Continuing Port Scan
SYN scan (-sS):
- Makes a scan by sets the SYN flag.
- SYN scan is a fast scan because only one packet is sent to ports.
- Often used to evade firewall, IPS and does not leave traces in the logs, because three-way handshake not completed.
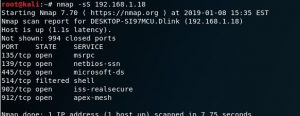
nmap -sS 192.168.1.18
TCP connect scan (-sT):
- Three-way handshake completed.
- Leaves traces in the logs.
- Is a slow scan.
nmap -sT 192.168.1.18
UDP scan (-sU):
- Uses UDP packets.
- Is a slow scan because the three-way handshake not completed.
nmap -sU 192.168.1.18
TCP NULL/FIN/Xmas scan (-sN/-sF/-sX):
- NULL Scan: The packet is sent to the destination without setting flags
- FIN Scan: The packet is sent to the destination by setting the FIN flag,
- Xmas scan: The packet is sent to the destination by setting FIN-URG-PSH flags,
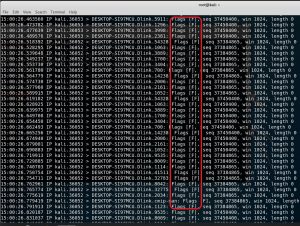
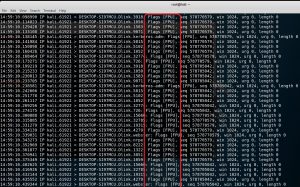
You can see that bits set as in the figure below with tcpdump.
nmap -sN 192.168.1.18

nmap -sF 192.168.1.18
nmap -sX 192.168.1.18
TCP ACK Scan (-sA) :
- Makes a scan by sets ACK flag.
- Used for firewall detection.
nmap -sA 192.168.1.18




