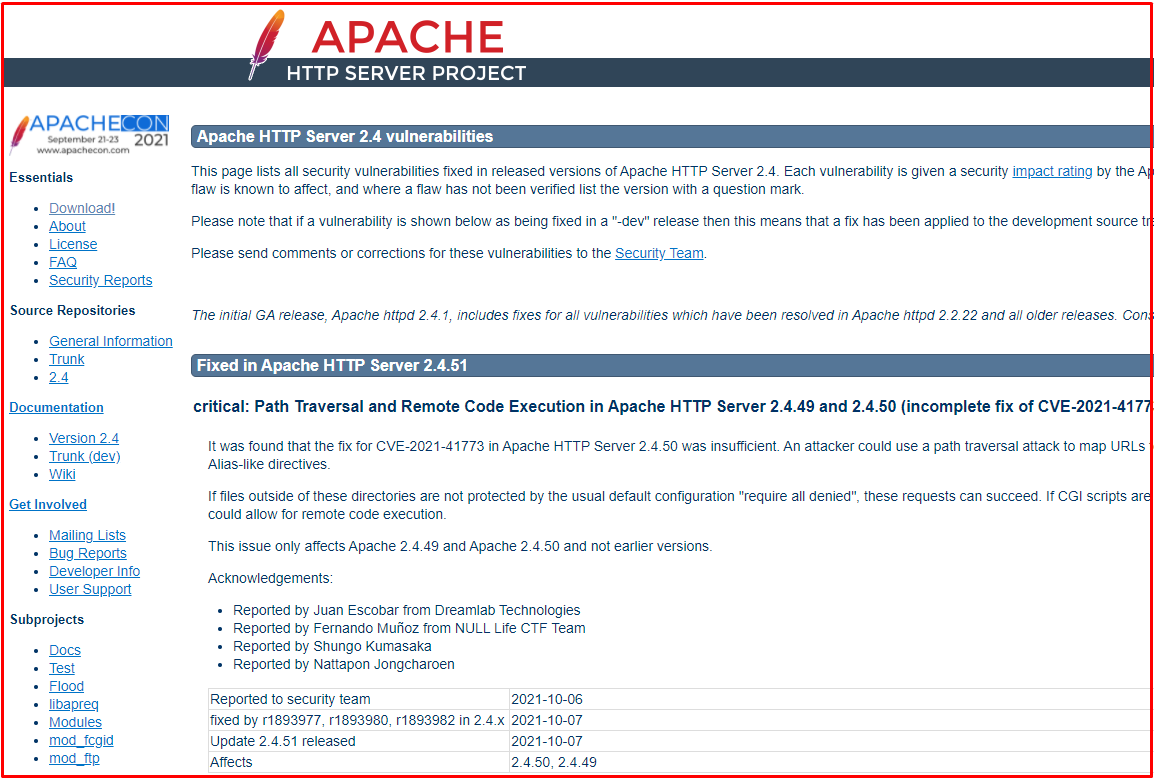
Apache has released updates to Path Traversal and NULL Pointer Dereference vulnerabilities that are known to be actively exploited by threat actors in HTTP Server. The vulnerability, tracked as CVE-2021-41773, is caused by an input validation error in the Path Normalization process. A remote threat actor can send a specially crafted HTTP request to map URLs to files outside the expected document root. These requests can succeed if files outside the document root are not protected by the ”require all denied” function. In addition, this vulnerability can also leak the source of files such as CGI scripts.
Another vulnerability tracked as CVE-2021-41524, exists due to a NULL Pointer Deference error when processing HTTP/2 requests. A remote threat actor can perform a denial of service attack by sending a specially crafted HTTP/2 request to the affected Apache http Server.
Affected Systems
These security vulnerabilities, which are considered to be of high criticality, only affect Apache 2.4.49.
Solution and CVE/CWE
It is recommended that users using vulnerable versions upgrade to Apache HTTP Server 2.4.51, where the vulnerabilities are fixed. You can download and install the updates from the link below.
https://httpd.apache.org/security/vulnerabilities_24.html
CVE/CWE: CVE-2021-41773, CVE-2021-41524
Note: A CVSS score of 3.1 (out of 10) of 7.0-8.9 is considered “high”, and 9.0-10.0 is considered a “critical” vulnerability.
Reference:




