When we look at the definition of DLP it means Data Loss Prevention or Data Leakage Prevention. With DLP software, you can prevent the unwanted data from getting out of your system or monitor the usage status of the files you specify.
Thanks to the technological possibilities of developing today, access to data has become easier. This situation brings with it the data security problem. A lot of work is being done to classify the data, store it, restrict the users who will access the data, appoint the authorities, and prevent the data from falling into the hands of unwanted third parties.
Why do we need DLP in our institution?
With DLP software, critical data such as employee personal information, pricing reports, R&D reports, financial analysis, budgets, balance sheet information, industry analysis and customer information are safely stored. Thanks to the data loss prevention system, leakage of information and documents outside the institution is prevented. In this respect, DLP software is a must-have system to ensure information security.
You can ask whether the Intrusion Prevention Systems, Antivirus or Firewall mechanisms cannot prevent data leakage or if a DLP system is required. All security layers support Antivirus Intrusion Prevention Systems (IPS), Antibot Blocking Software, Web Security or URL Filtering Solutions, SIEM, MDM and Anomaly Detection software, and other network security software and hardware we do not touch on to prevent Enterprise Data Leakage. The point where DLP leaves is this. Controlling the user in the institution.
In network security, companies often protect themselves from external attacks. We also know the fact that attacks and leaks can happen from the inside, but it is also known to have problems to report or prevent it.
Why invest in DLP product.
Among the motivations that play a role in the emergence of DLP and even becoming a commercial product, the losses that institutions experience due to the leakage of their private/confidential information. In addition, the sanctions of sectoral regulatory organizations forced companies to provide data security. Regulation sanctions such as HIPAA in healthcare, GLBA in finance, BASEL II, Sarbanes-Oxley laws and PCI (Payment Card Industry) Standards play an important role in taking serious steps in information security and thus DLP.
Steps to be taken before starting the DLP project.
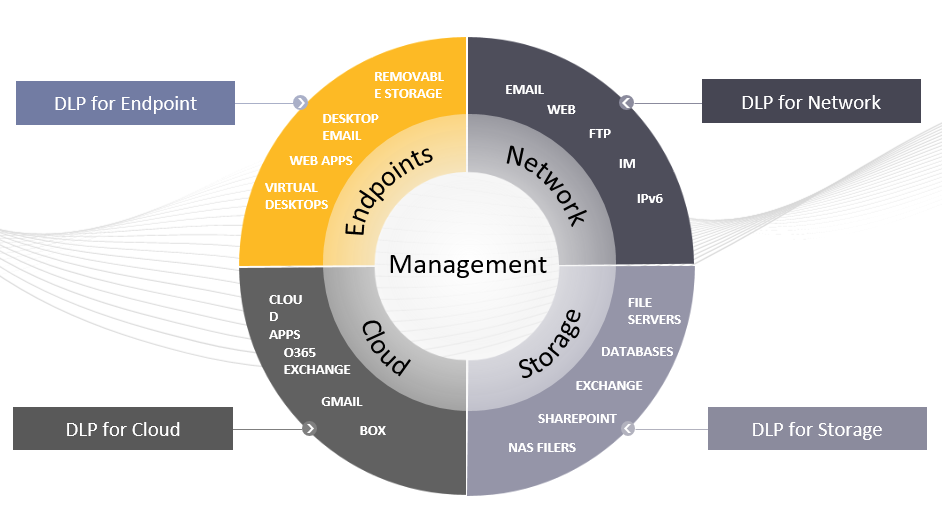
The DLP system technically keeps both the network and the clients under control. Before starting the project, a classification should be made on the critical level of data held in the File system, Databases, Sharepoint, Cloud, Mail server etc. Each internal department should determine the critical order for the data it holds, and then this critical data should be introduced to the DLP system.
Defining Critical Data
DLP does not understand whether a data is critical, we need to define the critical state of the data to the DLP system. So how do you introduce critical data to DLP? There are several methods for this. The keywords we call keyword can be promoted to DLP. These can be added the words you want to check Salary, payroll, top-secret, strategy document etc. When someone sends documents containing these words or makes these correspondences, he immediately comes to the DLP management screen.
Another method is Regex. Especially product numbers, credit card numbers, TC ID No etc. are numbers that have logic in themselves. Many DLP systems have pre-written regexes. It is also possible for the user to write his own Regex.
Drawing documents leaking out with File Type-based control, Database files, zip files, encrypted documents and True File Type etc. an identifier.
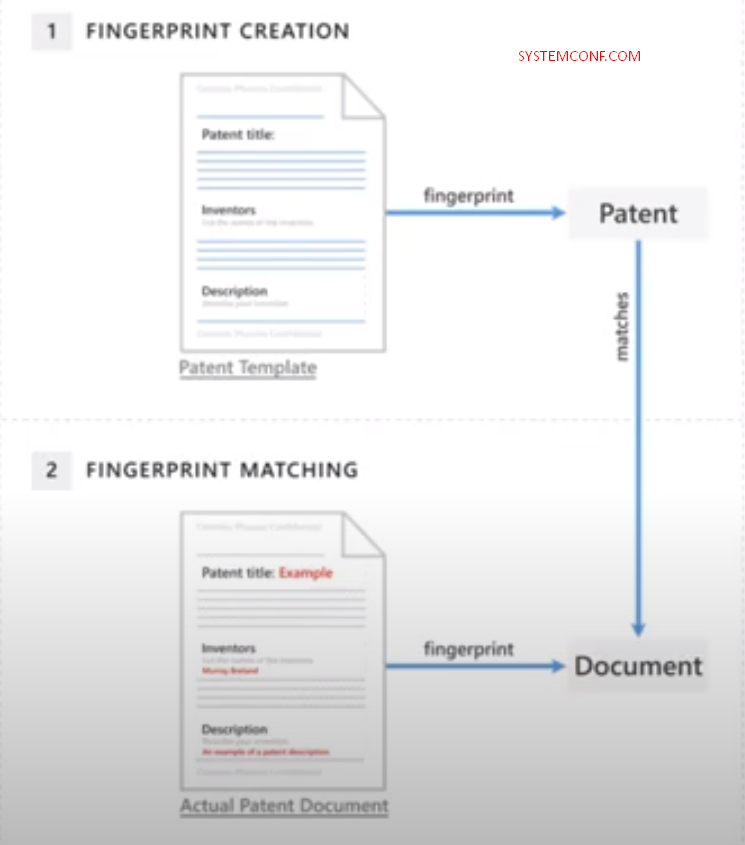
It is the fingerprint technology that makes DLP system DLP. In the File Server, only critical data in a directory accessed by administrators should be introduced to DLP. Or customer information in the institution’s database. How we will mark this information Critically. Here the fingerprint begins here. DLP, which accesses the directory structure with the right of admin, can open each document one by one, analyze the text data, and use a set of conjunctions, which it deems unnecessary in grammar. After ignoring such words and discarding the spaces between words, it starts to get the hash of the document according to a serious mathematical algorithm. The function in fingerprint data is unidirectional. It cannot be reverted from the hash of a fingerprint document to the original document.
Fingerprint technology is excellent, but the area where this technology also has difficulty is file size. So if you are getting the fingerprint of a 10 Gb of data, it’s okay, but it is not as easy as it seems to take the fingerprint of a 10 Terabyte of data and send the information to the clients. Technically, a shadow copy of the data in the Fingerprint Database and the File system is sent to the client. For many DLP systems, this package starts from 100 MB. The load on the system starts to increase as the received fingerprint size increases. Increasing data amount brings together DLP projects that are difficult to control with big data.
Companies must take fingerprints of data of truly Unique value. In other words, while identifying a person, TR identity number is the only value, it is wrong to get the fingerprint of the Date of Birth. Because it can be found in other users belonging to the same date of birth.
For this reason, Machine Learning Algorithm was developed on technology. This algorithm is based on learning, unlike fingerprint. Basically positive and negative samples are introduced to the system. The sample data introduced is for learning the ML algorithm. According to the introduced data, it is a general motivation to make a conclusion about whether the next sent data is critical or not.
What are the Benefits of Data Loss Prevention?
Always be prepared for the practices and audits of institutions regulating the sector, such as the Competition Board. Where the company’s confidential information is stored, to whom it is sent is kept under record. The information that the company and its customers should remain confidential is prevented from leaking and sharing in different places. The company is protected against unexpected internal threats. It is ensured that private users are identified and obtained extra authorizations within the company to reach the desired data and to protect the data from the remaining unauthorized persons.
Some of the DLP products
- Forcepoint
- Symantec
- Digital Guardian
- McAfee DLP Endpoint
- Sophos
- Cisco IronPort
- Websense DLP
- TrendMicro DLP
- Check Point DLP Software Blade
- Trustwave
- Panda Security
Below is the diagram prepared by Gartner for DLP products. (Magic Quadrant)





