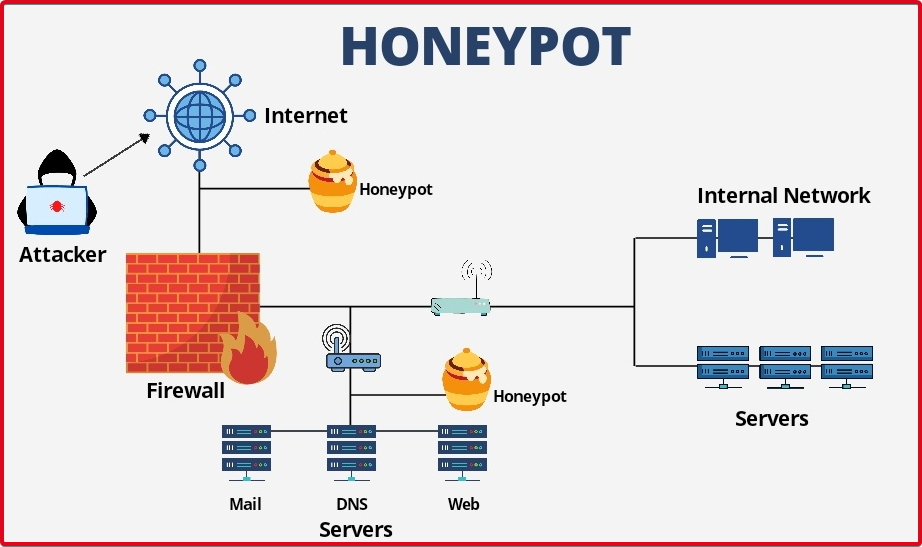
Honeypot; They are decoy servers that are used to gather information about attackers or users who access information systems without authorization. A honeypot can usually be a computer that appears to be part of a network or any server that hosts data. To attackers, it is an isolated resource whose movements are particularly monitored, posing as a target of information or value that could cause them to attack.
Honeypot Types
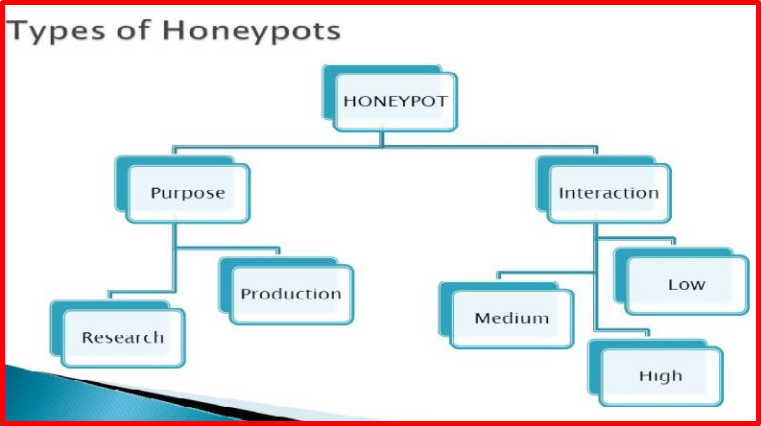
Honeypots are divided into three based on their level of interaction. These;
- Low Interaction Honeypots (Honeyd, Kippo)
- Medium Interactive Honeypots (Dionea, Nepenthes)
- High Interaction Honeypots (Specter)
The risks and benefits of each level of interaction are different; a low level of interaction provides less protection while at the same time low cost. Doesn’t require much training. As the level of interaction increases, the cost and the required education level increase, while the protection increases in direct proportion. It is aimed to keep the benefits and risks of other levels in the middle with honeypots interacting at a relatively medium level, which can be considered the middle of both levels. Honeypots are divided into two according to their intended use. These; Known as Production Honeypots and Research Honeypots.
Production Honeypots
Production honeypots are easy to use. They contain limited information. Production honeypots are generally placed in the production network together with other production servers. Production honeypots are generally low-interaction honeypots that are easier to set up and use. They obtain less information about attacks and attackers than research honeypots.
Research Honeypots
Research honeypots are used to gather information about the purpose and attack tactics of groups of attackers targeting different networks, and to research the threats organizations face and learn how organizations can better protect against these threats. Research honeypots are difficult to set up and maintain. They hold more comprehensive information and are particularly used by military, research, and government agencies.
WORKING LOGIC OF HONEYPOTS
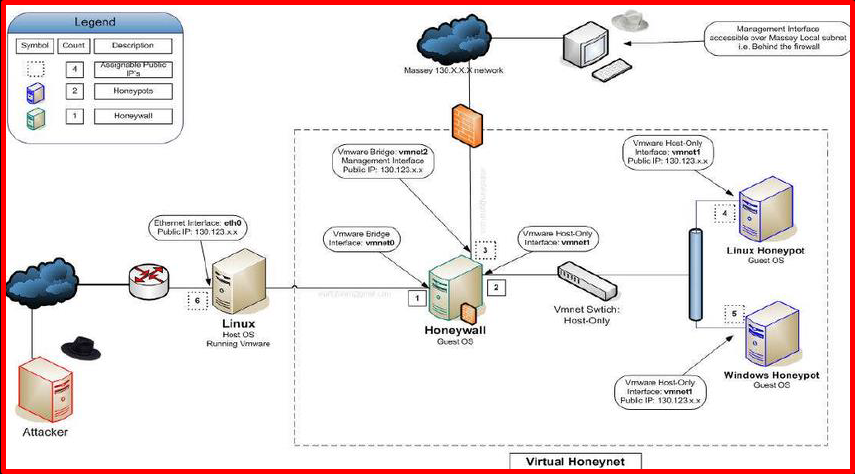
Honeypots do not have complex algorithms, unlike the big works they do. It has a very simple logic. The working logic of honeypots is parallel to the working logic of IDS (Intrusion Detection System) intrusion detection systems. It can show us the log records by analyzing the attacks on the services running on the port we have determined. When the attacker sends an exploit, he can analyze it with the help of antivirus. They can be configured in many ways according to their usage areas. For example, they can even be used to detect spam activity.
Another example is different network structures may exist within a large organization. This can create a vulnerability when an attacker tries to infiltrate a non-honeypot network when he starts to attack. In this, a honeypot network can be established by configuring many honeypots in different networks. Such systems are called HoneyNet.
ADVANTAGES OF HONEYPOTS
- It has low data requirements.
- A single login attempt is sufficient for aggressive behaviour detection.
- It reduces false alarms.
- They analyze and reduce false alarms produced by other measures.
- They increase the detection of missed attacks.
- They detect attackers that other measures miss.
- Encryption/Decryption can detect even if the attacker’s data is encrypted and can be decrypted later.
- Contrary to most security measures, they can work not only on IPv4 but also on IPv6, which is currently in use but will become widespread in the future.
- Low resource use, even at a high cost, unlike other measures, use fewer resources.
DISADVANTAGES OF HONEYPOTS
- If there is only one data entry point, if the attacker understands the situation and never communicates with the honeypots, detection becomes impossible.
- A poorly designed honeypot can contain critical system information and compromise the entire system.




