As you use smartphones, you need to know more about the risks that accompany them and take appropriate measures. Smartphones are powerful speakers and distributors that transmit your personal data to the outside. Smartphones are designed as a standard to provide as many connections and social networking services as possible. The reason for this is that your personal information is valuable information that can be compiled, scanned and sold.
IOS
Do Not Jailbreak: This process to liberate iOS and provide more access is called “Jailbreak“. It is not possible to install an app that is not available on the App Store, that is, Apple does not approve, of an Apple device that has not jailbroken. Or it is not possible to access the system files of a device that is not jailbroken. So basically, we can say that jailbreaking is a method used to provide “root” access to the operating system. If you are using an iOS device, you should never do Jailbreak operation. You ask why? Because WikiLeaks has proved that the Jailbreak process has been released by the CIA in the latest information it published and that it was not created by young and enthusiastic hackers, contrary to popular belief.
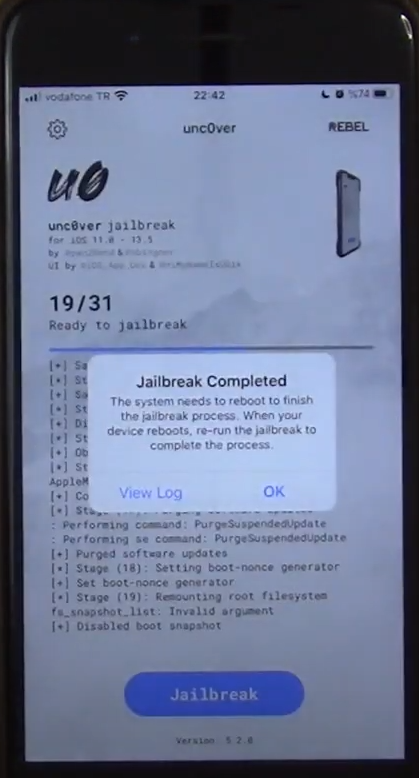
The CIA realized that this is the only way to access iOS devices. All files, emails, photos and videos on your system, your call records, and voice listened to all the time. If this has been done before, you can get rid of harmful applications by installing the latest version of iOS from scratch. There is no other protection method for iOS devices. Because it is seriously difficult to produce viruses and attack the iOS operating system.

ANDROID
Using Passwords: One of the most frequently encountered transactions in the daily life that users waive from their information is not to put a password on the phone. If you do not put a password on your phone, the attacker, who will want to harm you, can easily install the hidden tracking applications he wants on your device.
Not Rooting: The first thing I recommend you do is not to do a root operation. This process, known as rooting the device, is cracking the operating system for full authority on your mobile phone, just like Jailbreak on iOS devices. If your device is rooted, you need to reset it completely to the first one.

Always Keeping the Operating System Updated: iOS, Android or Windows Phone does not matter, regardless of which operating system you are using, be sure to have the latest version. Therefore, you should check whether your device is updated frequently from the version update section.

Storing the IMEI Number: 15-digit serial number or IMEI number (International Mobile Device Code) helps to identify your phone. This code can be accessed by dialing * # 06 # on most phones, by looking at the back of your phone battery or by looking at the phone’s settings. If this code is stolen, it will cause you to deal with any legal actions, including tracing your phone and transferring it to another phone, write down this code and keep it separate from your phone.

Installing Antivirus: You must install an antivirus application. Although RAT applications try to hide in the device, many current antivirus applications can find and delete this malware. Also, try to keep the antivirus application you installed up-to-date. Stay away from sites that distribute paid applications on websites for free. You can anticipate that distributing these applications, which are quite inexpensive and that everyone can buy easily, can be a problem. Never overlook this fact.
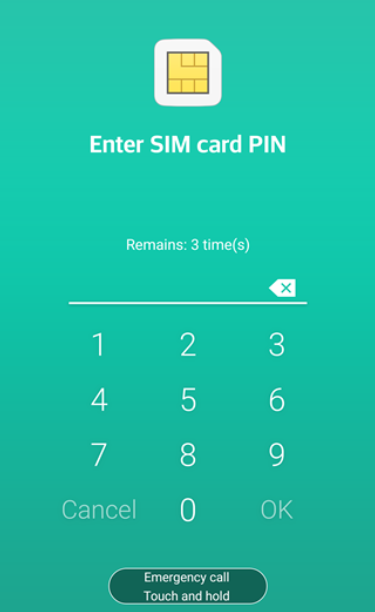
SIM PIN Lock: Always use SIM PIN lock and Device Lock. Whether you know it or not, keep your phone locked in your environment. Sometimes these harmful apps can come to you from your curious friends near you.
Pay Attention to Public Wifi Access Points: Just like when using your computer, be careful when connecting to WiFi access points that do not require passwords with your mobile phone. Mobile phones are basically like computers, and therefore the weaknesses and vulnerabilities of computers and the internet also apply to mobile phones.

Avoiding Applications That You Do Not Know The Source: An average of 520 million virus attacks is detected annually. It turned out that 45 thousand malicious software stolen all the information stored on users’ phones. Therefore, do not get applications through unofficial channels. Thousands of fake APK applications are produced every day and RAT attacks are tried on phones.

Not Storing Sensitive Information in the Phone Memory and SD Card: For example, if you have your credit card information or a photo of your passport, do not store them in external memory. This makes it easier for attackers to access your information.
Not having Phone Repairs Outside an Authorized Service: Only consider using reliable phone dealers and repair shops. This reduces the chances of your information getting into malicious hands when you buy a second-hand phone or have it repaired. Consider getting your phone from an authorized but randomly selected phone vendor so that you can reduce the chance that your phone will be specially prepared for you by installing spyware. Also, your device may have been removed and replaced in a non-original part.




