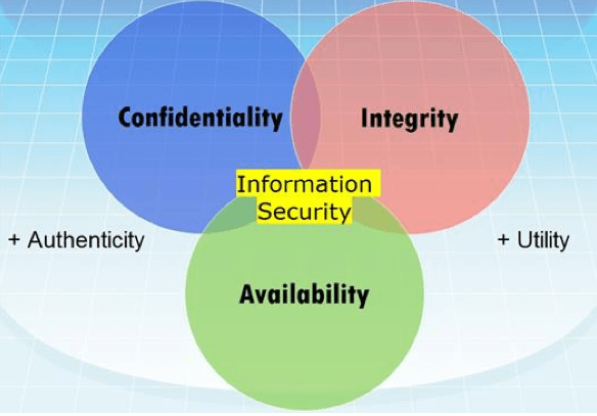
Information security is defined as the prevention of unauthorized or unauthorized access, use, alteration, disclosure, elimination, alteration and damage of information as a type of asset, and consists of three basic elements called “confidentiality”, “integrity” and “accessibility”. it occurs. If any of these three basic security elements are damaged, a security weakness occurs.
Confidentiality: In information security, confidentiality “is the property, that information is not made available or disclosed to unauthorized individuals, entities, or processes.” While similar to “privacy”, the two words aren’t interchangeable. Rather, confidentiality is a component of privacy that implements to protect our data from unauthorized viewers. Examples of confidentiality of electronic data being compromised include laptop theft, password theft, or sensitive emails being sent to the incorrect individuals.
Integrity: In information security, data integrity means maintaining and assuring the accuracy and completeness of data over its entire lifecycle. This means that data cannot be modified in an unauthorized or undetected manner. This is not the same thing as referential integrity in databases, although it can be viewed as a special case of consistency as understood in the classic ACID model of transaction processing. Information security systems typically provide message integrity alongside confidentiality.
Availability: For any information system to serve its purpose, the information must be available when it is needed. This means the computing systems used to store and process the information, the security controls used to protect it, and the communication channels used to access it must be functioning correctly. High availability systems aim to remain available at all times, preventing service disruptions due to power outages, hardware failures, and system upgrades. Ensuring availability also involves preventing denial-of-service attacks, such as a flood of incoming messages to the target system, essentially forcing it to shut down.
Information security coverage
Information security is not just a standard or concept established to prevent third-party information from being captured. In addition to the unauthorized change of information, it is also among the issues that the information security concept deals with, to prevent it from being played on existing information, to target its loss and accessibility when necessary. It is a negative situation in terms of efficiency that the information existing in the company has an accessibility problem. Likewise, access to information provided by unauthorized persons should be considered as a bad scenario.
Information security management system
Information security is a system that ensures the security and integrity of information and allows authorized persons to easily access information when necessary. Abbreviated as ISMS. It is regulated by the international standard ISO 27001: 2013. An organization that fulfils the requirements of this standard has taken an important step towards ensuring the security of the Information assets, which are among the valuable assets.
Performing a job restricted or regulated by law is a non-transferable permit process granted by the public authority so that an attempt can be made.
ISMS(Information Security Management System) is the process of protecting you from unauthorized use of information, unauthorized disclosure, unauthorized destruction, unauthorized modification, damage to information, or blocking unauthorized access to the information. The terms information security, computer security and information insurance are often used interchangeably. These areas are relevant and share common goals in protecting privacy, integrity and accessibility of information.
ISO 27001 Information Security Management System
The Information Security Management System (ISMS) standard covers all types of organizations (for example, commercial organizations, public institutions, non-profit organizations). This standard covers the requirements for establishing, implementing, monitoring, reviewing, maintaining and improving a documented ISMS in the context of all business risks of the organization. It specifies the requirements for performing customized security checks according to the needs of independent organizations or parties.
ISMS is designed to provide adequate and proportionate security controls that protect information assets and rely on interested parties.
Who does ISO 27001 concern?
ISO/IEC 27001 is suitable for all big and small organizations, regardless of which country or sector in the world. This standard is especially necessary for areas where information protection is of paramount importance, such as the finance, healthcare, public and IT sectors.
ISO/IEC 27001 is also very important for organizations that manage information on behalf of others, such as IT subcontractors: it can be used to reassure customers that their information is protected.
Benefits of installing ISO 27001 Information Security Management System
The responsibility for the protection of the information obtained by the institutions belongs to the institution. This information can include a lot of information that identifies the company as well as the personal information of the customers. The fact that important data and information is sold through different channels through cyberpiracy or in different ways or sent directly to competitors affects company image and prestige significantly. In addition, the company becomes legally responsible and legal action can be taken against it. In order not to deal with such situations, measures should be taken to ensure information security.
The organization realizes what information assets it has and its value. It determines the controls and protection methods it will establish and protects it by applying it. It guarantees its business for many years. Also, in case of a disaster, he/she has the ability to continue working. It gains the trust of the related parties since its information will be protected, especially its suppliers. It protects the information through a system and does not leave it to chance. If it evaluates customers, it is better evaluated than its competitors. It increases the motivation of the employees. It prevents legal proceedings and provides high prestige.
How is data security provided?
Organizations may need to improve both within the organization and within the information technologies used to ensure data security. Training of the personnel on information security, measures to prevent the outflow of information and global standards that will create a corporate culture in this direction should be included. Clear lines on who will be responsible for the operation of a number of hierarchies and the leakage of important information within the scope of access to the information within the organization. It is also necessary to take necessary security measures within the scope of information technologies. Comprehensive data security can be ensured by testing that the software and hardware used with security programs are vulnerable.




