The update released by Microsoft for Exchange Server 2013, Exchange Server 2016 and Exchange Server 2019 servers resolves a very critical security vulnerability. It was announced that this vulnerability was actively and widely exploited.
The information that came after the update released by Microsoft 2 days ago, this vulnerability is mainly in Chinese-based cyberattacks and the U.S. It was used to target their institutions. However, by looking at the data flow in the last 2-3 hours, it contains serious clues that this vulnerability has started to be used by lower-level cyber attackers.
Update Exchange Server
Update your Exchange server urgently. Update the patches below. If for some reason you cannot update, it may be temporary measures to disconnect the Exchange server from the network and ensure that incoming connections to port 443 are only made through VPN. For this attack to be successful, the attackers need to take a few steps, and the first of these steps requires access to port 443 of the Exchange server. If this port is not open to the internet, it can save you time to update.
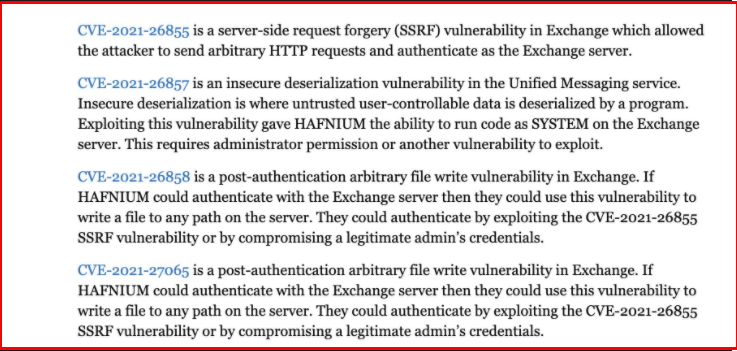
CVE-2021-26855: Exchange Server authentication vulnerability.
CVE-2021-26857: This vulnerability exists in the Unified Messaging Service and allows running malicious codes on the system as SYSTEM. In order to exploit this vulnerability, another daily vulnerability, manager rights, must be gained.
CVE-2021-26858: Attackers who exploit this vulnerability can write files to the paths they want on the exchange.
CVE-2021-27065: Again, like the above vulnerability, attackers can randomly write files on the system.
As a result, if you are using one of the above Exchange versions in your structure, it is very important that you pass the updates without wasting time.
Conditions to Check
The USA. In the warning issued by the Cyber Security and Infrastructure Security Authority, the requests sent to the server by those who try to exploit this vulnerability are stated. If you see these in the connection logs coming to your organization, the vulnerability in your system may be exploited and someone has infiltrated your network. In this case, threat hunting and incident response processes should be activated and the real dimensions of the attack should be revealed.
Reference: https://www.microsoft.com/security/blog/2021/03/02/hafnium-targeting-exchange-servers/




