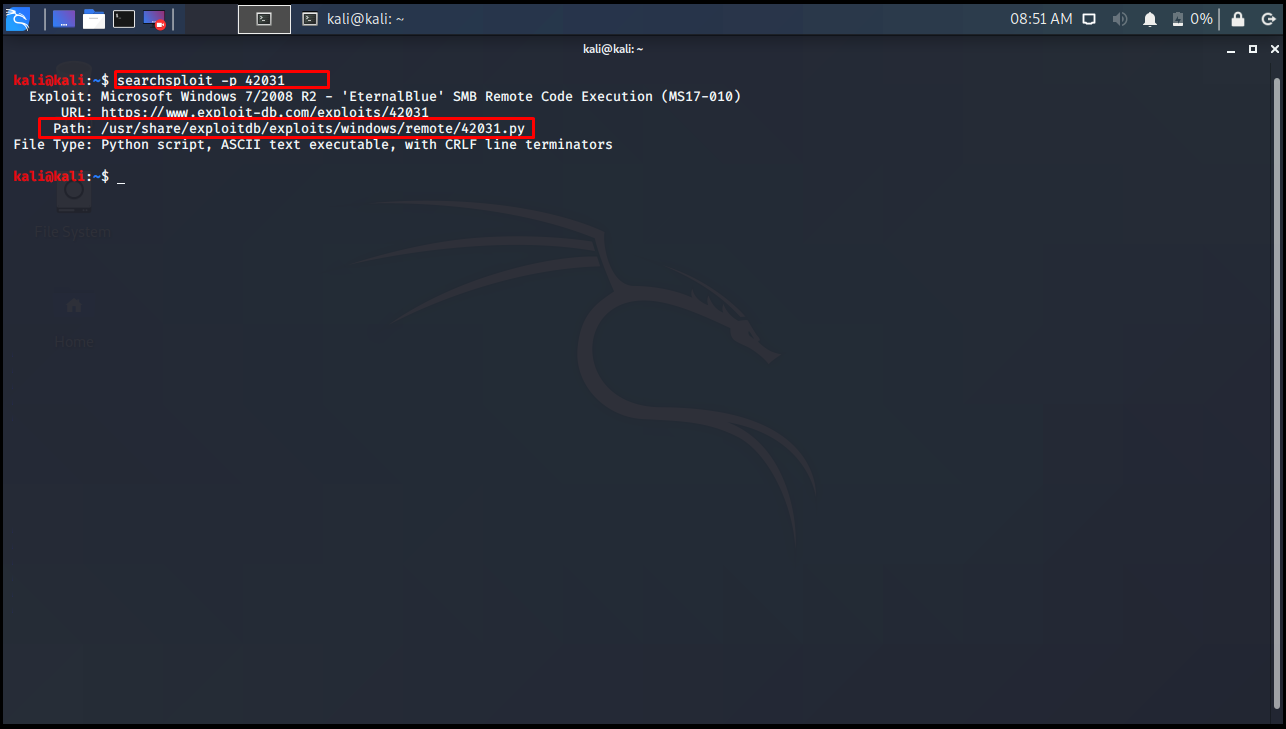
As we understand from the title of Exploit, this exploit is also included in the Metasploit. We will find the Exploit’s location with the parameter searchsploit -p 42031.
kali@kali:~$ searchsploit -p 42031 Exploit: Microsoft Windows 7/2008 R2 - 'EternalBlue' SMB Remote Code Execution (MS17-010) URL: https://www.exploit-db.com/exploits/42031 Path: /usr/share/exploitdb/exploits/windows/remote/42031.py File Type: Python script, ASCII text executable, with CRLF line terminators kali@kali:~$
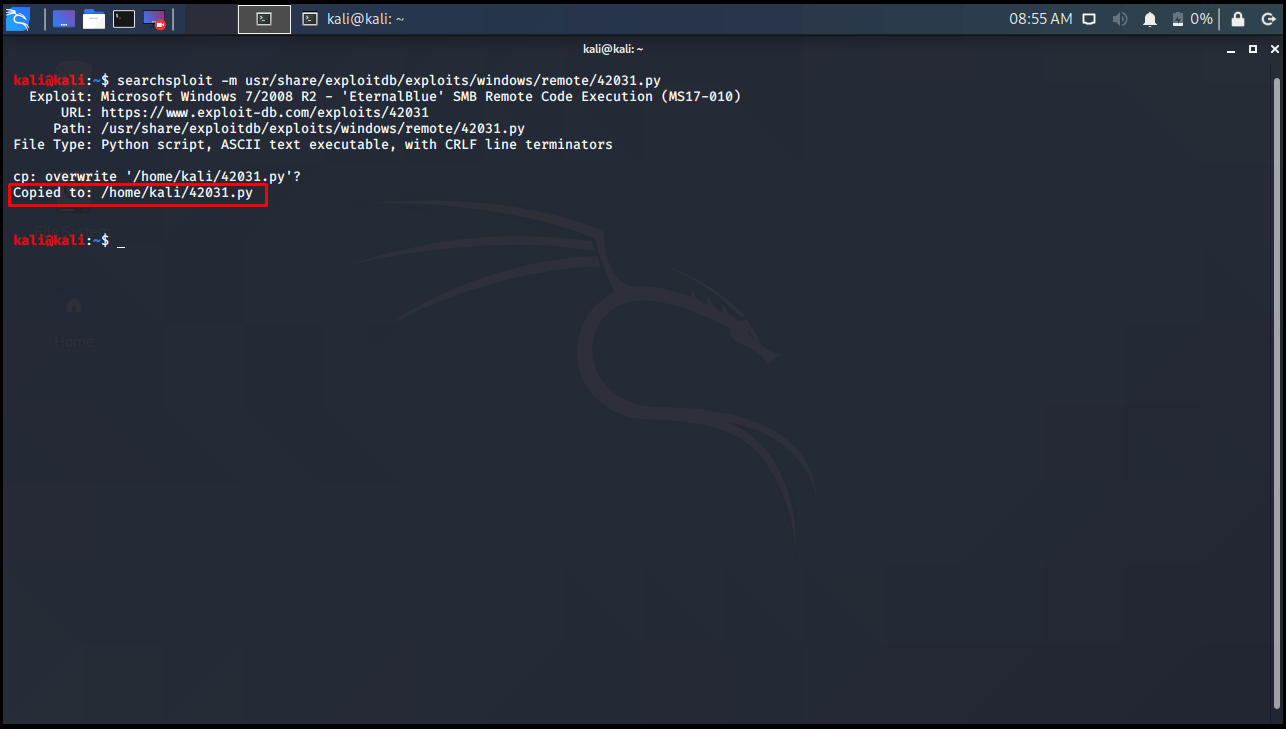
We found its location, now let’s get a copy of the directory where we are.
kali@kali:~$ searchsploit -m usr/share/exploitdb/exploits/windows/remote/42031.py Exploit: Microsoft Windows 7/2008 R2 - 'EternalBlue' SMB Remote Code Execution (MS17-010) URL: https://www.exploit-db.com/exploits/42031 Path: /usr/share/exploitdb/exploits/windows/remote/42031.py File Type: Python script, ASCII text executable, with CRLF line terminators cp: overwrite '/home/kali/42031.py'? Copied to: /home/kali/42031.py kali@kali:~$
-u Parameter
Any new exploit that we need to keep the Searchsploit updated can be helpful. So we need to update it with the -u parameter.
kali@kali:~$ searchsploit -u
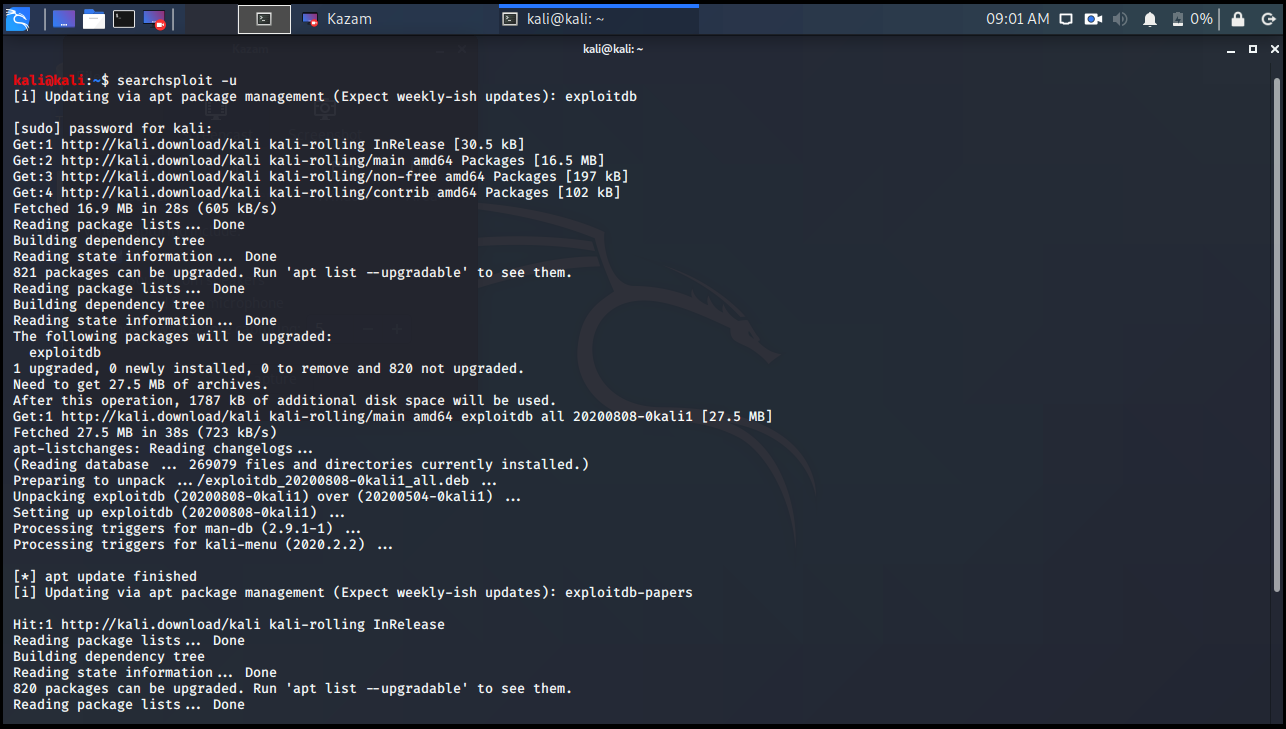
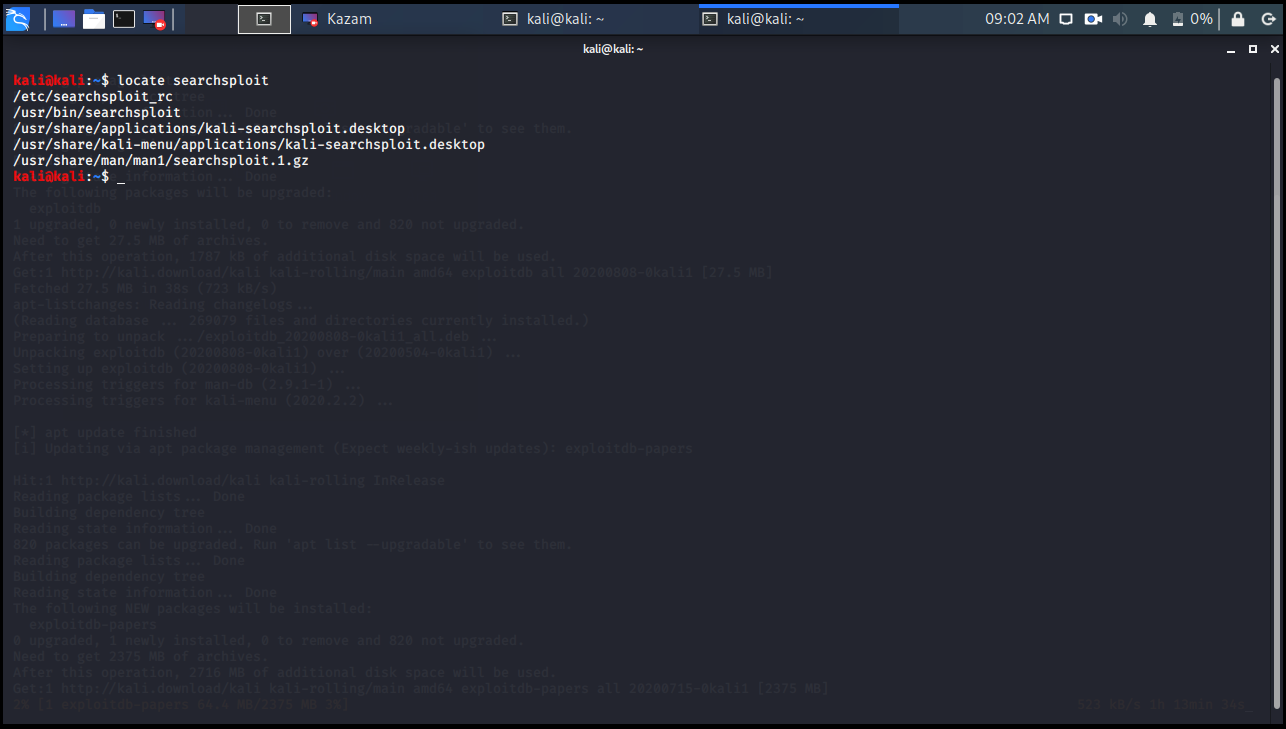
Finally, we can find the location of Searchsploit with the locate command.
kali@kali:~$ locate searchsploit /etc/searchsploit_rc /usr/bin/searchsploit /usr/share/applications/kali-searchsploit.desktop /usr/share/kali-menu/applications/kali-searchsploit.desktop /usr/share/man/man1/searchsploit.1.gz kali@kali:~$




Thanks much Ömer for this well put Tutorial. Cheers!
Thank you G1Testing for your good wishes.