Announced new vulnerabilities affecting VMware vCenter and ESXi hosts. It was stated that the CVSSv3 score was high, such as vCenter 9.8 critical and ESX-i 8.8 important. VMware thanked Mikhail Klyuchnikov of Positive Technologies for reporting this issue.
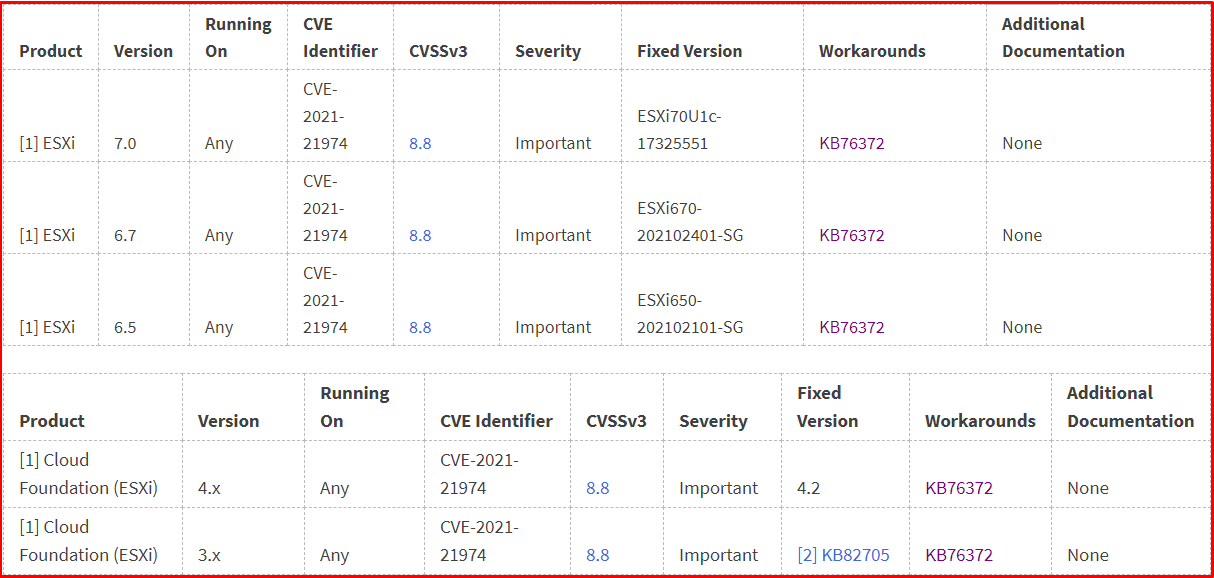
Response Matrix of Affected Systems

Solution for vCenter
The option to install and configure the vRops appliance automatically will be disabled. We connect to the vCSA (vCenter) server with SSH. We go to the file directory as below and back it up.
/etc/vmware/vsphere-ui/compatibility-matrix.xml

Add the following line to this file. We are restarting the “vsphere-ui” service.
<PluginPackage id = "com.vmware.vrops.install" status = "incompatible" />
We are restarting the “vsphere-ui” service.
service-control –restart vsphere-ui

In the vCenter client plugins tab, we can see that vRops client plugins are incompatible.

We need to add the following line to the xml file “C:\ProgramData\VMware \vCenterServer\cfg\vsphere-ui\compatibility-matrix.xml” on Windows-based vCenter servers.
<PluginPackage id = "com.vmware.vrops.install" status = "incompatible" />
To undo these processes, simply remove the line below and run the vCenter interface service again.
<PluginPackage id = "com.vmware.vrops.install" status = "incompatible" />
Reference:
https://www.vmware.com/security/advisories/VMSA-2021-0002.html




