The Trojan virus is similar to the Trojan Horse in case of placement on your computer. Therefore, its other name is Trojan Horse. Trojans are software that looks legitimate but has malicious intent. These viruses gain access to your personal data and perform many harmful actions, such as deleting, modifying, copying, and slowing down your computer performance. Usually, this malware is used by cyber-thieves and hackers.
Trojans are one of the most common categories of malware. But unlike other types of viruses and worms, Trojans cannot reproduce by themselves.

What Trojan Virus Can Do?
Trojans are divided into different classes according to their purposes. The operations that each type can perform on your personal computer are different.
Backdoor creation: Backdoor Trojans allow malicious users to take control of your computer through the Trojan. These usually allow many operations to be performed, including file copying, file receiving, sending, deleting, and viewing your personal data.
Espionage: Some of the Trojans are entities designed to access your personal passwords, bank card information. In addition, Trojans created to spy have the ability to capture your e-mail address and phone number.
Dominating your computer: Some Trojans allow hackers to access all functions on your computer. It is also possible to save your image by accessing your computer’s camera with this virus.
What are the Types of Trojans?
Trojans are classified according to the malicious actions they take on your computer. These;
Backdoor Trojan
It allows such malicious attackers to take complete control of the computer, performing the backdoor creation process. It has the ability to access every process including file deletion, retrieval, viewing, and performance settings of the computer. This highly dangerous Trojan horse settles on your computer to take complete control of your computer.

Exploit
They are malicious programs that contain malicious code that exploit vulnerabilities that are usually found in your operating system and applications.

Rootkit
Rootkits are designed to hide some activities and objects on your computer, thus preventing malicious programs from being detected by security software.

Trojan-DDoS
These types of programs launch serious attacks on target websites. Attack on infected computers will cause the target address to be overloaded. This results in the so-called Denial of Service (DoS) situation.

Trojan-Banker
These viruses, which are designed to steal your personal information about credit and debit card information, online banking systems and e-payment systems, are quite dangerous and common.
Trojan-Downloader
These types of programs download unwanted adware, various viruses and malware programs onto your computer.
Trojan-Dropper
These programs are designed to prevent Trojans from being detected on the computer. Especially rudimentary antivirus programs have difficulty scanning components found in such Trojans.
Trojan-FakeAV
Trojan-FakeAV programs mimic the effectiveness of anti-virus software and thus act with their identity. It is designed to leak money from users by reporting nonexistent threats to users.
Trojan-GameThief
These types of viruses track users who play online games and capture account information.
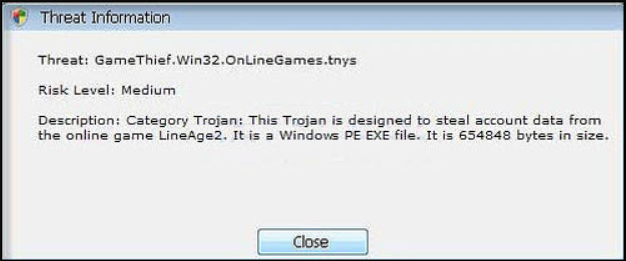
Trojan-IM
They are trojans that steal your login and passwords, especially for messaging applications (MSN, AOL, Yahoo Pager, Skype, etc.)

Trojan-Ransom
Ransom type Trojans alter the data on your computer, causing your computer to malfunction. It also makes the data unusable. Usually, hackers who carry out such attacks demand a ransom to restore the computer.
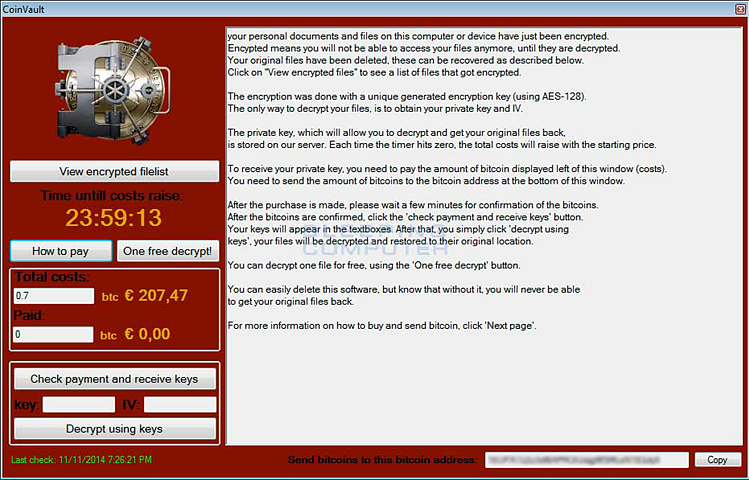
Trojan-SMS
These types of viruses send text messages from your mobile phone to special rate lines, thus causing you to spend money.

Trojan-Spy
Working on the principle of keyloggers, these programs are capable of tracking all the characters you enter using the keyboard. It takes snapshots of your computer and tries to access the programs running on your computer.

Trojan-Mailfinder
These programs have the ability to access all of your mailbox data by collecting mail session information on your computer.

How to Detect a Computer Infected Trojan?
The trojan virus infects not only desktop and laptop computers but also tablets and mobile phones. It is often difficult to detect the trojan virus on the device. Sometimes your device may run slower than its previous performance, showing strange user interface behaviour. This may indicate that there are trojans on the computer.
Trojans cause unexpected and unexpected disk errors on your computer, automatically opening new windows in the system. It also causes the mouse and keyboard to operate by itself, and the computer to turn itself off.
When you notice these changes on your computer, you can review the programs you have installed and search the downloads section of your browser.
How to Clean Trojan Virus?
To ensure the security of the data and programs on the computer, you need to remove the malware on the computer. We’ll usually talk about what to do when you notice malware that can affect system performance and personal data.
Trojan viruses always send your information to another user via an internet connection. If you remove the internet connection, you will be doing the smartest thing to keep your data safe. Now run your computer in safe mode.
When you run your computer in safe mode, all software installed later on your computer is disabled. Therefore, safe mode is the preferred environment to start the cleaning process. After logging into safe mode, delete all unfamiliar software installed on your computer and everything, especially suspicious files, and empty your recycle bin.
Now you will need to find anti-malware software that will scan your computer for malware and install it on your computer. Make sure that your computer does not have an internet connection until you find this software on a different and secure computer and clean it.
After installing the software, scan your computer with the detailed scanning option and delete all the results. Then restart your computer and run a second scan in safe mode. Finally, as soon as you start Windows normally, you can install an anti-malware software again and perform another finish scan.
Changes that occur on your computer are usually due to the files and programs you download. View the programs installed on your computer by selecting “Control Panel> Programs> Programs and Features“. Check if there are unlicensed programs that you think are suspicious by listing the programs by the date they were installed. If there is such a program in the list, you can uninstall it.
Also, if you are a Windows user, enable Windows Defender if not. It is possible to eliminate threats that may arise by scanning for viruses through this wall.
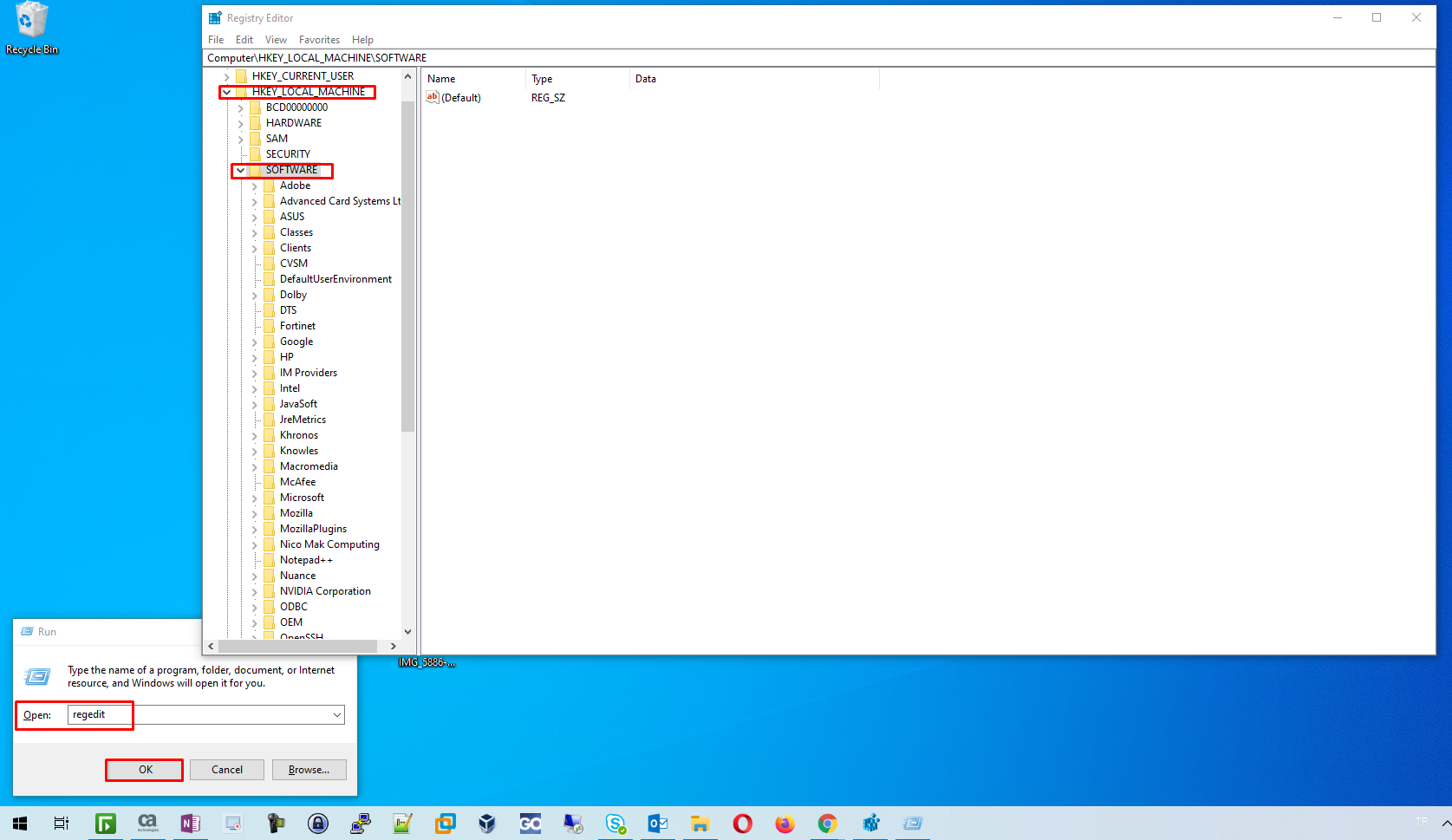
Trojans found on your computer are not always attached to a program. Therefore, you can check the installed files in the registry editor called Registry. First of all, press the “Win + R” keys and type Regedit in the exiting client. You can examine the files you come across by clicking on the “HKEY_LOCAL_MACHINE\ SOFTWARE” file by clicking yes on the screen that appears. You can delete suspicious file names by searching Google for these files.
Protection from Trojan
You can protect yourself from Trojans by always following the security procedures that apply to your computer and using the Internet carefully.
You can protect yourself from Trojans by always following the security procedures that apply to your computer and using the Internet carefully.
- It will be beneficial for your security to follow up and install updates on time by installing reliable anti-virus software. It is also very important for the security of your computer that you regularly scan for viruses.
- It is possible to protect yourself from malicious advertisements and pop-ups by running safe and powerful security plugins for your browser.
- You should keep your operating system’s firewall software updated and active.




