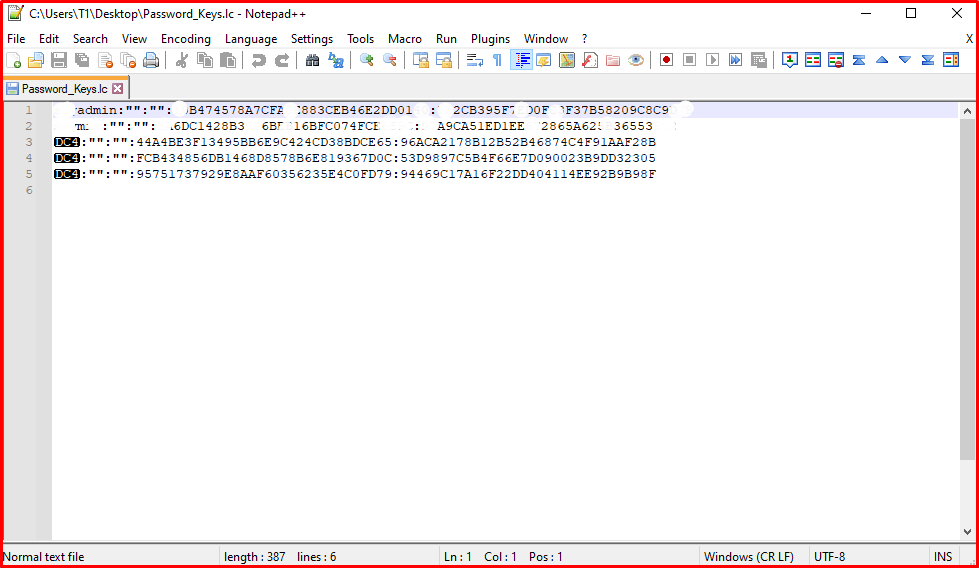
In the Windows operating system, local accounts authenticate via SAM and SYSTEM files. Therefore, the security of SAM and SYSTEM files is critical. The password summaries of local accounts belonging to a Windows computer and registered in the captured SAM and SYSTEM files will be obtained with the Cain&Abel tool.
What is Cain&Abel Tool?
Cain&Abel is a password recovery tool for Microsoft Operating Systems. Its main purpose is the simplified recovery of passwords and credentials from various sources. It uses many different methods, from network sniffing to brute force attacks.
Network listening, dictionary attack, brute-force and cryptanalysis attacks, recording VoIP conversations, decrypting encrypted passwords, recovering wireless network keys and revealing cached passwords are useful for password recovery by various methods.
Extracting Hashes Using the Cain&Abel Tool
SAM and SYSTEM files of a computer named Test1 are located in the C: \ directory of another computer named RedTeam where the Cain & Abel application is installed. We open the Cain&Abel application installed on the RedTeam computer. We will show SAM and SYSTEM files to Cain & Abel application by following the steps of “Cracker> Cracker link on the left panel> Clicking on the empty space on the right panel>” + “icon”.
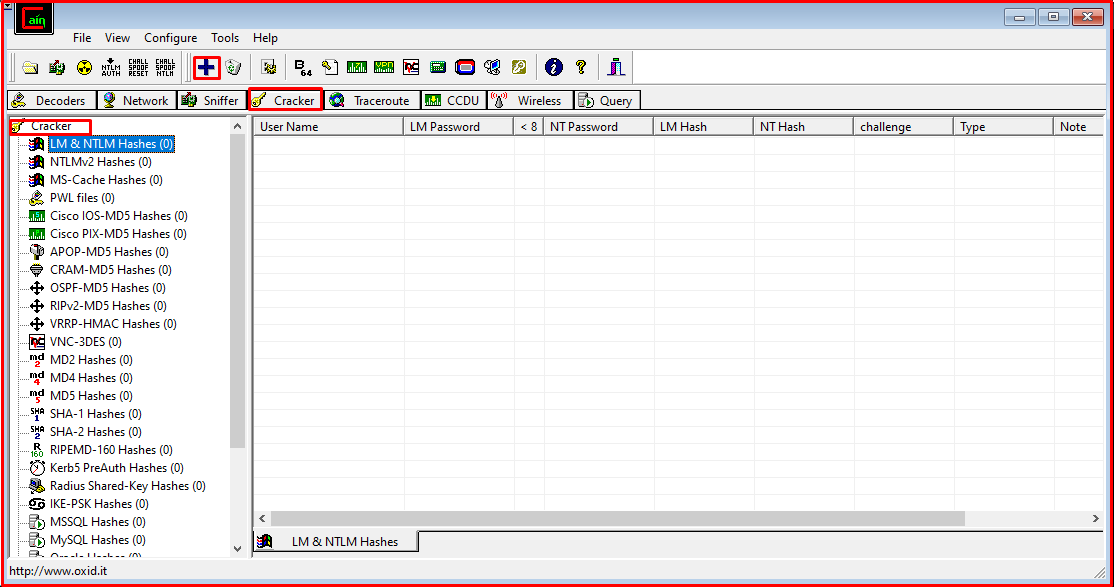
In the window that opens, we will import SAM and SYSTEM files to the application with the “Import Hashes from a SAM database” option. To transfer the SAM database, we select the SAM file in the C:\Desktop directory.
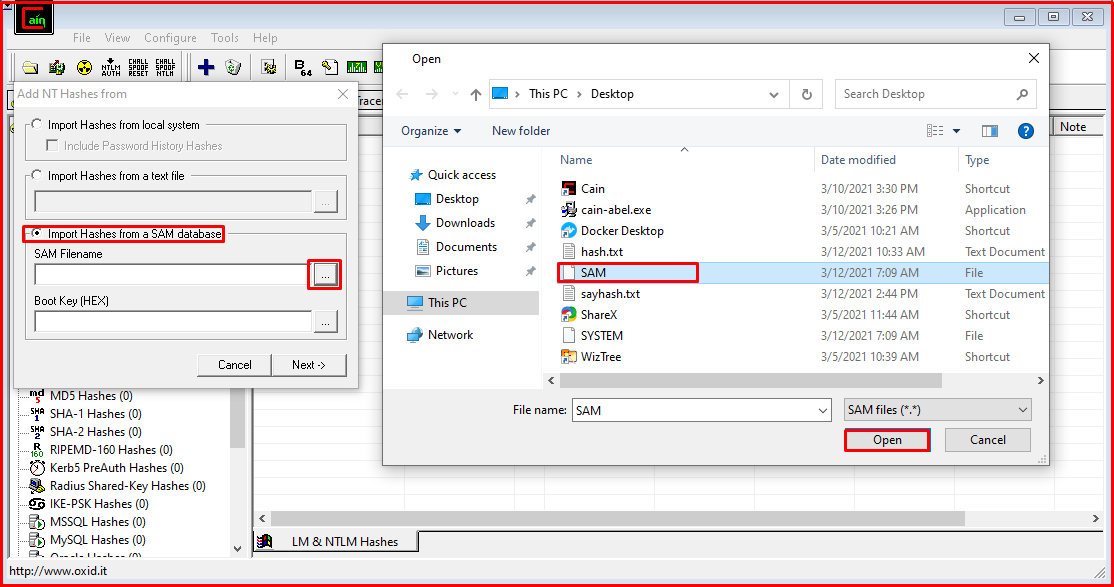
In order to obtain the SYSKEY value, we select the SYSTEM file in the C:\Desktop directory.
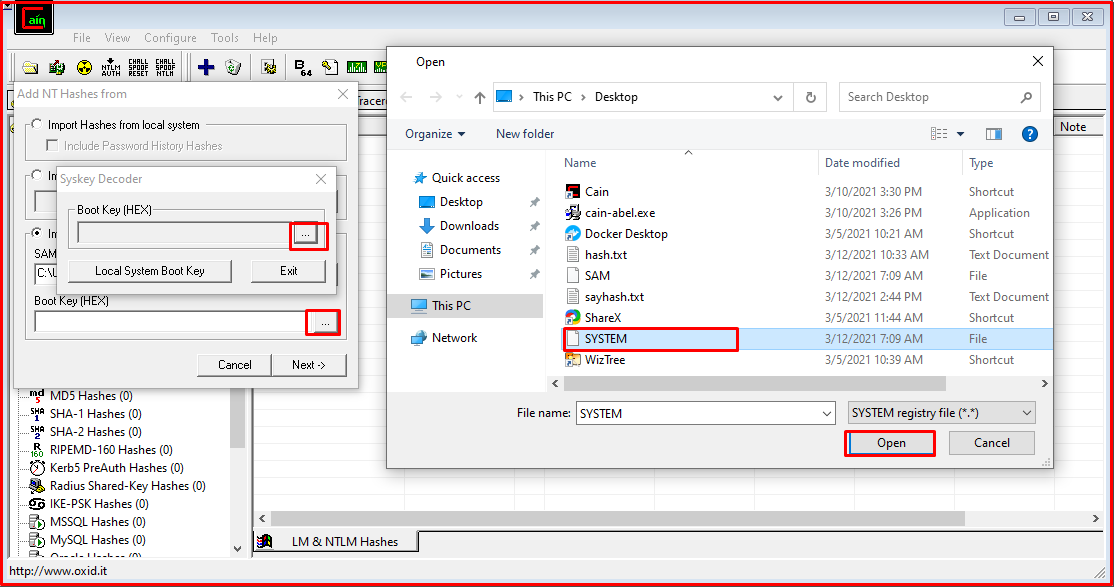
Once the SYSTEM file is selected, we copy the resulting SYSKEY value.
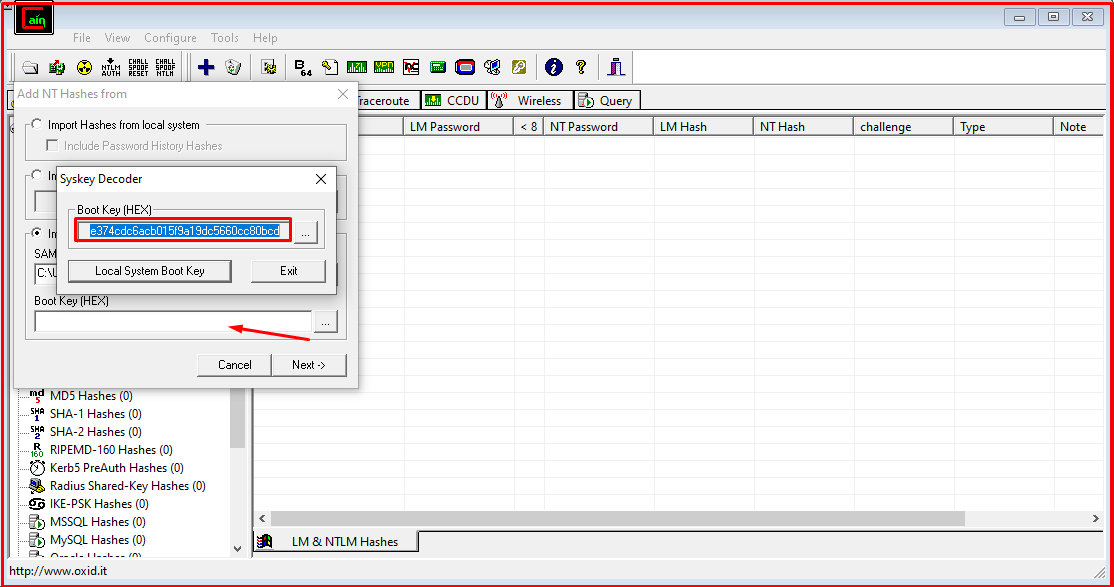
We paste the SYSKEY value that we copied into the text field expressed with “Boot Key (HEX)” and complete the process by clicking the “Next” button.

You will see that the password summaries of the accounts belonging to the Test1 computer from which the SAM and SYSTEM files were taken are listed in the blank area on the right panel.
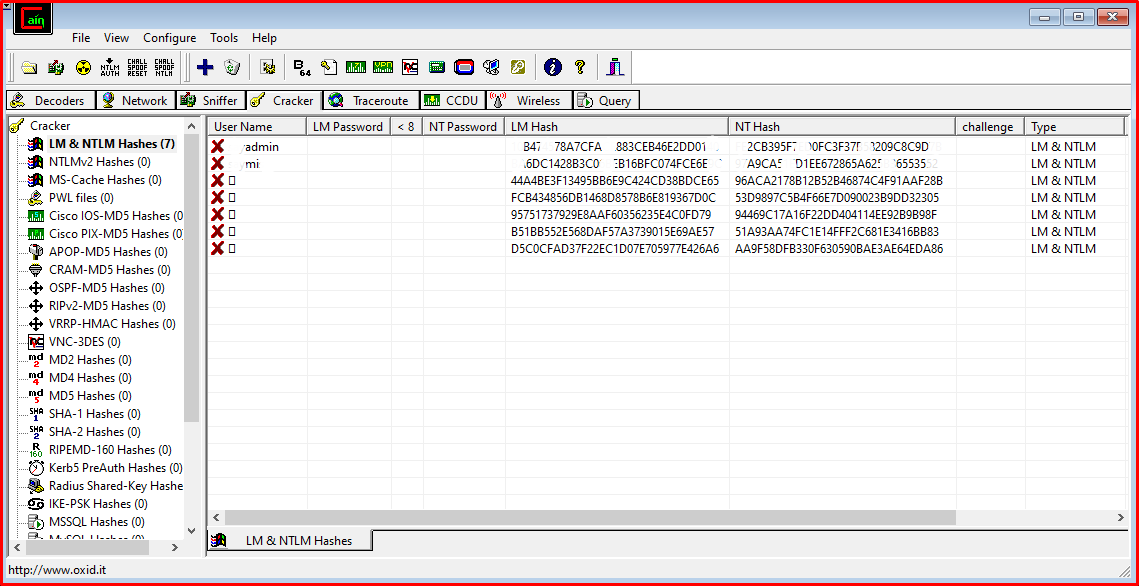
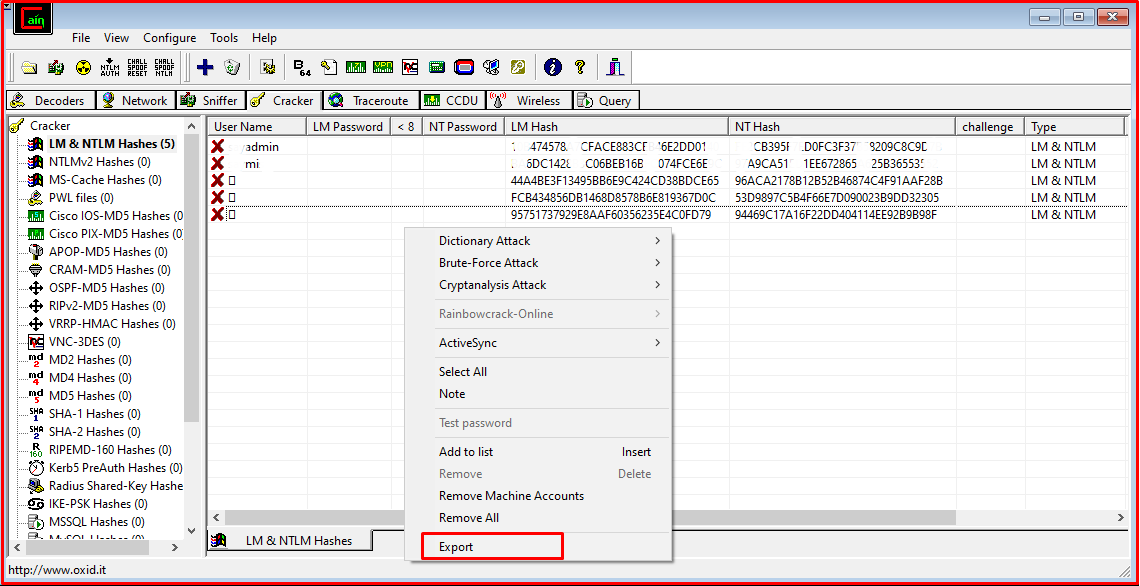
In order to save these data, we perform the “Export” process by right-clicking on the right panel.
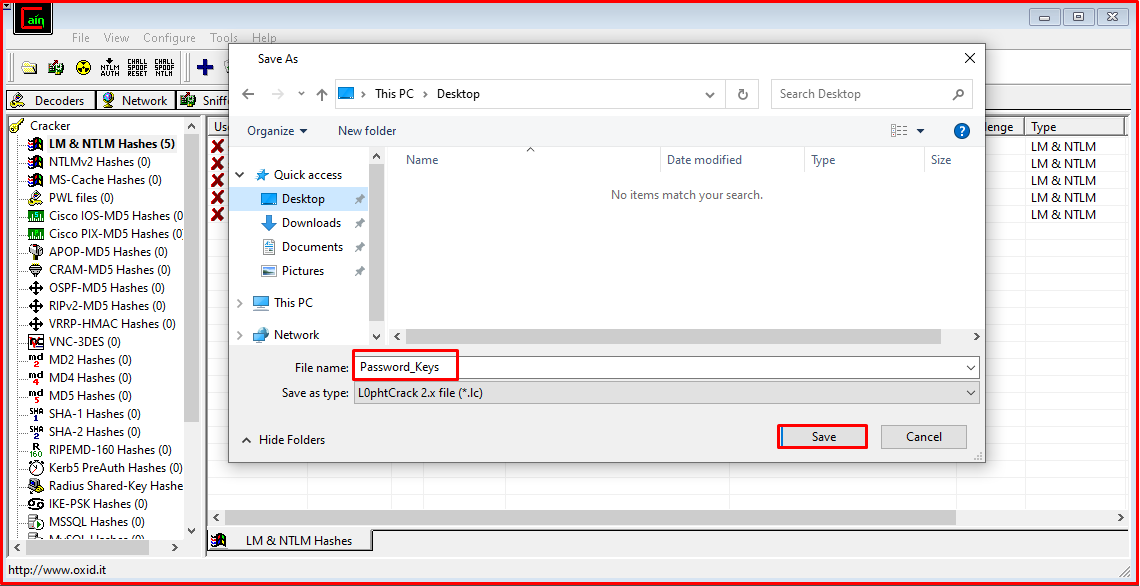
We determine the name and directory of the file be saved.
When we open the password summary file of the accounts of the Test1 computer we exported, it is seen that the credentials are saved.