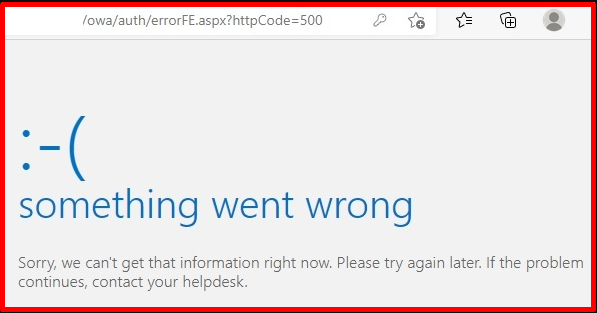
After installing security updates such as “KB5004778” installed on a server running Microsoft Exchange Server, Outlook Web Access (OWA) and Exchange Control Panel (ECP) applications stop working on the server. This error occurs when the security update “User Access Control (UAC)” is enabled but manually installed on a server without elevated permissions. Microsoft has published an article summarizing exactly this. OWA/ECP stops working when your OAuth certificate expires. To solve this problem, do the following.
We run the Exchange Management Shell tool with “run-as-administrator” authority. For this, we run the following command.
Note: Replace systemconf.com with your SMTP domain.
New-ExchangeCertificate -KeySize 2048 -PrivateKeyExportable $true -SubjectName "cn=Microsoft Exchange Server Auth Certificate" -FriendlyName "Microsoft Exchange Server Auth Certificate" -DomainName "systemconf.com"
We note the “thumbprint” information in the output of the command below. We will need this for the next command. Now we run other commands.
Set-AuthConfig -NewCertificateThumbprint "Thumbprint" -NewCertificateEffectiveDate (Get-Date) Set-AuthConfig -PublishCertificate Set-AuthConfig -ClearPreviousCertificate Restart-Service MSExchangeServiceHost Restart-WebAppPool MSExchangeOWAAppPool Restart-WebAppPool MSExchangeECPAppPool
If there is a Load Balance in your environment for the problem of accessing OWA/ECP; when trying to login we get back to the main OWA page. If you have more than one Exchange server, you need to run the following commands on each one. However, you will have to wait for the new Exchange Auth Certificate to be copied to these servers first.
Restart-Service MSExchangeServiceHost Restart-WebAppPool MSExchangeOWAAppPool Restart-WebAppPool MSExchangeECPAppPool
It may take a few hours for this to reproduce, but then everything starts working again. If you want to verify that each server is aware of the new Auth configuration, you can run Get-AuthConfig. With “thumbprint” you can verify that the validity date matches your new certificate and the time you executed the first “Set-AuthConfig” command. If you have a Hybrid Exchange environment, you will need to update these changes in Azure Active Directory.
Get-ExchangeCertificate -thumbprint "Thumbprint" | New-ExchangeCertificate
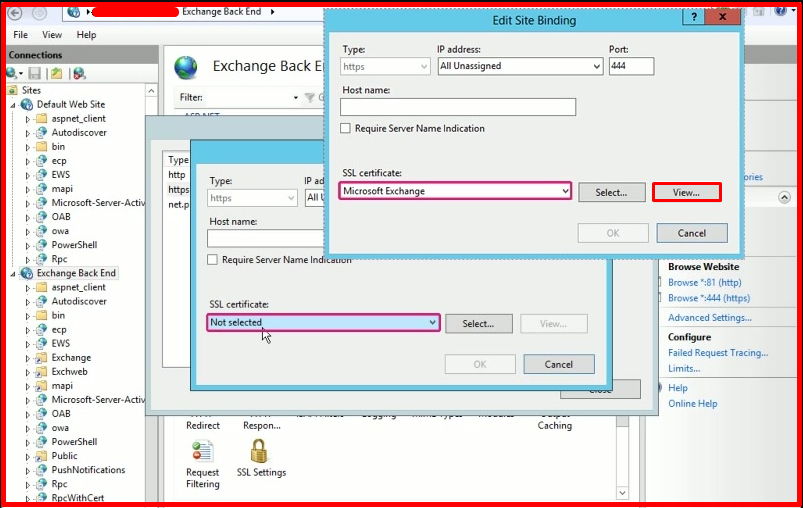
Once this is done, we turn on the IIS service. We’re browsing the “Exchange Back End” site. We choose “Binding”. We change the certificate binding on your Exchange Server by editing the HTTPS binding to use the new certificate. It will have the same name as the old certificate. Therefore, be sure to click the “View” button to see the properties of your certificate. Pay attention to the expiry of the new certificate.