In the current information technology environment, server, application and network devices are monitored by many monitoring applications. Although applications can monitor, monitoring and reporting of the specific Windows security logs we need are essential for security. If the system uses System Center Operations Management (SCOM), the SCOM Audit Collection Service (ACS) role can be used.
SCOM is a Microsoft product commonly used to track the health and performance of server, application and network devices. Audit Collection Services (ACS) is one of the roles offered with SCOM 2007 and continuing with SCOM 2012, SCOM 2016 and SCOM 2019. This role enables security logs to be collected on the server where the SCOM agent is installed, from a central server to the ACS database.
There are three different roles in the ACS structure:
ACS Forwarder
These are the systems that send the audits to the ACS Collector. In short, it is the name given to the systems whose controls we will monitor.
ACS Collector
It is the management server that routes the security records coming from the router machine to the ACS database. By determining which security numbers are to be taken or not, filtering settings are made on the ACS Collector. In the link below, filtering setting and sample made on ACS Collector can be accessed.
SCOM ACS Filter Events
Run at a cmd line as Administrator. This will disable a good collection of meaningless events. A typical large environment will see around 10,000,000 5156 events a day (7 2008 R2 domain controllers) if the Base Filtering Engine service is enabled.
adtadmin /setquery /collector:”Collector Name” /query:”SELECT * FROM AdtsEvent WHERE NOT ((HeaderUser=’SYSTEM’ OR HeaderUser=’LOCAL SERVICE’ OR HeaderUser=’NETWORK SERVICE’) OR (EventId=538 OR EventId=566 OR EventId=672 OR EventId=680) OR (EventId>=541 AND EventId<=547))”
Also
select * from AdtsEvent WHERE NOT (EVENTID=5156 OR EventID=5145 OR EventID=4768 OR EventID=4624 OR EventID=4634 OR EventID=4769 OR EventID=4656 OR EventID=4776 OR EventID=5158 OR EventID=4658 OR EventID=5140 OR EventID=4661 OR EventID=4672)
Note: You must apply registry changes per the below BEFORE running the ACS Query.
The service is configured to run as ‘Network Service’. When trying to set a filter, the service tries to update a registry entry:
HKLM\SYSTEM\CurrentControlSet\services\AdtServer\Parameters
The string that it wants to update is ‘DbQueueQuery’.
The permissions to this registry key do not allow ‘Set Value’. You will need to update the permissions on this registry key to allow ‘Network Service’ the ability to set this registry value.
ACS Database
It is the SQL database where security records will be kept(ACS Database). The ACS structure is shown in the figure below.

Audit records are the records kept as a result of the settings we make under the group policy named Audit.
Security-related settings such as Object Access and Account Logon are usually made under this group policy. For example, by providing all defined servers to transmit security records to ACS, only security-related records can be kept. Settings that can be made in group policy can be accessed from the link below.
Security records; Examples can be given to client A: which users are logged in, which users’ account is locked over which client, which users account has been deleted, which users have been created, which users have logged in incorrectly. Below are examples of queries that can be written in the ACS database.
Note: The following examples are prepared according to the Windows 2008 security registration number.
Example 1
The query and output of the user account locked with security record number 4740 are given below. (Security record query with 4740 id)

The definitions of the objects of the SQL query in security record query 4740 are as follows:
EventMahchine: Domain name of the domain.
CreationTime: The date the user account was locked.
TargetUser: A user name in the domain.
PrimaryDomain: Domain name.
EvenId: Security registration number.
AdtServer.dvAll: All parameters are in ACS database.
String02: Indicates on which client and server the user is locked.
As can be seen in the example above, records such as when and why the account of “abaki” user is locked can be accessed through which client or server
Example 2
The query of how many times the user account is locked with the security registration number 4740 is given below. (Query how many times the user account was locked)


The definitions of the objects of the SQL query are as follows:
TargetUser: A user name in the domain.
EvenId: Security registration number.
Count (AdtServer.dvAll.Id): Crash sum of a user account.
AdtServer.dvAll: All parameters are in ACS database.
Example 3
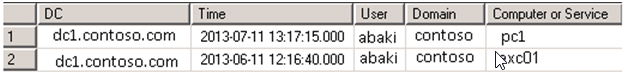
The query with 4624 security registration number and which users login to the server and client are given below. (Query of which users are logged into the client)
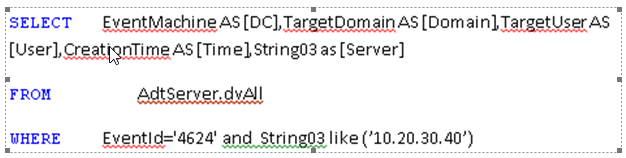

The definitions of the objects of the SQL query are as follows:
EventMahchine: Domain name of the domain.
CreationTime: The date the user account was locked.
TargetUser: A user name in the domain.
TargetDomain: Domain name.
EvenId: Security registration number.
AdtServer.dvAll: All parameters are in ACS database.
String03: IP address of the client or server being logged on.
Example4
Security query number 4726 and SQL query showing which administrators deleted which users and output are given below. (SQL query showing which users administrators deleted.)

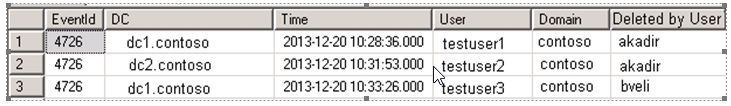
The definitions of the objects of the SQL query are as follows:
EventMahchine: Domain name of the domain.
PrimaryDomain: Domain name.
PrimaryUser: Administrator name that deletes users.
CreationTime: The date the user account was locked.
TargetUser: The deleted user name in the domain.
EvenId: Security registration number.
AdtServer.dvAll: All parameters are in ACS database.
Example 5
The SQL query with 4741 security registration number and its output showing which administrators created which users and its output are given below. (SQL query showing which users the administrator created).


The definitions of the objects of the SQL query are as follows:
EventMahchine: Domain name of the domain.
PrimaryDomain: Domain name.
PrimaryUser: Administrator name that deletes users.
CreationTime: The date the user account was locked.
TargetUser: A user name in the domain.
EvenId: Security registration number.
AdtServer.dvAll: All parameters are in ACS database.
These examples can be duplicated by typing different Windows security registration numbers. The security registration numbers and what they mean can be found at the link below.
http://www.ultimatewindowssecurity.com/securitylog/encyclopedia/default.aspx





Msg 208, Level 16, State 1, Line 1
Invalid object name ‘AdtsEvent’.